
The Era of "Dark LLMs": How AI is Supercharging Social Engineering
The AI revolution of the 2020s has positioned Large Language Models (LLMs) as the new foundation for digital transformation. With unparalleled data processing power and text comprehension, LLMs can...

How Sophisticated Vishing Attacks are Currently Bypassing SSO for Wide-Scale SaaS Data Theft
The ShinyHunters group is currently orchestrating vishing attacks and exploiting SSO to bypass multi-factor authentication. These sophisticated campaigns have led to breaches of cloud platforms like...

The New Vishing Playbook: Attackers Can now Control the Flow in Real-Time and Break SSO
Identity attacks are evolving into hybrid vishing operations. New phishing kits allow attackers to manipulate a victim’s browser in real-time, syncing web visuals with phone scripts to perfectly...

How Quishing Can Be Weaponized to Target Top Organizations: The North Korea’s Kimsuky Case
The FBI warns that North Korean group Kimsuky is using quishing to target organizations. Discover how bad actors exploit QR codes to bypass security controls and how to test your defense against...

The InboxPrime Case: AI-Based Phishing Kits, Or The New Frontier of Credential Theft
AI and LLMs are creating a paradigm shift in cyberattacks. Attackers now use AI-powered kits to automate the entire attack lifecycle with unprecedented speed and precision. CISOs must adapt awareness...
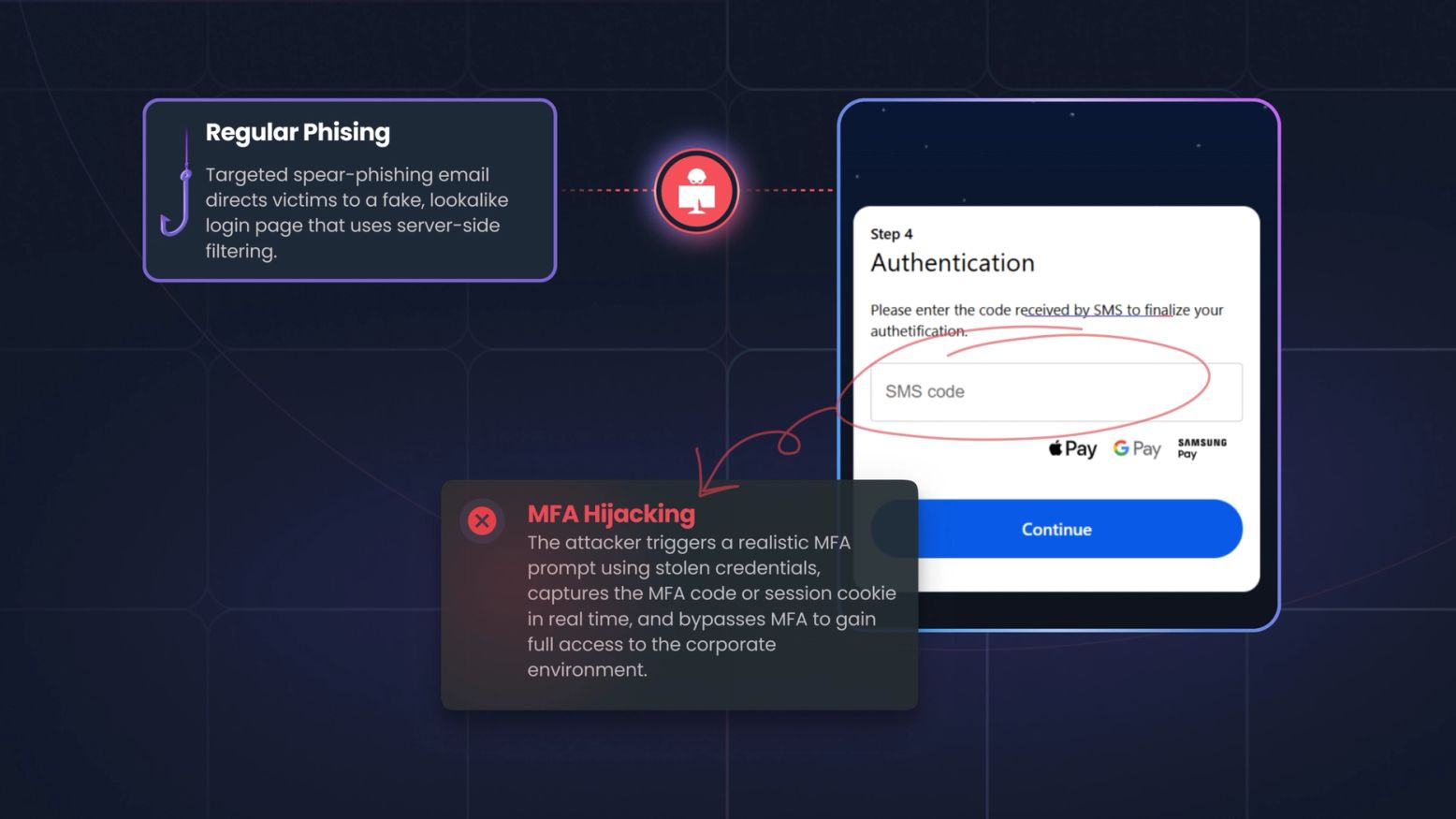
The BlackForce MitM Phishing Kit & MFA Hijacking: When Your Credentials Are No Longer Enough
Phishing has evolved. Zscaler ThreatLabz recently revealed BlackForce, a toolkit hijacking active sessions and bypassing MFA, using the "Man-in-the-Middle" (MITM ) attack tactic. CISOs must update...

