In March 2021, the top 10 dating sites in France recorded 46.4 million visits, according to a study conducted by monpetitdate. Dating apps have become genuine tools for finding one's future partner. However, these apps are not used solely for benevolent purposes.
Catfishing (or catphishing), a variant of phishing, involves using a false online identity to extort money or personal data. Hackers carrying out this scam seduce their victim over time and use social engineering to establish a climate of trust with the aim of lowering the victim's guard.

Although many cases of catfishing involve only individuals, it can also be used to carry out attacks against companies.
In this article, we will revisit the "Mia Ash" attack carried out against Deloitte before discussing protection techniques.
1 – Catfishing can be a threat to your business
OilRig, a team of Iranian hackers, assumed the identity of Cristina Mattei, a Romanian photographer. Using the information and photos of Ms. Mattei, OilRig created a fake Facebook profile under the name Mia Ash, a supposed photographer living in London.
In July 2016, a cybersecurity employee at Deloitte, a major consulting firm, received a message on his Facebook account from the infamous Mia Ash, indicating that she would like to discuss their respective work.
OilRig then built a relationship, establishing a connection by, for instance, complimenting the employee on his various skills. It was after several weeks that the victim offered his help to the fake profile to create her new website. Mia then sent him a file supposed to contain her photos.
This file actually contained PupyRAT, malware designed to extract login credentials to Deloitte's system.
Fortunately for Deloitte, the software failed to connect to the company's systems, preventing a data breach.
However, Deloitte revealed that it had been the victim of another attack targeting its servers hosted by Microsoft Azure during the same period as the "Mia Ash" affair. It can therefore be assumed that the two attacks are related and that one resulted from the other.
2 – How to Spot a Catfish?
Before helping you identify a case of catfishing, it's important to emphasize the complexity of detection due to the dating context.
This is very different from a sextorsion attack.
In this situation, it's normal to want to learn more about the other person and for some personal information to be exchanged. However, if several of the points below are present in your conversation, it's highly likely you're dealing with a scammer, so stay alert!

Request for personal information
During an exchange on a dating app, it's logical to ask for more information about the person you're speaking to.
However, a scammer will generally request personal information quicker than in a regular conversation.
Your salary, your address, your email, or login credentials are unusual requests that should alert you.
No in-person or video contact
A malicious individual will always avoid physical or video contact as it would expose them more easily, so they will always cancel these meetings at the last moment. Of course, a real person might have an unexpected issue preventing them from meeting you, but when cancellations are repetitive, it's a sign of catfishing.
Too good to be true
If you have nothing but common interests, and your interlocutor agrees with everything you say, it's probably too good to be true. Moreover, a profile that displays all the signs of high social success, an attractive appearance, and significant wealth is likely fake.
Excessive flattery
A low-level scammer will lack social intelligence and will flatter you excessively.
If someone declares their love for you during the first or second exchange, it's wise to question the authenticity of their statements and their identity.
Lack of consistency in some statements
Depending on the attacker's level of preparation, their fake identity and pretexts may contain inconsistencies. Pay attention to the details and don't hesitate to confront your interlocutor with their contradictions.
Request for Financial Aid
Asking for financial help is the end goal for a vast majority of catfishing attacks targeting individuals. Generally, it's obvious that sending money to a person in this context is a mistake and a strong warning sign.
Incomplete Digital Identity
Often, profiles created for catfishing lack "depth." They are only present on the platform used to carry out the attack.
Search for the individual on other social networks; if you get no results, and no secondary accounts like LinkedIn are linked to the profile, then you might be dealing with a case of catfishing.
Moreover, these profiles, representing a form of digital identity, provide you with context and allow you to check the consistency of the information exchanged during conversations.
Person Alone in Photos
If your contact's profile contains only photos where they are alone, with no other people in their pictures, it's a suspicious profile. Indeed, group photos would require inventing a relationship with each person present. So, it's easier to impersonate someone appearing alone. Additionally, if the profile features only professional, magazine-worthy photos, that's another indicator of the potential danger of your contact. A genuine profile would necessarily have more "natural" photos.
File Transfers
Another purpose of this type of attack is hacking the connected device. Whether in a corporate environment, as with the Mia Ash case, or for an individual, it's straightforward to transmit malicious files.
Sending an archive with photos or installing a program to make a video call are examples of potentially dangerous file transfers.
3 — How to Protect Yourself from Catfishing?
We have seen various helpful signs to identify catfishing. Now, we will look at the steps to take to protect yourself from these attacks.

