"Perfectly tailored to our needs, Arsen's training modules are quick, easy to complete, and well-integrated with our existing stack."
97%
of decision-makers say more training and awareness help reduce cyberattacks
2024 Security Awareness and Training
71%
of employees complete only a one-off cybersecurity training session, instead of receiving continuous, ongoing training
The Annual Cybersecurity Attitudes and Behaviors Report 2025
89%
of organizations view social engineering as the top cybersecurity threat, making it a key focus for training
SANS 2024 Security Awareness Report

Train in less than 5 minutes
Our modules are time-efficient, to the point, and prioritize efficiency to protect your business productivity.
- Less than 5 minutes per month to complete
- Answer control questions in one click
- Friction-less: no need to log into an elearning platform

Ensure seamless compliance with all leading industry frameworks
From ISO 27001 to SOC2 or your cyber-insurance, our content and reports will allow you to become or stay compliant with the most popular frameworks, and prove it.
- Modules based on NIST and ANSSI recommendations & best-practices
- Engagement tracking with proof of completion
- Export complete reports instantly—download or integrate through our API

Frictionless: embed Arsen into the tools your team already knows
Arsen's awareness has been built to fit into your employee's current workflow. They don't need to create an account or log into a different platform, they can learn while using your existing stack.
- Deliver modules via
Microsoft Teams,
Slack or email
- Trigger phishing simulations based on elearning behavior
- Connect to our API to integrate with your current reporting tools
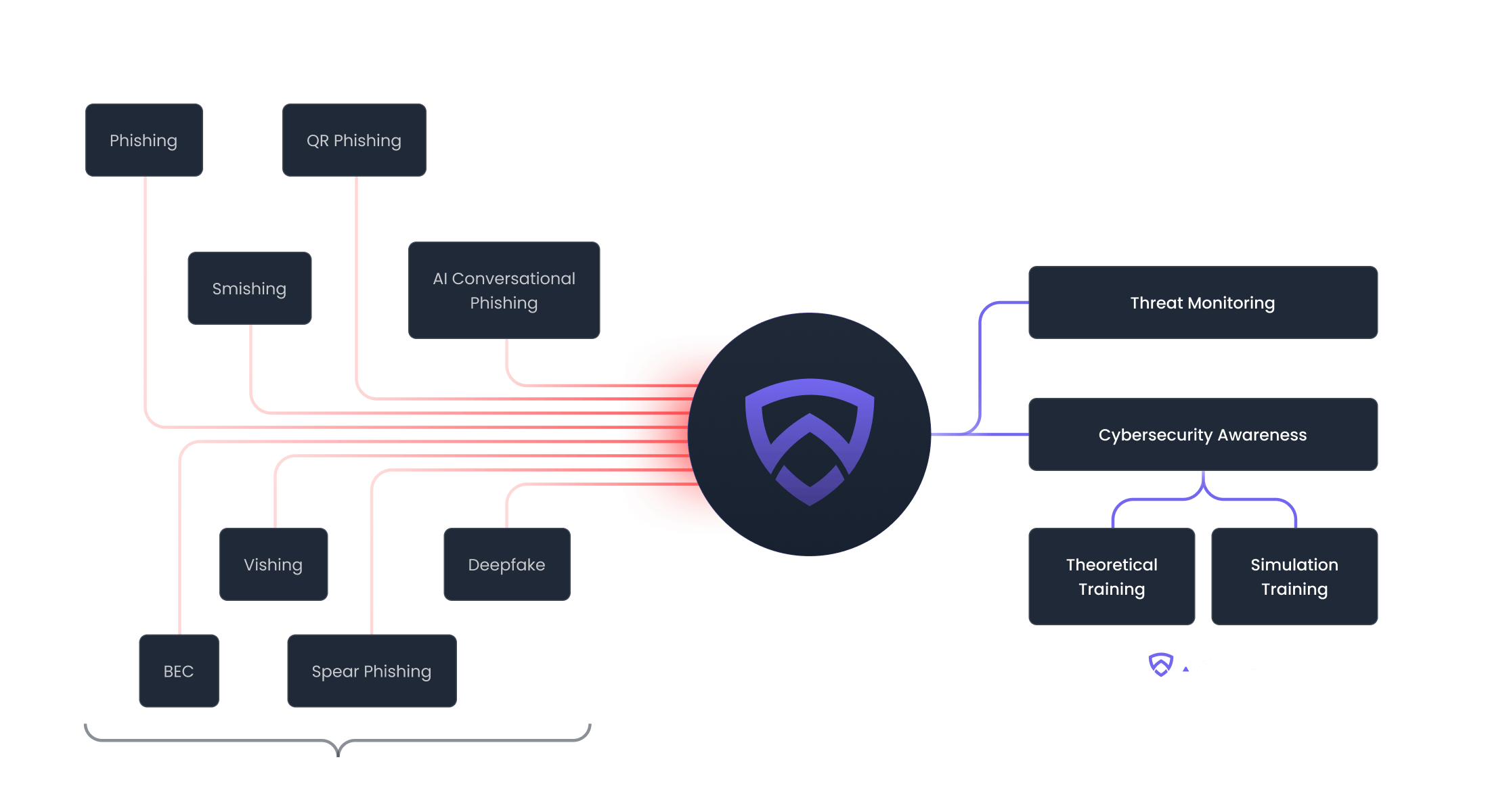
Protecting your business from every angle
Replicate real-world threats like advanced phishing, BEC, smishing, and vishing attacks to keep your employees aware and empowered to take action against threats.
Trusted by 500+ organizations worldwide
Empowering the best cybersecurity teams
Helps organizations meet regulatory requirements and industry standards
"Phishing campaigns are a key element of my awareness plan. Tracking employees on Arsen is simple and easy. The variety of scenarios is a real advantage in the long term."

Sophie Dubois
CISO"Thanks to Arsen, I can quickly and regularly test our employees, confront them with realistic attack simulations, and track results in real-time."