Vishing Training Platforms for Call Center Teams
Call centers are prime targets for voice phishing due to high-pressure environments and shared access. Discover why specialized vishing training platforms are essential for BPOs to defend against...

Vishing Training for Financial Services Teams
Protect your financial institution from voice phishing. Learn why vishing targets banking and fintech teams, the limitations of traditional defenses, and how to implement scalable, compliant...
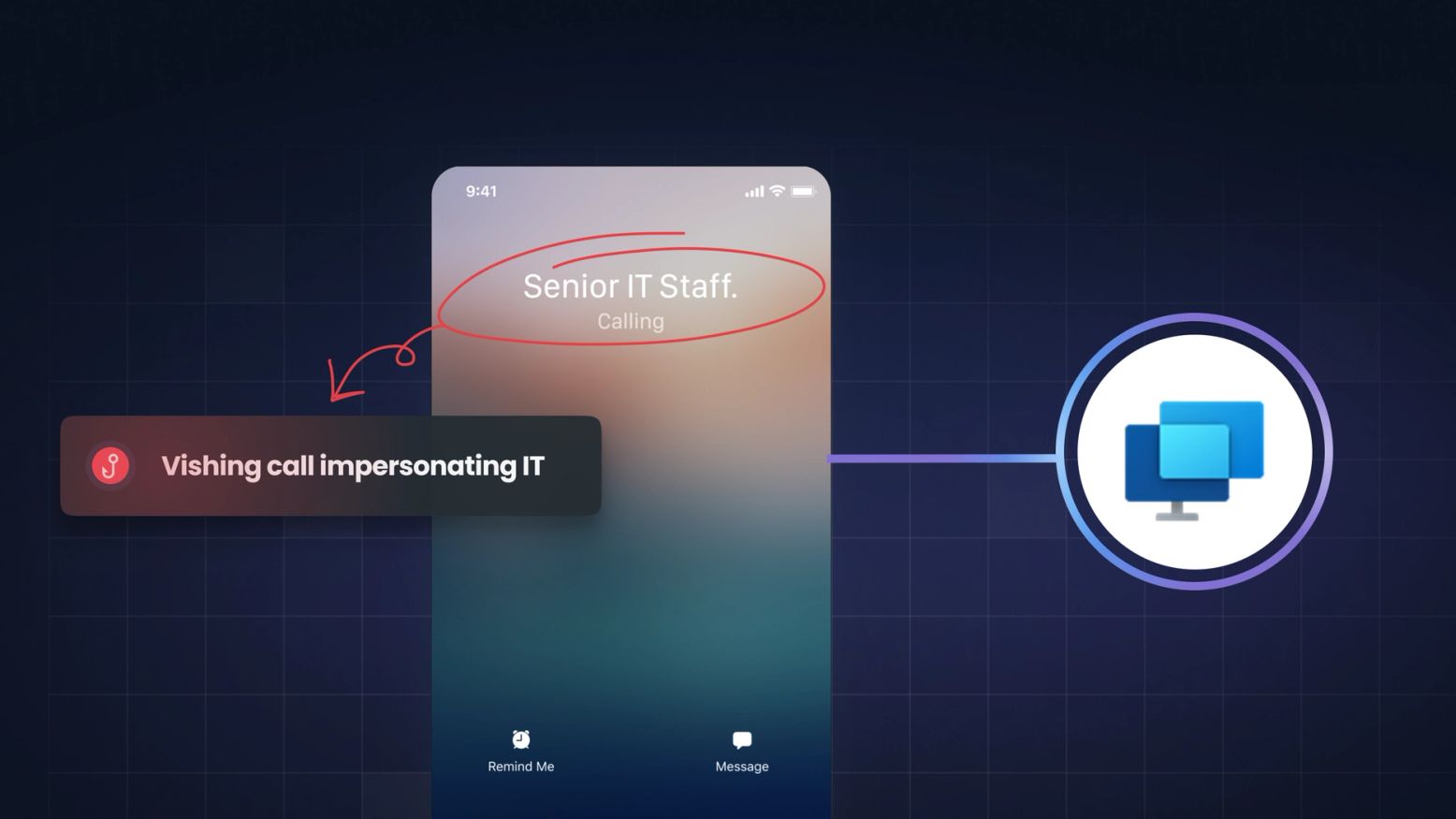
Vishing And The "Quick Assist" Trap: How Attackers Weaponized A Trusted Microsoft Tool