Reverse Image Search
Take a screenshot of your contact's profile picture. Then, conduct a reverse image search on Google, TinEye, or PimEyes to find other sources of the image. Typically, the profile photos of catfishing accounts belong to other existing profiles.
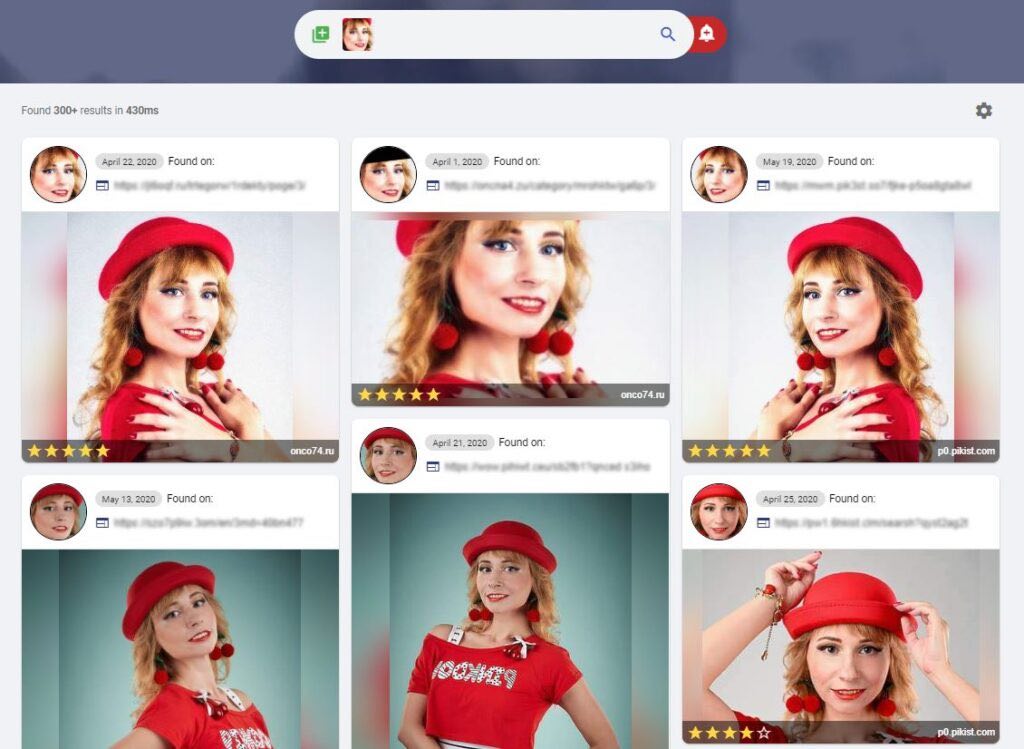
Preview of the PimEye interface
However, be cautious as it is increasingly easy to create profile photos using AI-based generators like thispersondoesnotexist.com.
Asking for Photos and Videos in Different Contexts
Although technologies like deep fakes exist, the more you ask for photos in various contexts, the more costly it is for the attacker to stay consistent. Ask for videos of your contact or group photos. These elements are harder to produce than simple profile pictures.
Intuition
If you have doubts about the identity of your correspondent, trust your intuition. A bad feeling is never without reason and could prevent you from finding yourself in a dangerous and unpleasant situation.
Avoid Sending Money to Strangers
It goes without saying, never send money to someone you've never met in person. Also, avoid sharing too much personal information in your conversations with a stranger. This will reduce the chances of getting scammed.
Compartmentalization
One of the basic rules of cybersecurity is not to mix uses. The hardware (computer, phone) as well as the sites and email addresses you may use for your personal activities and discussions should be different from your professional equipment and addresses.
Thus, the infection of a personal computer with malware from catfishing cannot spread to the company's network.
Software Protections
The first step to avoid infection is to be very cautious with the files exchanged on these platforms.
In the case of malware transmission, having up-to-date antivirus software and a firewall could potentially limit the impact of the attack by detecting the malware or any suspicious network activity it causes.
Report
As with most cyberattacks, reporting the scam helps authorities catch the hackers. It's therefore important to report fake profiles or scam attempts on applications or social networks.
You can also report the attack on signal-spam.fr, an online platform where the CNIL (National Commission on Informatics and Liberty) will handle your report.
Conclusion
Catfishing is an attack often considered as "obvious" to identify. However, as with phishing, even individuals who are aware of it can be fooled.
Proof of this is the Mia Ash case, where a cybersecurity employee was deceived.
It's important to communicate about these attacks to raise awareness of the risks they pose.
By being aware of potential dangers, you will be more vigilant on dating apps and thus more protected.

