Business Email Compromise caused $55 billions in loss over the last 10 years
Because they use legitimate senders, they are hard to detect and can lead to tremendous loss and reputational impact.
- Hard to detect
-
BEC impersonate existing people and accounts, sometimes within existing email conversations, which makes it very hard to detect by untrained employees.
- Costly
-
According to the latest FBI IC3 report, a single successful BEC attack sots a business an average of $137,132. Overall, BEC is more costly than ransomware attacks.
- Reputational impact
-
On top of the financial loss, successful BEC have a very negative impact on your reputation and can impact the whole supply chain.
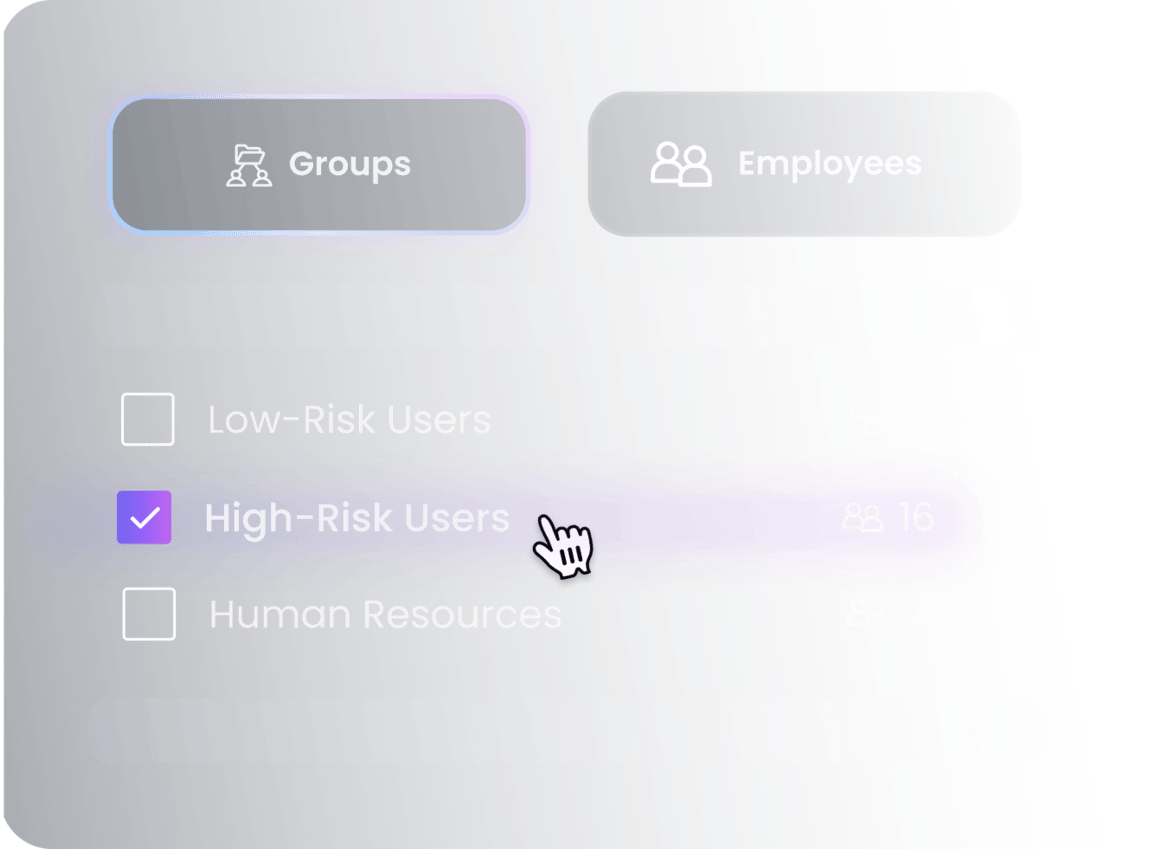
Train high-risk users
Use our targeting engine to target the most exposed and BEC-prone users in your system. Reinforce their awareness and training program so they can better defend themselves and your company against these attacks.