A new vishing campaign weaponizing Microsoft Teams and Quick Assist for fileless malware execution was recently revealed. Learn how this hybrid attack bypasses defenses and why AI-driven vishing...
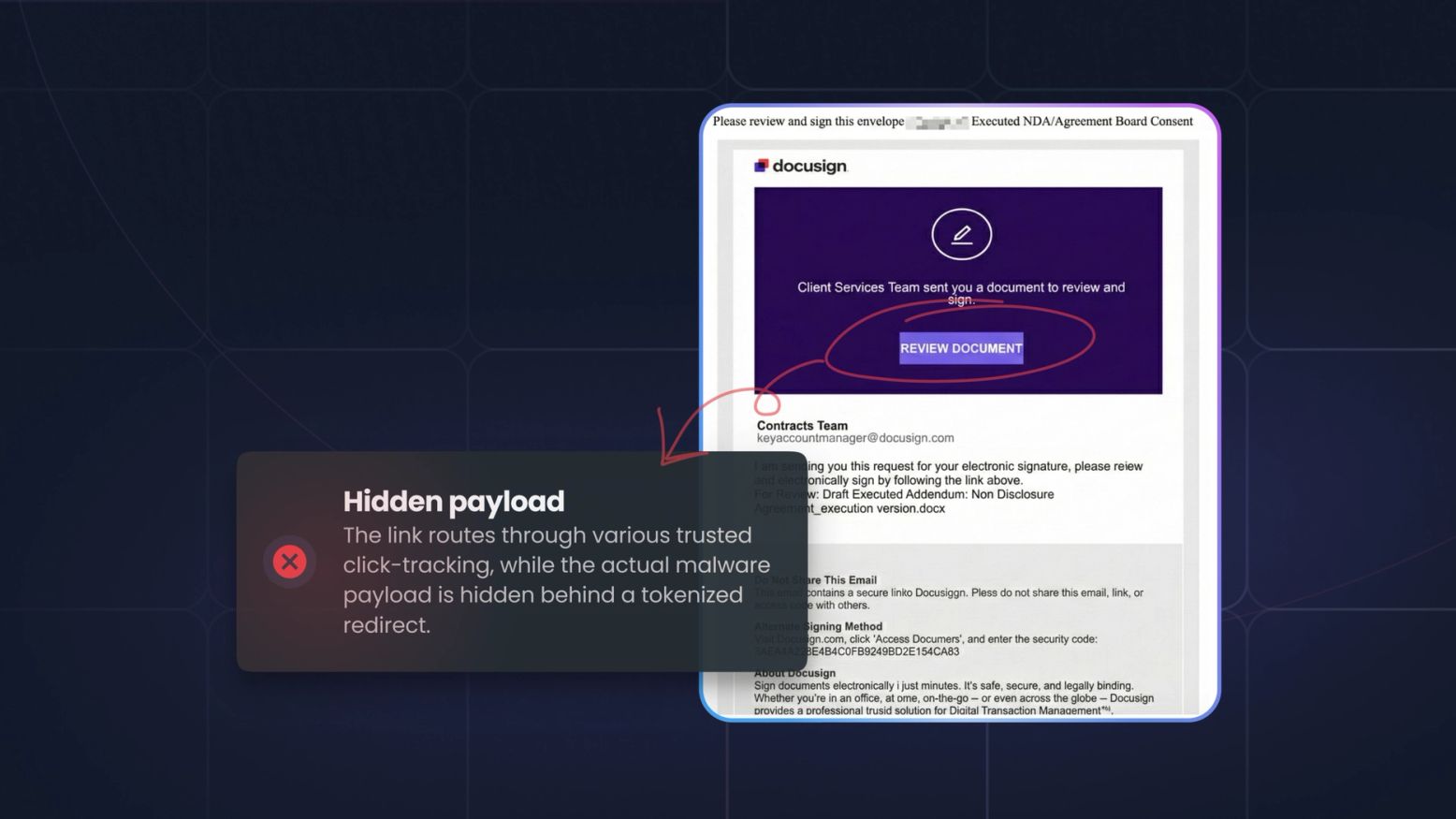
How Hundreds of Financial Institutions Were Hit by Massive Phishing and How to Prevent It
A recent massive phishing campaign targeted financial institutions by weaponizing trusted services like Mimecast and DocuSign. Discover how these attacks bypass filters and learn how to protect your...

