Phishing comes in different shapes and forms.
This means you have a lot of choices when it comes to creating a phishing simulation, and most companies get confused as to what type of simulation they should run.
In this article, we'll provide you with a simple way to select the right simulation for your needs.
What's your goal?
It's very important to define the goal for your simulation.
If you're looking to evaluate and audit your company, understand how it would behave when facing an attack, you will need to create a very realistic simulation. As realistic as possible, in fact.
If you're looking to train your employees, foster safer behaviors, you'll want to create campaigns with adaptive difficulty and embedded microlearning so they can learn from it with instant feedback.
These are two different things, and mixing them won't yield good results: realistic campaigns won't really train people, and training campaigns, because they will have some obvious flags and a tight feedback loop, won't be realistic.
The Realistic Simulation
The realistic simulation is there to evaluate your security posture, your employees susceptibility to current attacks, executed as realistically as possible.
Realistic Scenarios
I know a lot of simulation platforms compete on the number of scenarios they have.
It's of little relevance for this type of campaign. You want to use a mix of scenarios that represent the threat landscape.
Recent research by Slashnext is showing this mix:
- 22% of attacks are link-based
- 12% of attacks are file-based
- 68% of attacks are text-based
Each category has a few variations but if you look at the threat reports from various secure email gateways, you'll often find the following:
- for link-based credential harvesting scenarios about a password reset, suspicious activity, or a document share on Office365 or Google Workspace — as these accesses yield the best ROI for attackers.
- for attachment attacks it's usually a Word or Excel document with Macros.
- for text-based attacks it's usually a CEO fraud or BEC type of attack, with a conversational approach.
This can be tricky if you're using older generation simulators, so if you can't find a way to do this with your current solution, feel free to request a demo and have a look at what we do.
Realistic Execution
Having the right scenarios or threat mix doesn't make your campaign realistic.
You also need to execute realistically.
This is tricky, because attackers will select a few targets and be very discrete, while you want to evaluate everybody, as just one weak link can give attackers an initial access.
So here are a few things you can do to maximize realism.
We've already sorted out diversity: you won't send one scenario to everyone but use a threat mix that is coherent with the real threats out there.
Regarding timings, you need to spread the campaign so that people will receive the phishing emails randomly, at realistic timings.
Once you've done all of that, you have a realistic simulation in your hands.
The Training Simulation
The phishing training simulation needs to... train people.
We need it to create learning moments and be adapted to your employees' level.
Feedback loop
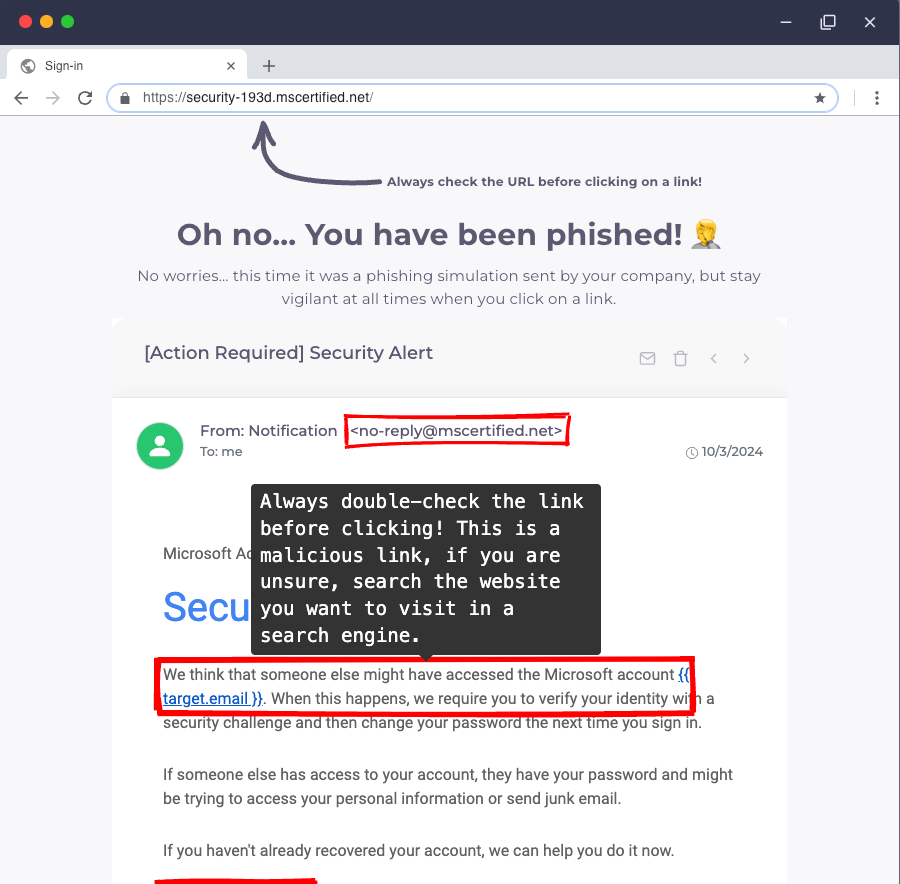
Contrary to what we want in a realistic attack simulation — no feedback loop to give it away — in training, you want to have a very short feedback loop.
As soon as an employee makes a dangerous action, you want to provide feedback.
The goal is to leverage the emotional reaction people get from learning they've been caught to make the learning moment "stick".
So you want the feedback to be immediate, and contextualized.
The best way to do so is to show what we call an "email replay" showing the phishing email and the clues they should have seen while opening it.
Difficulty
In realistic simulations, you want to crank the difficulty all the way up: attackers won't leave breadcrumbs so they can be detected.
In training simulations, it's a bit different. You want to adapt the difficulty to the level of your employees.
If it's too hard, they might get discouraged.
If it's too easy, they might get bored and not even consider reporting the simulated threat, or worse, they might become overconfident and pose a risk down the road.
Diversity
Now, although you need to stay fairly close to the threat mix, it's more important to create a high level of diversity in training than in realistic simulations.
The goal is to train people with a lot of different types of phishing, in many different settings and scenarios so they can focus on the common point sof all phishing and social engineering attacks : the deception mechanisms.
This is when the many different variations of scenarios are handy.
It's very unlikely that an attacker tries to hack your employee's accounts for a very obscure internal tool you're using.
But it's a good pretext to provide training while pretexting a security issue with the software that needs immediate attention.
Putting it all together
Over the year, we recommend you combine both types of simulations, with a majority of training campaigns — as training brings more value and takes time — when realistic campaigns and few realistic campaigns to measure the results of the training.
Arsen does this on autopilot, with all the new generation attack vectors. We leverage generative AI to build realistic conversational attacks and deploy these across different vectors, from email to vishing. Click here to request a demo.

