A sextortion attack involves extorting money by blackmailing with a sexual theme. For instance, the malicious individual contacts the victim claiming to have a video of them in a compromising situation. The individual then threatens to release the video unless they receive a payment.
Sextortion attacks are popular because they are very inexpensive for their operators to set up.
The Central Office for Combating Cybercrime related to Information and Communication Technologies (OCLCTIC) identified several hundred sextortion attacks, around 1,200 per year. In January 2021, Avast announced that it blocked over 500,000 sextortion attack attempts.
1- The Principle of the Sextortion Attack
The hacker first sends bulk emails to random contacts, hoping that some recipients will fall for the scam.
In the email, the attacker claims to have access to the victim's webcam or compromising photos because a Trojan horse was previously installed on the victim's computer. The attacker then blackmails the victim, either demanding a bitcoin ransom or threatening to release the photos on social media or share them with the victim's contacts.
The attacker exploits the potential embarrassment and humiliation the victim might feel from the exposure of these images. The aim is to stress the victim so they view the situation as urgent, pressuring them to pay the ransom promptly.
To elicit a quick response, the hacker generally gives the victim only a few days before releasing the compromising material.
To make the hacking claim more credible, the hacker may include passwords associated with the victim's email address that might have leaked in the past.
Seeing a password previously used across various accounts, the victim might believe their system has been hacked. However, obtaining such data from the dark web is easy. Just having this type of information does not confirm the email's legitimacy, but many victims don't realize this.
Another type of sextortion, similar to catfishing, involves creating a fake attractive profile on dating sites or apps and building trust with various contacts.
The hacker's goal is to gradually gain intimate access and obtain compromising photos. These images are then used for blackmail, as described earlier in the article.
However, this method is less profitable and less popular as it takes longer than simply sending mass phishing campaigns.
Nevertheless, victims face the real risk of seeing personal photos or information made public.