Vishing vs Phishing in Cybersecurity Awareness Programs
Email phishing is still the #1 entry point for social engineering, but attackers no longer stop at the inbox. They follow up with phone calls, pressure employees in real time, and stitch channels...

AI Voice Phishing Simulations: Legal Considerations
Vishing simulations are a powerful awareness tool — but without legal guardrails, they can put your organization at risk. Here’s how to approach them safely.

Cybersecurity Awareness Training and FERPA: Securing Student Records Through Education
The Family Educational Rights and Privacy Act (FERPA) protects the privacy of student education records in the United States. While FERPA places legal obligations on schools, universities, and...

How Cybersecurity Awareness Training Supports the NIST Cybersecurity Framework
The NIST Cybersecurity Framework (CSF) is a widely adopted set of best practices for managing cybersecurity risks across all sectors — from critical infrastructure to cloud-native startups. It...

Cybersecurity Awareness Training for CCPA / CPRA Compliance: Empowering Employees to Protect Consumer Privacy
The California Consumer Privacy Act (CCPA) and its expanded version, the California Privacy Rights Act (CPRA), have redefined how businesses must handle personal data in the U.S. These laws emphasize...

PCI-DSS and Cybersecurity Awareness Training: Protecting Cardholder Data from Human Risk
The Payment Card Industry Data Security Standard (PCI-DSS) is a mandatory framework for any organization that stores, processes, or transmits cardholder data. While most PCI compliance efforts focus...

HIPAA Compliance and Cybersecurity Awareness: Training for Healthcare Data Protection
The Health Insurance Portability and Accountability Act (HIPAA) mandates the protection of Protected Health Information (PHI) across healthcare providers, insurers, and business associates. While...