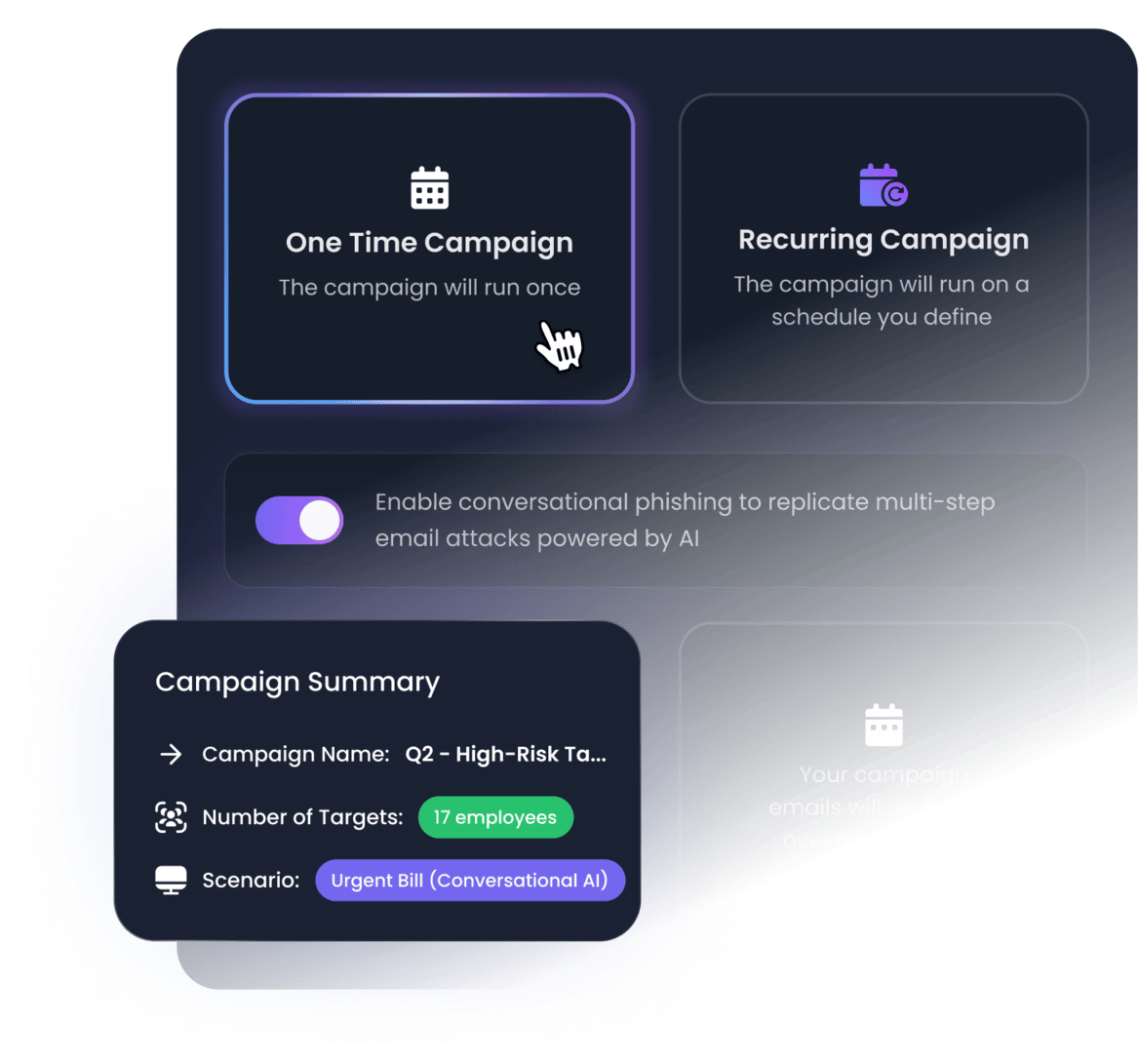
Reproduce BEC attacks
Using our simulation engine, you can reproduce BEC attacks to train your people to detect and defend against them.
- Learn by doing: simulate actual deceptive conversations leading to an attack with our conversational phishing engine.
