Arsen Security Blog
AI-Powered Social Engineering in Financial Services: What Every CISO Needs to Know in 2026
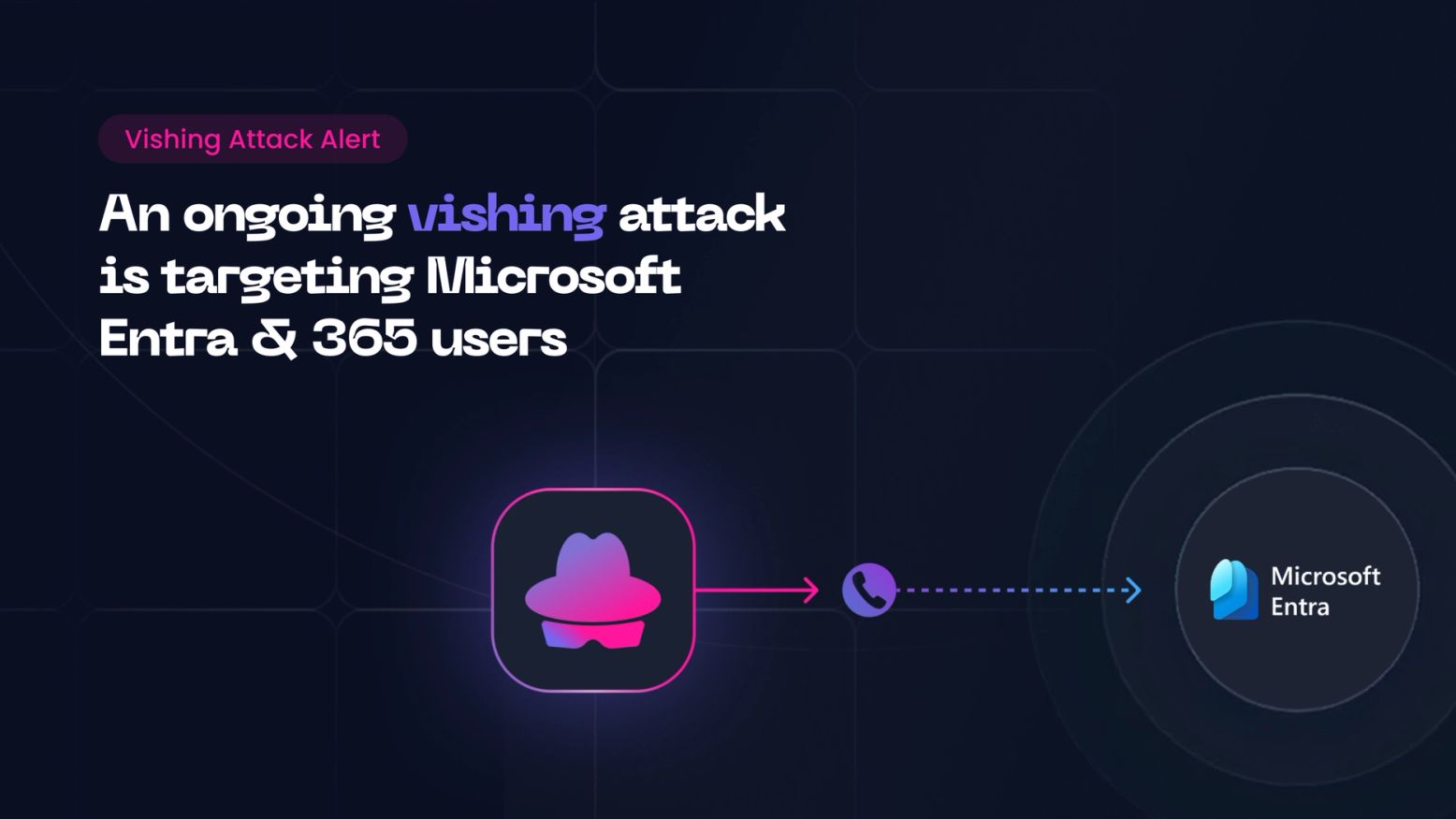
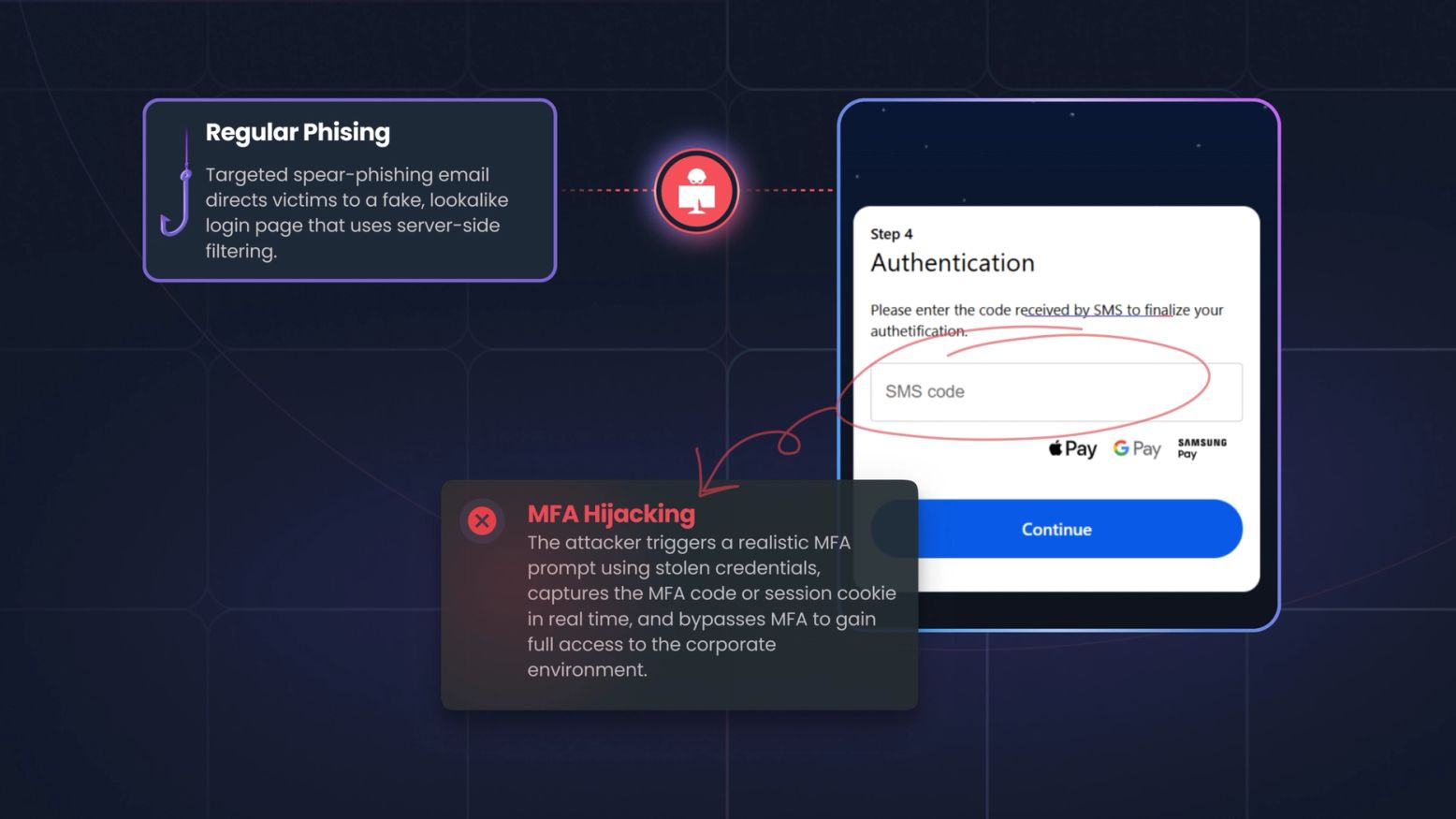