Cybersecurity Awareness Training and NIS2 Compliance: Securing the Human Layer in Critical Sectors
The NIS2 Directive (Directive (EU) 2022/2555) represents a significant expansion of the EU’s cybersecurity legislation, aimed at strengthening resilience across critical infrastructure and digital...

Cybersecurity Awareness Training for DORA Compliance: Managing Human Risk in Financial Services
The Digital Operational Resilience Act (DORA) is the European Union’s new regulatory framework aimed at strengthening the operational resilience of financial services — including banks, fintechs,...

Cybersecurity Awareness Training and ISO 27001: A Practical Compliance Guide
ISO/IEC 27001 is one of the most widely recognized standards for Information Security Management Systems (ISMS). Whether you're pursuing certification or maintaining compliance, one thing is clear:...

Meeting SOC 2 Type II Requirements with CSAT
SOC 2 Type II has become the gold standard for demonstrating security and trustworthiness in the SaaS and technology sectors. Unlike Type I, which evaluates controls at a point in time, Type II...

How Cybersecurity Awareness Training Supports GDPR Compliance
Since the introduction of the General Data Protection Regulation (GDPR) in 2018, organizations operating in or serving the EU have faced strict requirements for how they handle personal data. While...

Modern Phishing Detection: Why It’s So Hard and How to Get Better at It
Modern phishing detection is notoriously difficult. As technology evolves, so do attack patterns. What was once a simple scam exploiting an emotional lapse has become a sophisticated, multi-layered...

MFA Fatigue: The Growing Threat Undermining Multi-Factor Authentication
Multi-factor authentication (MFA) was supposed to be the silver bullet. By requiring a second step—typically a push notification or a one-time code—organizations could drastically reduce the risk of...

Quishing: The Rise and Dangers of QR Code Phishing
Quishing — short for QR code phishing — is a rapidly growing threat vector that blends physical simplicity with digital deception. While many organizations have matured their defenses against...

QR Code Phishing: The Complete Protection Guide
QR code phishing, sometimes called “quishing,” is a rising threat that cleverly blends the digital and physical worlds. Attackers embed malicious URLs inside QR codes, hoping victims will scan them...

AI Vishing Attack: analysis of a new threat
"The voice sounds real. The request seems urgent. But the person on the line doesn’t exist." AI is transforming vishing into something faster, more convincing—and terrifyingly scalable. With voice...

Vishing Awareness Training: train your employees against vishing
"Your employees might know about vishing—but will they recognize it when it strikes?" Awareness isn’t enough. In today’s threat landscape, attackers exploit emotion, pressure, and live interactions...

Callback vishing: when phishing leads to vishing
"Think you're safe because you made the call? Think again." Callback vishing flips the script—literally. Instead of the hacker calling you, you unknowingly call them. Blending the deceptive power of...

Voice cloning attacks: all you need to know
"Can you trust the voice on the other end of the line?" With AI-powered voice cloning now accessible to anyone with an internet connection, this chilling question is no longer theoretical. From...

The Slovakia Election Deepfake: AI’s Threat to Democracy
In 2023, Slovakia became a cautionary tale when a fake audio recording targeting a prominent candidate in its national election sparked widespread outrage and concerns about electoral fraud. This...

The Le Drian Scam: A Masterclass in Social Engineering
Social engineering, the art of manipulating individuals to divulge confidential information or perform actions that compromise security, has evolved dramatically in recent years. But before talking...

Social Engineering Attacks: Tactics and Defenses
In this article we’ll explore how people’s emotions become business vulnerabilities, why social engineering is so effective, and three powerful principles to secure and protect your environment.