2 – Examples of Sextortion Emails
Below are two examples of sextortion emails.
These messages are crafted using social engineering, leveraging psychological triggers that disrupt the victim's reasoning and pressure them into paying the ransom.
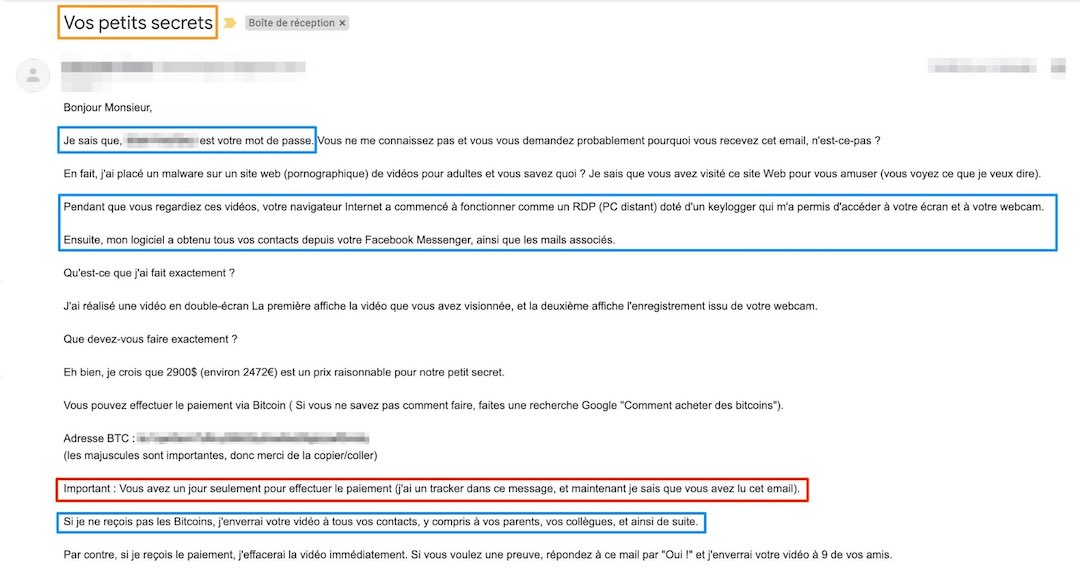
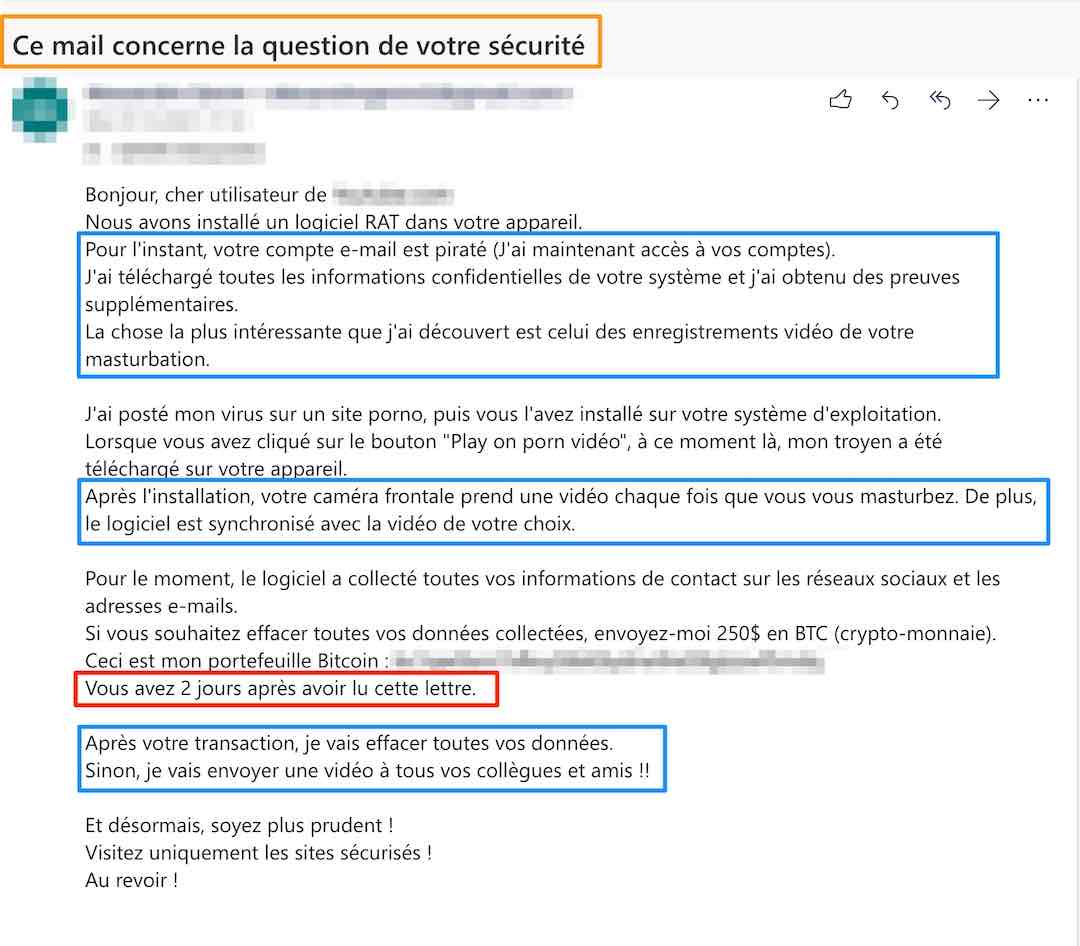
Curiosity is generally used in the email subject to entice the recipient to open it. Other elements generate stress and fear; the potential humiliation forces the victim to resolve the issue privately without consulting others.
To prevent the victim from thinking too much, discussing with others, or realizing the scam, hackers often add urgency to their messages, setting a 1 to 2-day deadline, indicated here in red.
3 – How to Protect Yourself?
The first line of defense against this attack is a good antispam filter. These emails usually follow a detectable pattern that many filtering tools can identify.
You need to keep your antivirus, firewall, and system updated to maximize your device's security.
It's better to be safe than sorry: consider buying a webcam cover to prevent it from activating without your consent. However, remember that the microphone can still capture data without indicating its activity.
If you're a sextortion victim, don't panic. Unless you've shared compromising content, the attacker almost never has these recordings. They solely use social engineering techniques to manipulate and press you into paying the ransom. It's essential not to pay, stop all contact with the scammer, and report the email as fraudulent.
If the hacker reveals any of your passwords, change them immediately, ensuring you choose strong ones.
The CNIL (National Commission on Informatics and Liberty) advises taking a screenshot of the received message and reporting the scam on the "internet-signalement.gouv.fr" website.
In general, avoid accepting message offers or connection requests from individuals you don't know or whose identity you cannot verify. Also, be wary of sharing confidential or intimate information online.
Furthermore, talk about it. Raise awareness among your acquaintances about this practice to prevent them from getting trapped.
Conclusion
Like all manipulation-based attacks, being aware of their existence helps thwart them.
Once you understand their methodology, these attacks become ineffective.
Regardless, always remain vigilant when reading emails with financial requests. Report any suspicious exchanges to combat these scams.