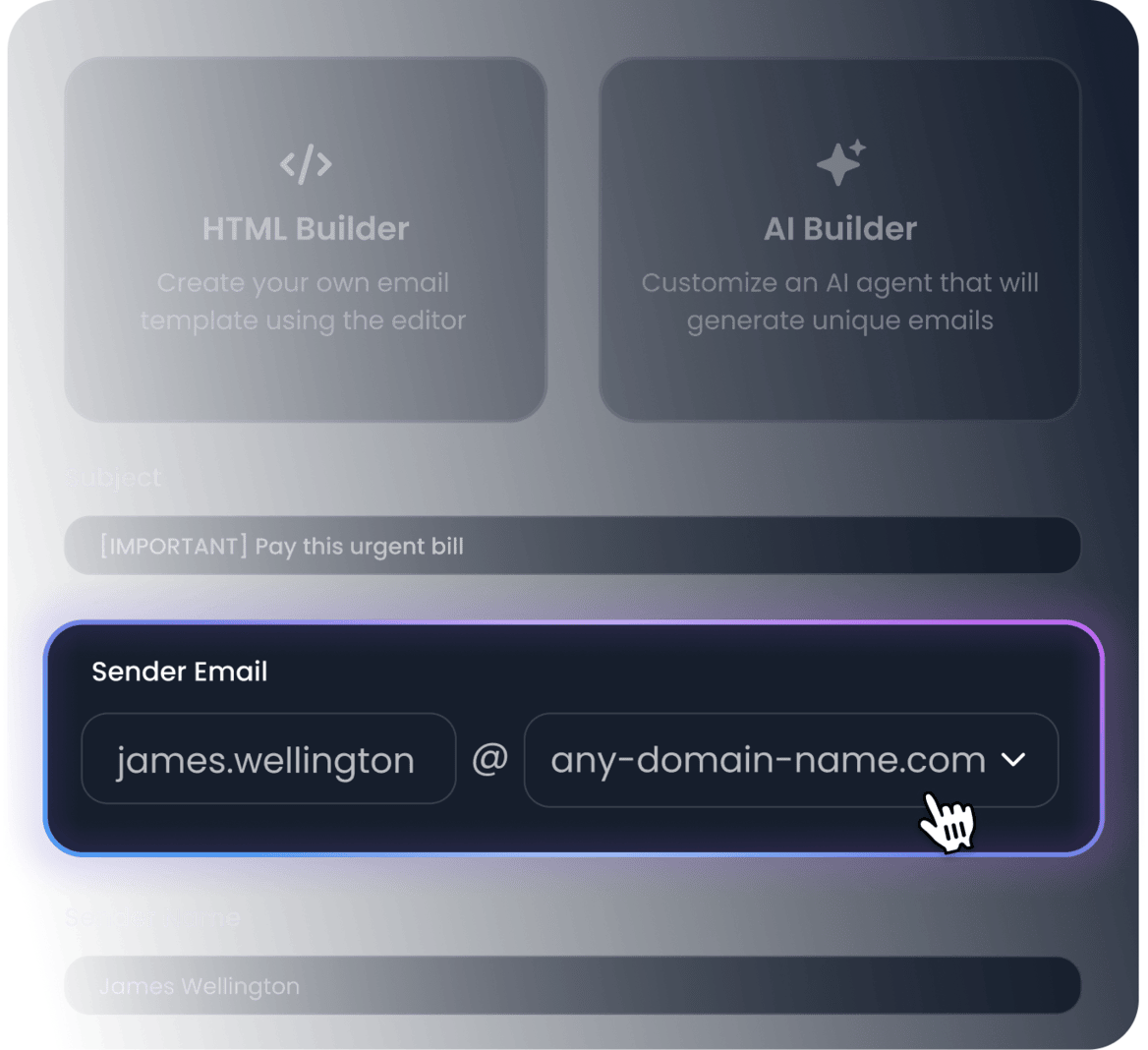
- Improve realism: use typosquatted domains just like attackers would do, using lookalike domains to deceive your users
- Adapt to your context: reproduce internal signatures to increase realism and train people against an advanced threat actor
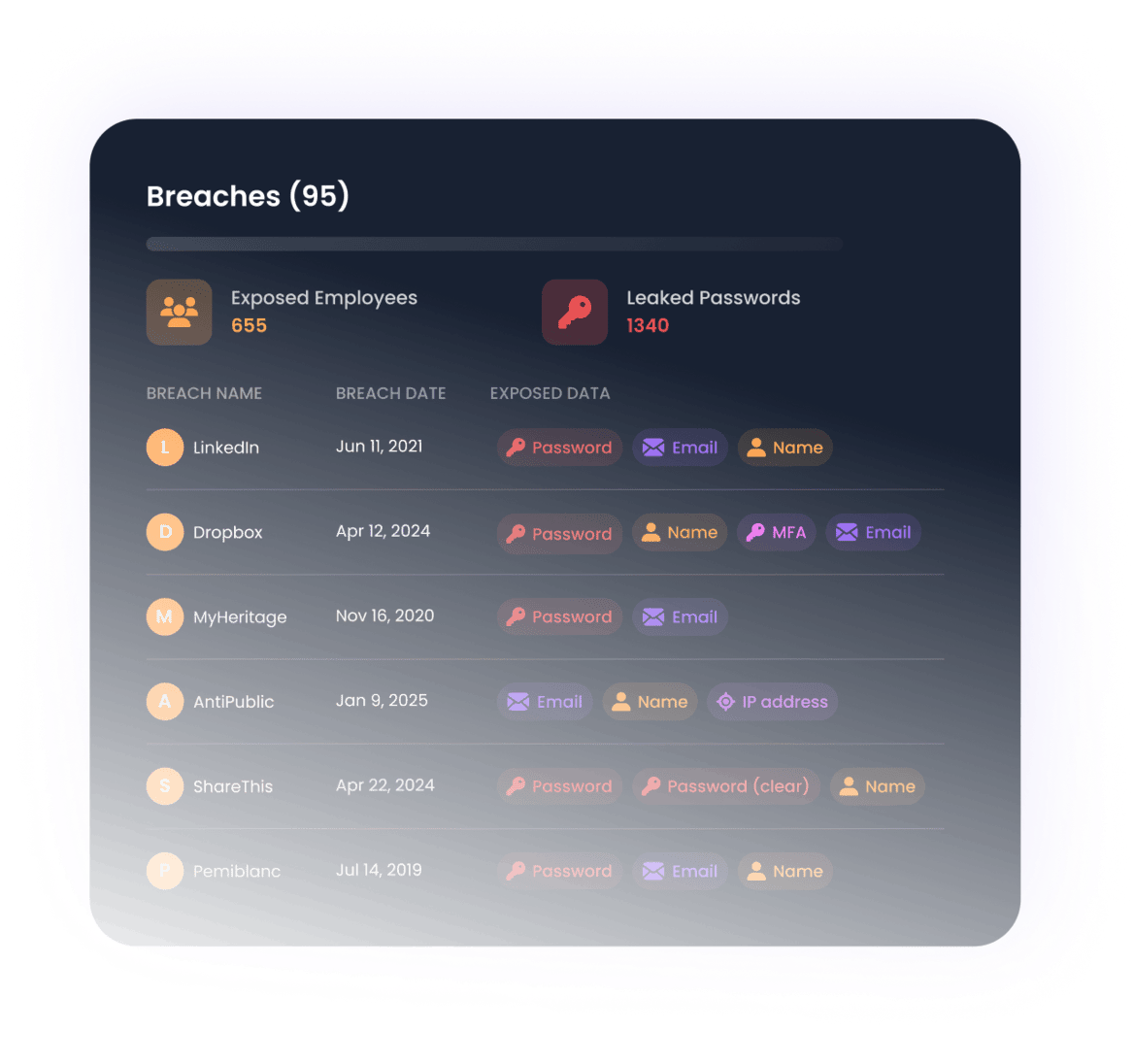
Monitor early attack signals