How to Run a Simulated Vishing Attack? Our complete guide.
"How would your team respond to a voice phishing attack—right now?" In today’s threat landscape, knowing isn’t enough. Simulated vishing attacks are the safest way to uncover how employees actually...
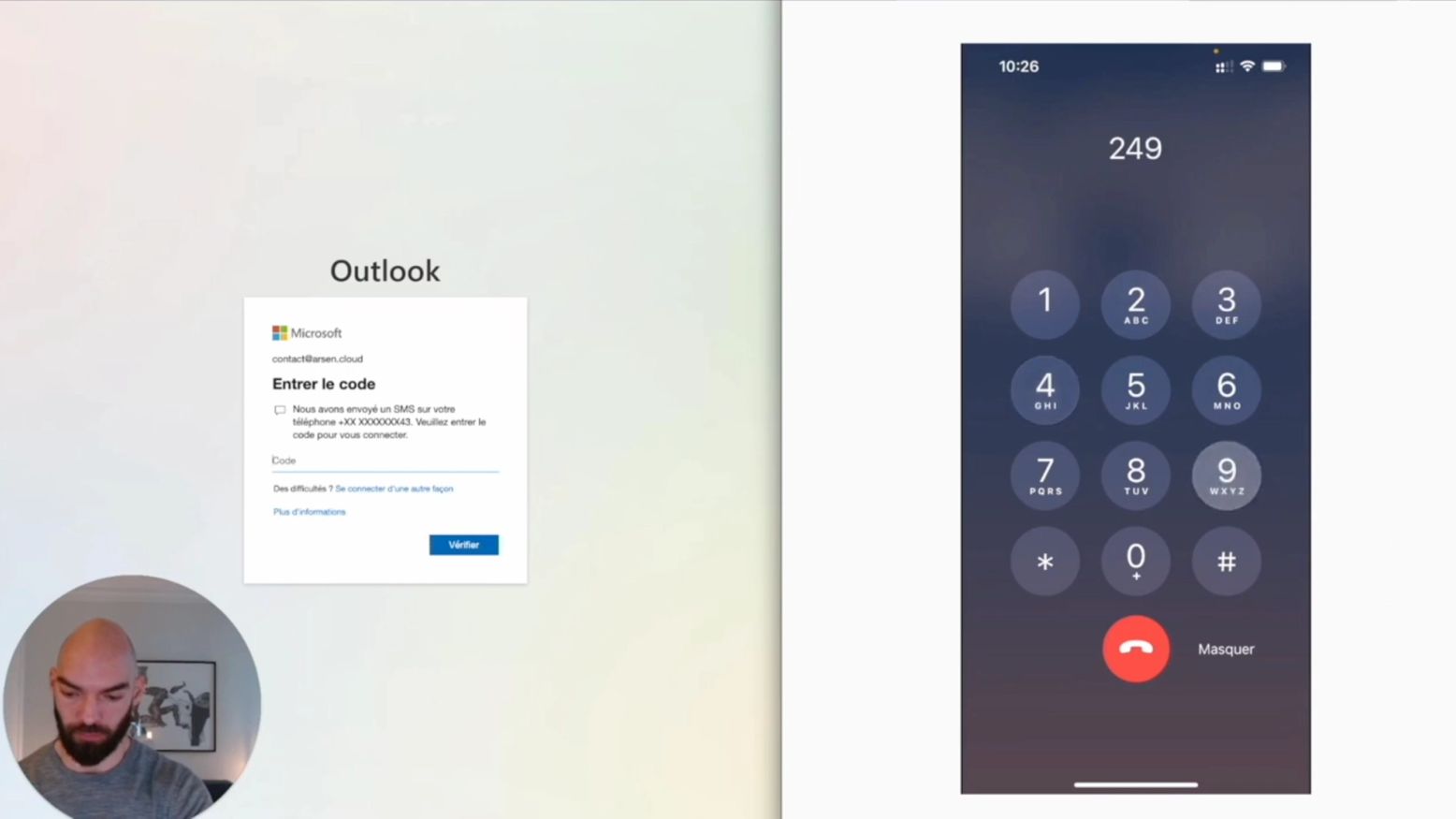
Bypassing Multi Factor Authentication (MFA) with a callbot
Call bots, a kind of vishing automation can be used to trick victims and defeat MFA. Here's how.

What Is Bad Rabbit Ransomware? How It Works & How to Stop It
In the world of cybersecurity, Bad Rabbit ransomware has made headlines as one of the more sophisticated and dangerous ransomware attacks. This malware first surfaced in 2017, targeting companies...