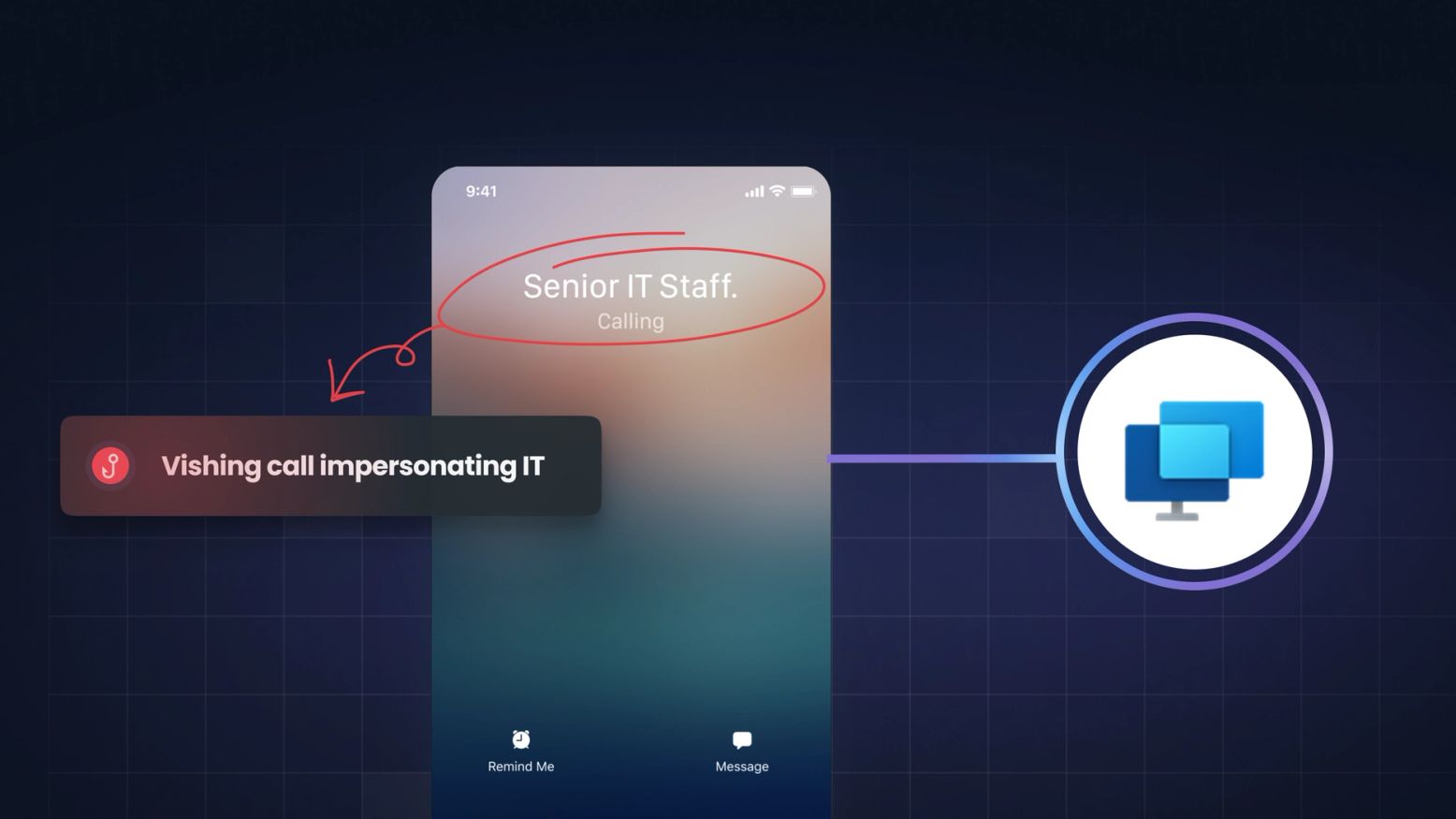
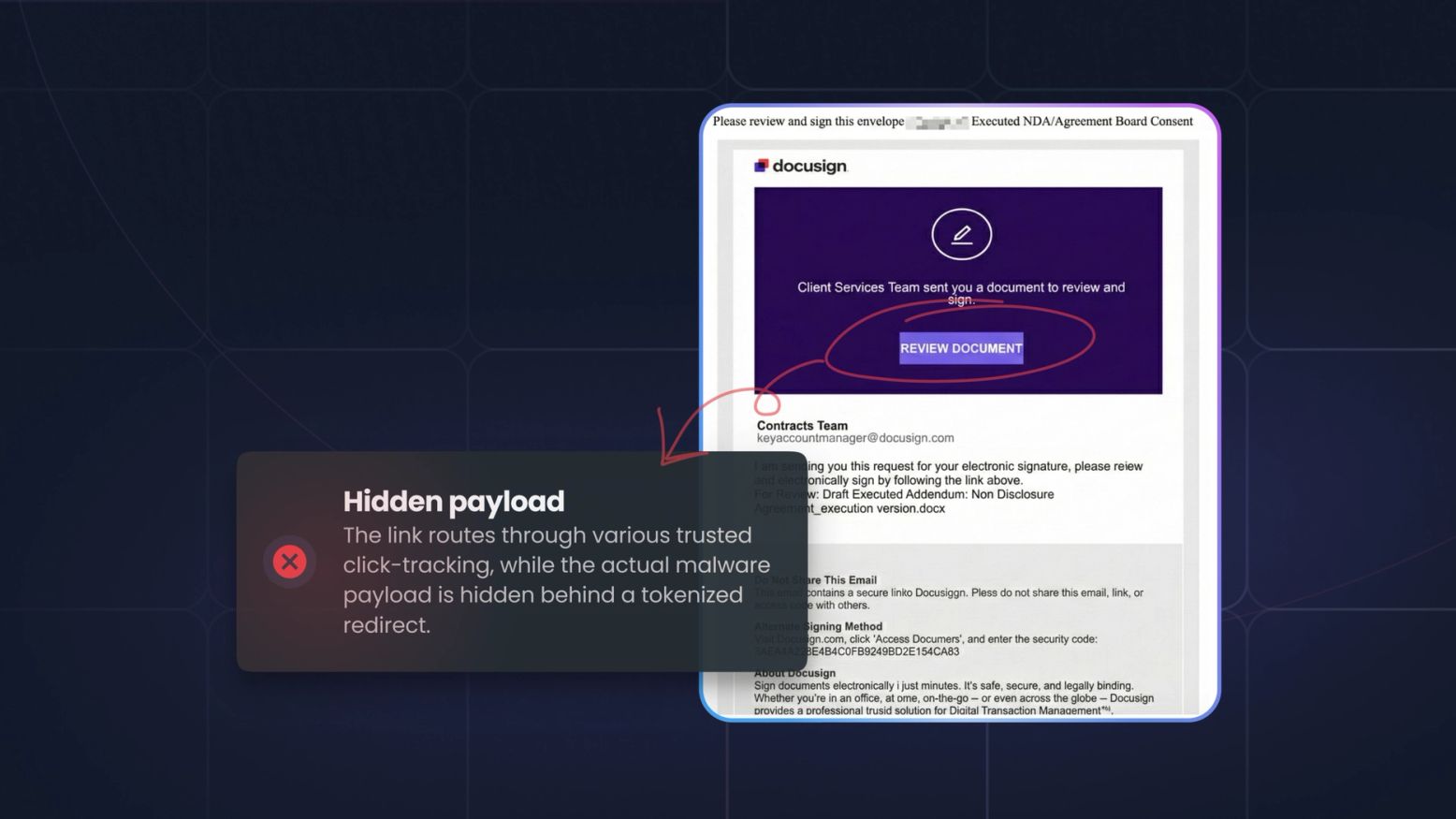
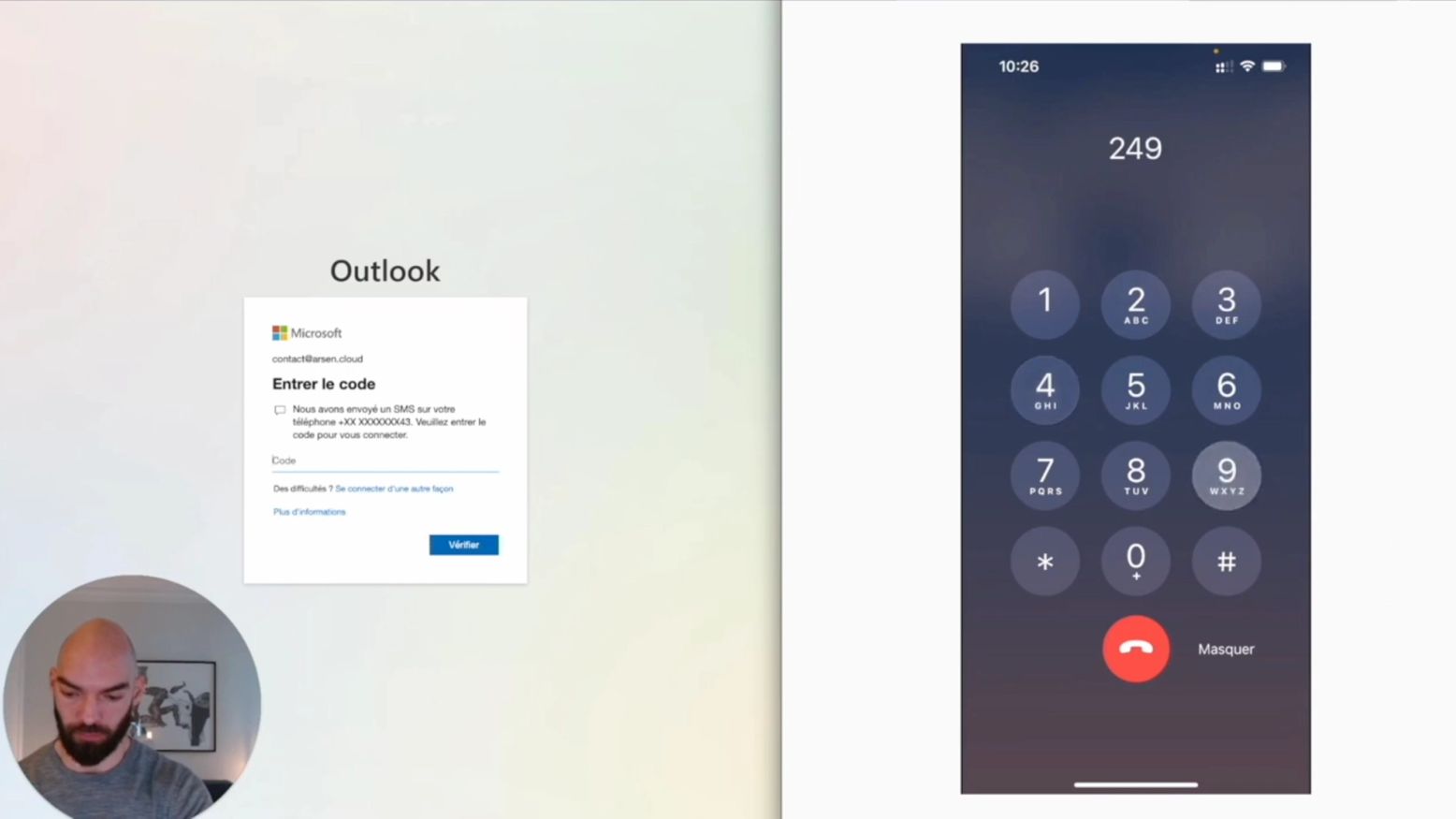
