WannaCry is the malware behind one of the most significant ransomware attacks. In this article, we look back at the history of this particularly virulent ransomware.
What is WannaCry?
WannaCry was a ransomware that caused a real global digital pandemic in 2017. It held its victims' data hostage by encrypting it, preventing access to the files or restricting access to the entire infected computer. The only way to regain access was to pay a ransom in bitcoin. The malware operated solely on computers running the Microsoft Windows operating system.
Despite its consequences, the WannaCry software is very basic. The ransom was set at 300 euros, then 600 euros after three days. A week later, the hackers deleted all encrypted data.
After analyzing the malware's code, certain clues led cybersecurity experts to believe that amateurs developed the ransomware. Several signs indeed suggest that the group behind WannaCry lacked professionalism.
First, the relatively low amount of the ransom compared to other ransomware attacks suggests that the hackers did not fully understand the impact of their ransomware and the amount of money they could extort.
Second, much of WannaCry's code comes from code created by the NSA to exploit the EternalBlue vulnerability. This code became available when the Shadow Brokers group made it public on April 14, 2017, by posting a link on Twitter. The minimal modification of WannaCry's code compared to the NSA's code is another sign of the operators' lack of professionalism.
Third, the hackers did not reserve a domain to be used as a kill switch— a system allowing for the destruction and termination of the attack—resulting in a loss of control and the cessation of the ransomware. This amateurish mistake could have been easily avoided.
Ransomware typically excludes certain countries from the attack or demands a different amount based on the victim's location. WannaCry did not operate in this manner, which underscores the generic nature of the attack once again.
Despite its low level of sophistication, the attack had disastrous repercussions, particularly on the British healthcare system. We will delve into the history of WannaCry, how it worked, and its targets worldwide.
Its History
On May 12, 2017, the ransomware emerged in Spain and the United Kingdom before spreading worldwide within a few hours.
In just one night, WannaCry reportedly infected more than 100,000 Windows systems. Some victims, such as Renault or Nissan, chose to halt certain healthy production lines to limit the ransomware's spread, thus completely interrupting production.
Given the scale of the attack, Microsoft chose to release security updates for versions of its operating system it no longer maintains, such as Windows XP, Windows 8, and Windows Server 2003.
The attack infected over 300,000 computers in 150 countries, including the United States, Russia, and India. Today, the cyberattack led by WannaCry is considered the biggest ransom hack in internet history.
Companies like Vodafone, Renault, FedEx, Telefonica, the Russian Interior Ministry, the NHS, the University Hospital of Liège, and Deutsche Bahn are among WannaCry's biggest victims.
How Did It Work?
WannaCry ransomware spread through Eternal Blue and Double Pulsar. Microsoft then developed a patch to fix these vulnerabilities. Unfortunately, many domains, especially state ones, do not perform all Windows updates, allowing hackers to exploit these security flaws.
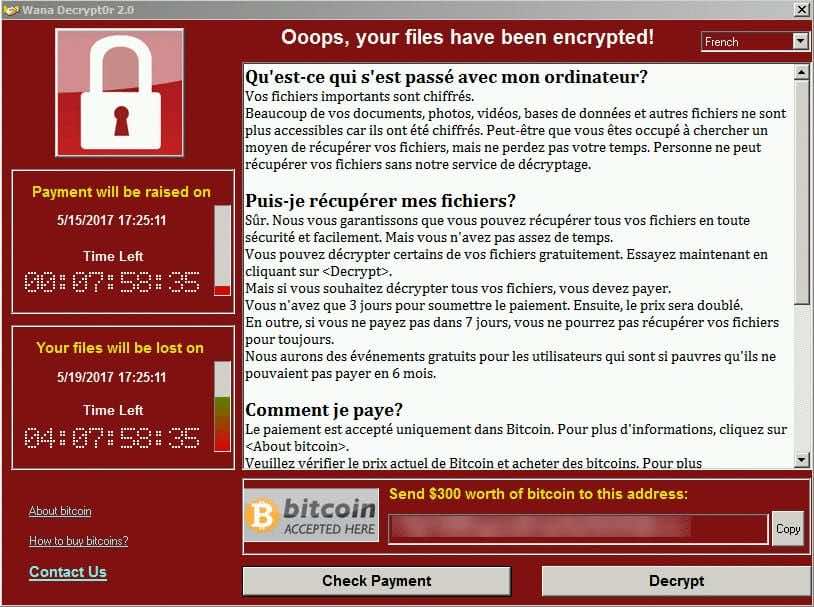
Overview of the WannaCry ransomware window
This vulnerability allowed the exploitation of a flaw in Windows' Server Message Block (SMB) protocol, thus spreading the attack. The protocol allows networked machines to communicate with each other.
WannaCry used DoublePulsar to install a backdoor, making it easier for the hacker to access the system.
The malware then encrypted the data to hold it for ransom. The program demanded payment within three days before doubling the ransom amount and then deleting the data if the victim had not paid a week later.
The Targets of the Ransomware
WannaCry's targets were diverse. Some of the ransomware's victims were users of unpatched Windows systems.

The National Health Service (NHS), and therefore British hospitals, were one of the ransomware's biggest victims. The attack caused a malfunction in flow management equipment, notably blocking access to patient records. Additionally, scanners, MRIs, and hospital product refrigeration centers were all put out of service. 70,000 devices displayed the message: "you must pay a ransom in bitcoin."
An emergency plan was deployed; some sites shut down their IT service, partially paralyzing their activities to avoid being infected by the virus. The NHS claims not to have paid any ransom. However, the cost of crisis management and cybersecurity training amounts to more than 250 million euros.
On May 12 and 13, 2017, Renault was also a victim of WannaCry. The National Agency for the Security of Information Systems (ANSSI) supported the manufacturer in its defense against the ransomware. The automotive group had to stop production at several factories to isolate infected computers and remove the malware.
It took several days for Renault to get rid of WannaCry.
The End of WannaCry
A 22-year-old Englishman, known as "MalwareTech," accidentally discovered a flaw in WannaCry. After analyzing the ransomware code through a copy he had made, an unregistered web address caught his attention: "IUQERFSODP9IFJAPOSDFJHGOSURIJFAEWRWERGWEA.COM."
He decided to purchase the domain name with the goal of monitoring the activities associated with it.
MalwareTech quickly realized that connections to the domain name were significantly diminishing. WannaCry was sending a ping to the mentioned address. If there was no response, the attack continued its progression; however, activating the domain prevented data encryption.
This phenomenon is called a "kill switch," allowing operators to stop a ransomware attack if necessary. This discovery helped curb the spread of WannaCry, thus enabling more effective and rapid handling of network infection.
Today, the WannaCry attack is considered one of the most significant cyberattacks globally, impacting various companies.
By replacing usual methods such as phishing or downloading via a malicious site with the exploitation of vulnerabilities, WannaCry marked a new era in ransomware.
Unlike other ransomware, WannaCry had many weaknesses, revealing the amateur aspect of the attack, limiting an already catastrophic impact.
The WannaCry attack would have had far less disastrous consequences if all Windows systems had been updated. Hackers would not have been able to exploit the Eternal Blue vulnerability.
Even though phishing was not the propagation vector for WannaCry, the hackers used the lack of awareness and negligence regarding system update policies to exploit a crisis situation.
The human factor remains a major element in cyberattacks; it needs to be effectively trained to reduce the number and impact of attacks. The WannaCry incident underscores the necessity for rigorous cybersecurity measures, regular system updates, and comprehensive crisis protocols to mitigate the risks associated with such global cyber threats.