Cybersecurity Regulatory Compliance — Key Strategies for CISOs
In today's digital age, regulatory compliance is a critical aspect of running a successful business. Ensuring that your company adheres to applicable laws and regulations helps avoid legal penalties,...

What Is a VPN? How It Works & Why You Need One
In today's increasingly digital world, safeguarding online privacy has become more crucial than ever. One of the most effective ways to protect your personal information while browsing the web is by...

DNS Security: Best Practices to Protect Your Network
In today's digital landscape, DNS security is a crucial aspect of safeguarding any organization’s network. The Domain Name System (DNS) acts like the internet’s phonebook, translating domain names...

PII Meaning — What It Is & How to Protect Personal Data
In today's digital world, the term "PII" (Personally Identifiable Information) has become central to discussions around cybersecurity and privacy. But what exactly is PII, and why is it so important...

Watering Hole Attack: What It Is & How to Prevent It
Watering hole attacks are an increasingly sophisticated cyber threat, targeting specific groups or organizations by compromising websites they frequently visit. In this article, we will break down...

Which Type of Phishing Simulation Should You Choose?
Phishing comes in different shapes and forms. This means you have a lot of choices when it comes to creating a phishing simulation, and most companies get confused as to what type of simulation...

How to launch a phishing simulation to better protect your company?
In this post, we'll explore the key steps to launch a phishing simulation that will help you protect your company from phishing attacks.

Employee Phishing Training — Empower Your Workforce Against Attacks
Phishing training for employees is essential in building defense skills against cyberattacks. By educating employees on how to recognize and respond to phishing attempts, businesses can reduce the...

Phishing Training — Build Employee Awareness & Resilience
Phishing training is essential for protecting your organization from cyberattacks. By educating employees on how to recognize and respond to phishing threats, you can reduce the risk of data breaches...

Build Phishing Awareness & Protect Your Organisation
Phishing awareness is essential to safeguarding your business from cyberattacks. Learn how to recognize phishing attempts, understand common tactics used by attackers, and implement strategies to...

What Is a Common Indicator of a Phishing Attempt?
Identifying common indicators of a phishing attempt is crucial for staying secure online. Look out for suspicious sender addresses, generic greetings, urgent language, unusual links, and requests for...

Phishing Attack Types Every CISO Should Know
Phishing attacks come in various forms, from deceptive emails to fraudulent text messages. Understanding the types of phishing—including email phishing, spear phishing, smishing, vishing, and clone...

What Is Spear Phishing? Definition & Defense Tips for CISOs
Spear phishing is a targeted form of phishing that uses personalized tactics to deceive specific individuals or organizations. Unlike regular phishing, spear phishing exploits trust by mimicking...

Spam vs Phishing — Key Differences & How to Stay Protected
Spam and phishing are common types of unwanted emails, but they serve different purposes and pose different risks. While spam typically promotes products or services, phishing aims to steal sensitive...

Smishing vs Phishing: What Cybersecurity Pros Must Know
Smishing and phishing are cyber threats that use deception to steal personal information. While phishing typically targets victims through email, smishing uses text messages to trick individuals into...

How to Identify a Phishing Email & Protect Your Organisation
Phishing emails use deceptive tactics to trick you into revealing sensitive information. Learning to identify phishing email techniques, such as manipulated sender addresses, urgency tactics, and...

Vishing Definition & How to Stop Voice Phishing Attacks
Vishing, or voice phishing, is a phone scam where attackers use various techniques, such as caller ID spoofing and urgency tactics, to trick victims into revealing sensitive information....

AI Attacks — How Artificial Intelligence Is Changing Cyber Threats
Conference on the Impact of AI on Cyberattacks in 2024.
How Klaxoon uses Arsen to train its employees against phishing attacks
Aymeric from Klaxoon explains why they chose Arsen to train their employees and improve their reflexes against phishing attacks.
Phishing & AI: new attacks and new solutions
In this discussion with Benjamin Leroux from Advens, we explore the changes brought by generative AI to the attack landscape when it comes to phishing and social engineering.