Use our threat monitoring to detect upcoming attacks. By monitoring new typosquatted domains and data leaks that could be used against you, you can better prepare and defend against BEC attempts.
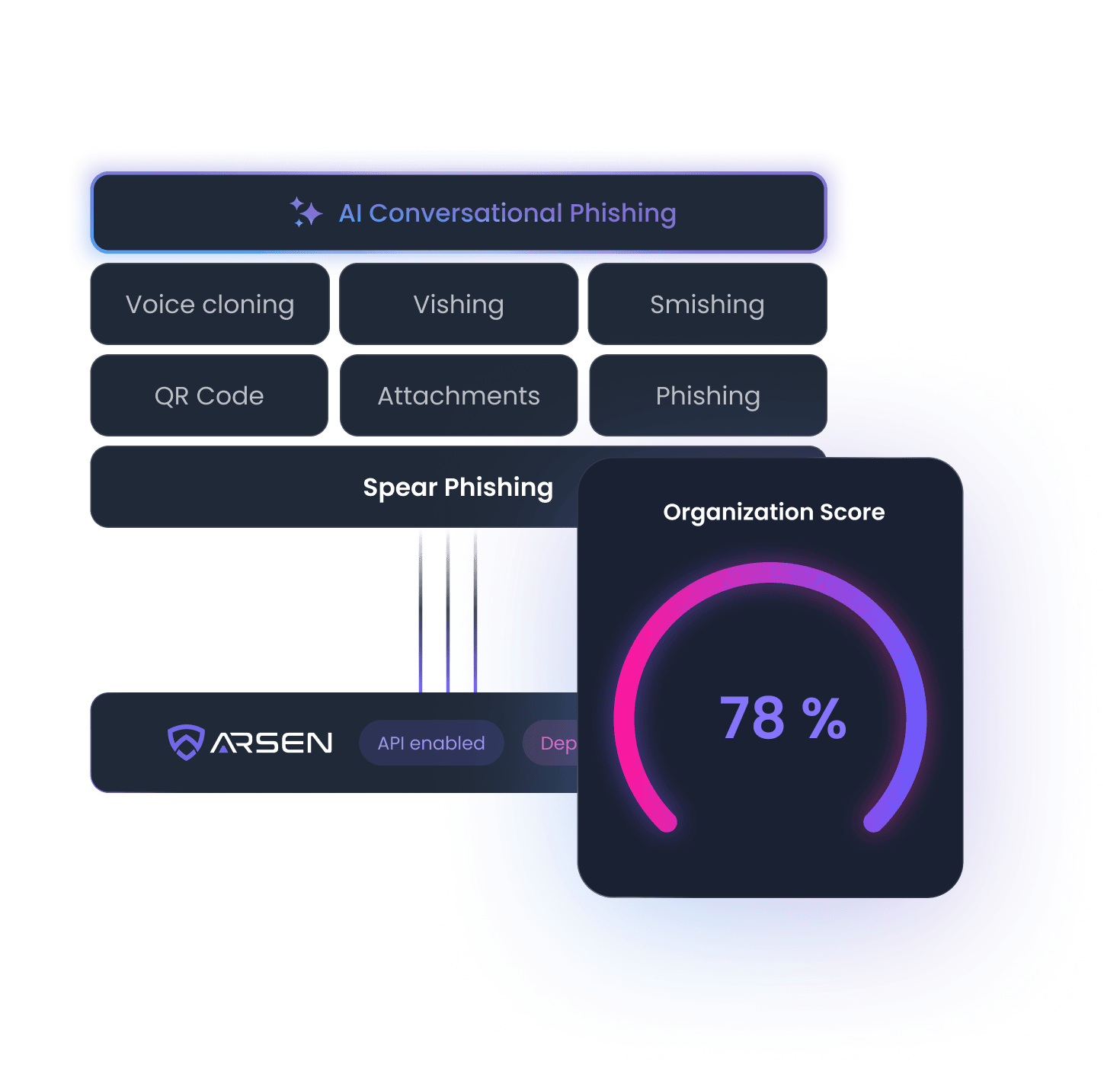
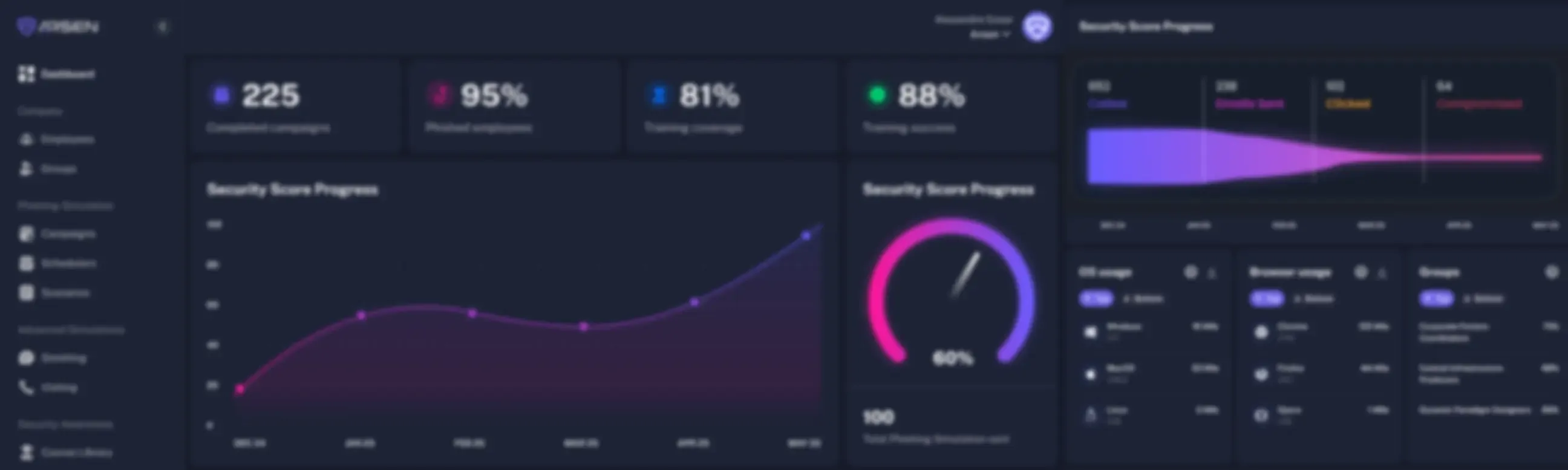
Arsen helps you fight against the most advanced social engineering attacks
Our platform leverages the latest technologies to create realistic spear-phishing simulations and monitor dark web activities for potential threats.
By combining these two products with a cybersecurity awareness program, we help you train your employees to recognize and report social engineering attacks before they become a real threat.