An attack via USB Drop—a method where attackers leave USB drives for unsuspecting victims to find and plug into their computers—is a significant cyber threat that is often underestimated. While USB drives are incredibly useful for storing and transferring data, they also serve as powerful vectors for cyberattacks. Many users are unaware of the security risks associated with these small, portable devices.
In this article, we'll explore the different types of USB Drop attacks, the potential consequences, and how to protect yourself and your organization from them.
What are the Different Types of USB Drop Attacks?
USB Drop attacks generally fall into three main categories. Each type relies on persuading the victim to connect the USB drive to their computer. Therefore, human behavior plays a crucial role in the success of a USB Drop attack.
#1 Using Social Engineering to Execute Malicious Files
Social engineering is a technique used to manipulate individuals into performing certain actions, such as clicking on malicious files found on a USB Drop device. The files on the USB may have enticing names like TopSecret.html or AccessCodes.xls, piquing the victim's curiosity and increasing the likelihood that they will open the files.
Once opened, these files can execute malware or redirect the victim to a phishing website, compromising their security. While antivirus software may sometimes block the malware, phishing redirections often go unnoticed, making this a sneaky method of attack in a USB Drop scenario.
#2 HID Spoofing: Making the Drive Appear as a USB Keyboard
Human Interface Device (HID) spoofing is a method in which the USB drive is disguised as a keyboard. When inserted, the computer mistakenly recognizes the drive as a legitimate input device. It then sends malicious commands to the computer, as if an invisible hacker were typing on a keyboard.
One famous example is the Rubber Ducky device, which is often used in USB Drop attacks to execute pre-programmed scripts that compromise the system.

The Rubber Ducky is a popular tool used in HID-based USB Drop attacks.
#3 Exploiting a USB Driver Vulnerability: Driver Zero-Day
The third type of USB Drop attack involves exploiting zero-day vulnerabilities in USB drivers. These vulnerabilities are unpatched flaws that attackers can use to run unauthorized code on the victim's machine as soon as the USB drive is plugged in.
The malicious code embedded in the USB Drop device leverages the flaw in the USB driver to execute a hack, giving attackers access to the victim's computer or network.
Do USB Drop Attacks Work?
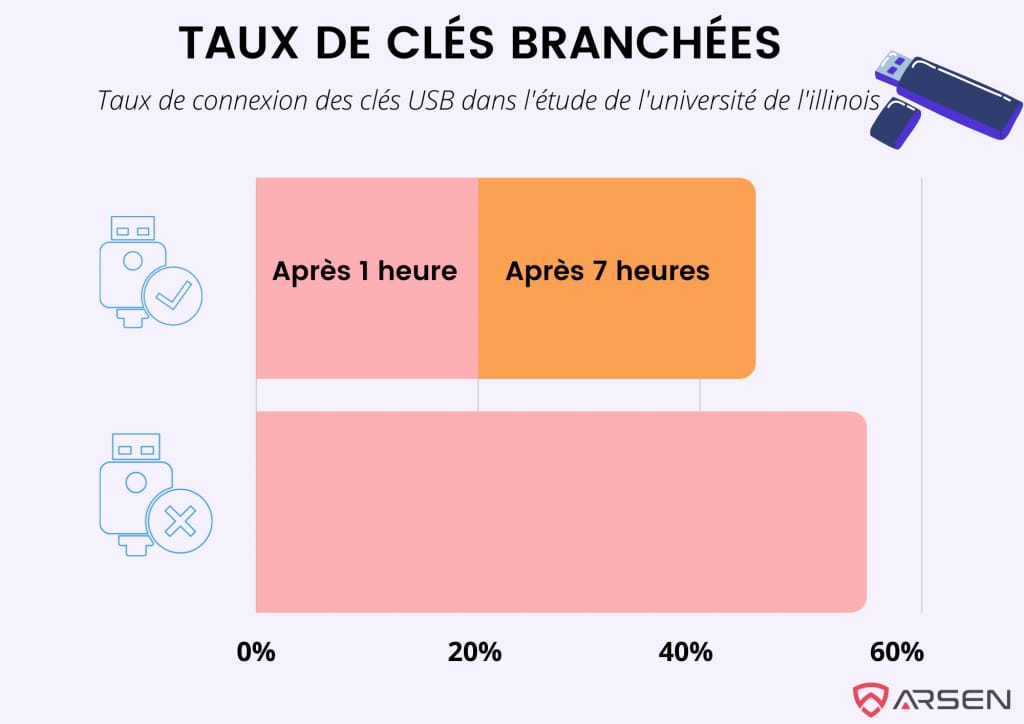
In 2016, researchers conducted a USB Drop experiment by scattering 300 USB drives across the University of Illinois at Urbana-Champaign campus. They monitored how many of these drives were plugged into computers and interviewed the participants afterward.
Here are the key findings:
- 20% of the USB drives were plugged in within the first hour, with an additional 25% connected within six hours.
- 48% of individuals who plugged in the USB drives opened or executed files on the drive.
Why Do USB Drop Attacks Succeed?