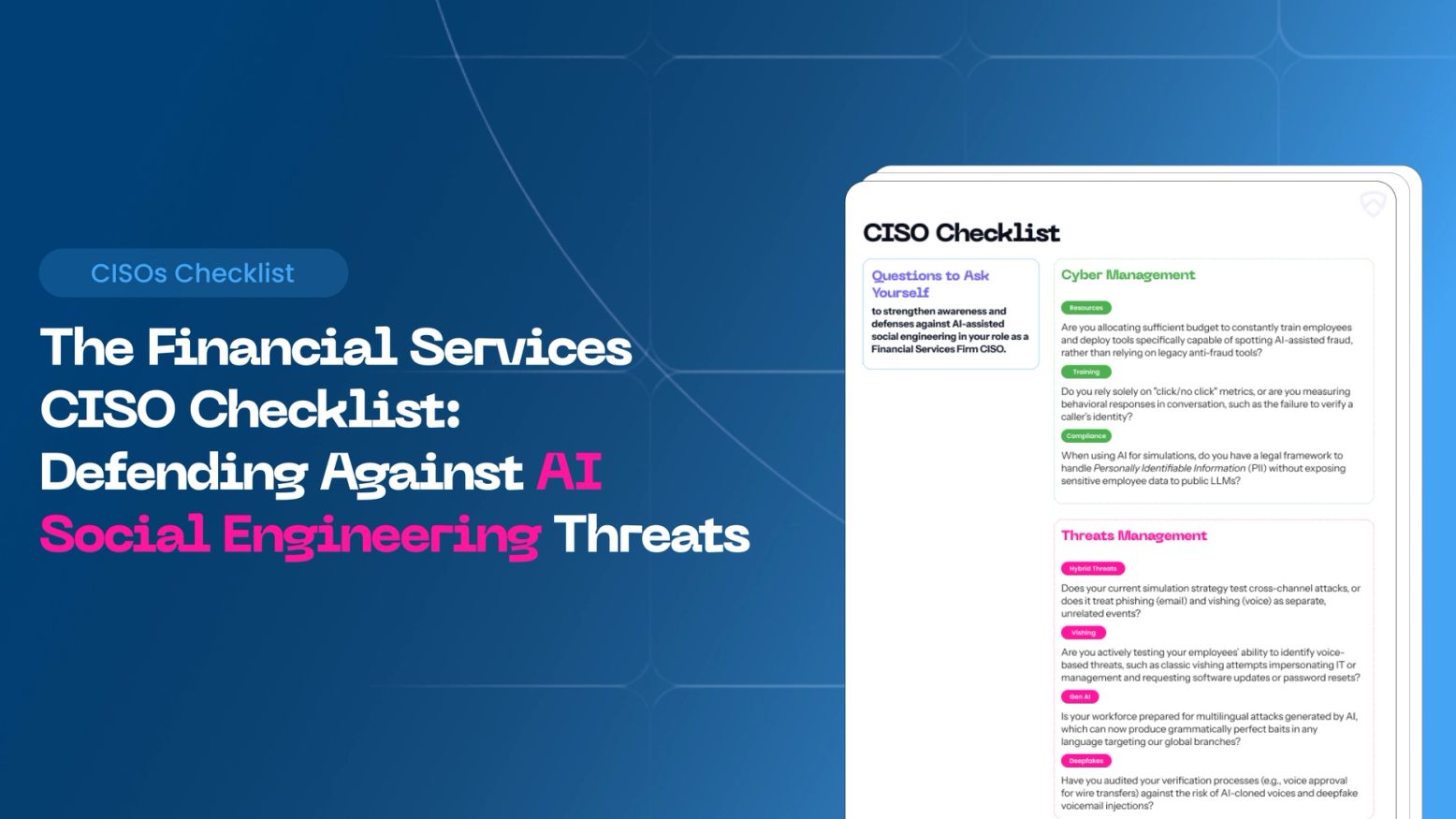
AI-powered social engineering is reshaping the threat landscape for banks, insurers, and fintechs. This guide gives financial services CISOs the frameworks, checklists, and strategic intelligence needed to close the preparedness gap before attackers do.