Malicious Attachment generation with generative AI
Spreading malware or gaining initial access through email attachment is the third most common phishing tactic. Because of the scale of our phishing operations at Arsen, we wanted to explore the use...

Generative AI Phishing Scenarios
GenAI phishing is now a thing. You might want to deploy it for your clients or your company but you might also want some scenario suggestions to get your creative juices flowing. This article is...

Using third party LLMs for genAI phishing operations
With the rise of genAI phishing, you might be tempted to use it for your phishing operations. Using a third party, well trained LLM has obvious advantages, from infrastructure cost — this GPU time...

Effective generative AI for phishing engagements
If you’ve been reading our content, you’re probably itching to shoot some genAI phishing for your next simulation campaign. But one does not simply ask ChatGPT for a cool phishing email. Here are...

Defense in depth: the importance of the human factor
A paradox has struck me for several years now. Everyone I speak to is convinced of the predominance of human risk. The internet is full of statistics linking initial access to employee behavior in...

3 advantages Arsen has over Gophish
At Arsen, we love Gophish. It’s by far the most comprehensive open-source solution for deploying phishing, whether for evaluation, training, or research purposes. That being said, GoPhish has...

Use of AI in Social Engineering Attacks
From phishing to fake transfer scams, social engineering is rampant. User manipulation is responsible for a large number of cyberattacks, and the situation is not improving. Simultaneously, the...

USB Drop: Discover the USB drive powered attack
An attack via USB drive, also known as USB Drop, is a danger that is still underestimated. USB drives are very effective in helping us store and transport small amounts of data. We use them...

Why generate a random password?
Often, when an individual needs to create a new password, they will rack their brains and choose personal information that relates to them, then modify it by changing elements or adding special...
What is Juice Jacking ?
Juice jacking is a type of cyber attack that exploits USB charging cables or chargers to compromise devices with USB ports, especially mobile phones. Charging cables don't just power your phone's...
How to Conduct a Successful Phishing Simulation
Why conduct a fake phishing exercise? Phishing is the entry point for 91% of attacks*. The objective of phishing simulations is to prevent the hacking of your company in order to avoid financial...
Catfishing Definition: What It Is & How to Spot the Signs
In March 2021, the top 10 dating sites in France recorded 46.4 million visits, according to a study conducted by [monpetitdate](https://www.monpetitdate.fr/etude-statistiques-sites-de-rencontre/)....

WannaCry, the biggest ransomware heist in history
WannaCry is the ransomware behind one of the most significant ransomware attacks. In this article, we look back at the history of this particularly virulent ransomware.

Managing the risks tied to phishing
The risks associated with phishing are often underestimated. Many still believe that the consequences are limited to having to change a few passwords, scan their network, or even have a comprehensive...

What is a sextorsion attack?
A sextortion attack involves extorting money by blackmailing with a sexual theme. For instance, the malicious individual contacts the victim claiming to have a video of them in a compromising...

BEC Definition: Understanding Business Email Compromise
The compromise of email addresses, or Business Email Compromise (BEC), is a popular attack aimed at compromising a company's mailbox for malicious purposes. The simplest monetization is generally to...
Instagram Phishing: Risks and Protection Measures
Instagram is a highly popular social network, making phishing on the platform equally prevalent. According to the "Digital Report 2021" by Hootsuite and We Are Social, Instagram ranks fifth among the...
How to Run a Phishing Test & Measure Security Awareness
In this article, we will analyze the process of a phishing test, from its setup to reporting. We will discuss framing, technical deployment, execution, and post-mortem of the exercise.

How to Assess Phishing Risk & Strengthen Your Defenses
Phishing is the entry point for 90% of cyberattacks today. This threat poses various risks to a company, including organizational, reputational, financial, and legal risks. It is therefore...

Vishing examples: real world attacks and consequences
"Vishing may be less known than phishing—but the damage it causes is just as real." From tech giants like Twitter to global banks and energy firms, voice phishing has quietly become one of the most...