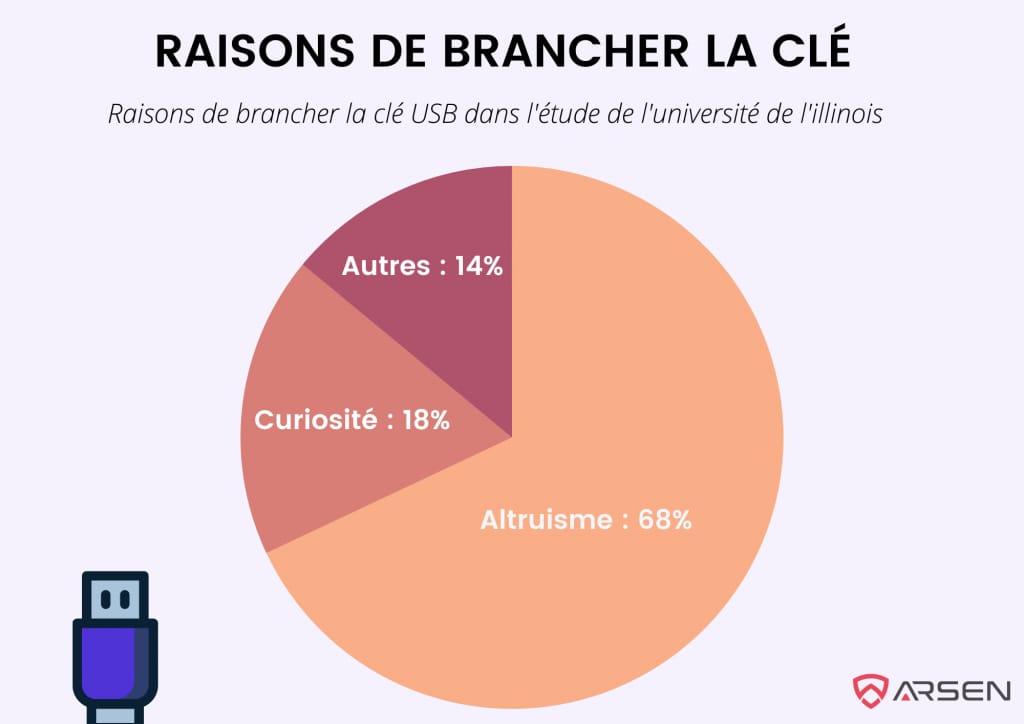
The study revealed that 68% of respondents connected the USB drives for altruistic reasons—they wanted to return the device to its owner. Another 18% admitted curiosity drove them to plug it in. Interestingly, attaching physical keys to the USB drive increased the likelihood that someone would pick it up and use it, believing it was genuinely lost.
Even with known risks, 45% of participants connected the USB Drop devices, demonstrating a widespread lack of awareness about the dangers of USB attacks.
If you discovered a USB drive with your name on it tomorrow, what would you do?
Possible Consequences of a USB Drop Attack
A successful USB Drop attack can have serious consequences, ranging from data breaches to hardware damage. Here are some potential outcomes:
Extraction of Sensitive Information
Cybercriminals can use a USB Drop to extract sensitive data such as passwords, personal information, and financial details. They often design the malware to target specific file types or directories, quickly siphoning valuable information.
Remote Access
A USB Drop can result in the installation of a RAT (Remote Access Tool), allowing the attacker to remotely control the infected computer and connected devices like webcams, microphones, and keyboards.
Hardware Destruction
Some USB Drop devices, known as "USB Killers," can physically destroy the hardware they are plugged into by delivering a high-voltage electric shock through the USB port. This overload fries the motherboard, rendering the computer inoperable.

USB Killers can instantly destroy hardware in USB Drop attacks.
Examples of USB Drop Attacks
2008 U.S. Military Attack: A USB Drop infiltrated a U.S. military computer, spreading undetected and compromising confidential data.
Stuxnet (2009): Stuxnet, a sophisticated virus, was delivered via a USB Drop to Iranian nuclear facilities, causing damage to the centrifuges used in uranium enrichment.
8 Tips for Protecting Against USB Drop Attacks
Here are eight essential strategies to guard against USB Drop attacks:
- Raise Awareness: Educate your team about the dangers of USB Drop devices and the importance of not using unidentified USB drives.
- Use Secure Transfer Stations: Deploy a secure device, like Hogo, to analyze data on USB drives before allowing it onto your network.
- Antivirus Protection: Install and update antivirus software that can scan USB devices for malware.
- Immediate Response: If a suspicious USB drive is connected, disconnect the device from the network and contact IT immediately.
- Disable Autorun: Ensure autorun features are disabled to prevent USB devices from automatically executing malicious code.
- Beware of USB Chargers: Avoid using unknown USB chargers, as they can also be used in USB Drop attacks (via juice jacking).
- Disable Unused USB Ports: Disable USB ports on devices that do not require them to minimize potential attack vectors.
- Comprehensive Security Training: Implement regular cybersecurity training that covers USB Drop attacks, phishing, and other threats.
The key to preventing USB Drop attacks is vigilance. By educating your team and implementing robust security measures, you can mitigate the risks associated with malicious USB drives.

