There are many ways to improve your defense against phishing attacks.
It has been for years and is still the main initial access vector in successful cyberattacks.
There are many defense mechanism you can deploy to protect your company against phishing, one of them is using phishing simulations.
Phishing simulations, if done properly will help harden the human layer of your company, and this is what we will see in this article.
Initial configuration
It seems obvious but before doing anything with your phishing simulation platform, you'll need to make sure it's properly configured.
- Delivery: make sure you can send fake phishing emails to your infrastructure without being flagged, quarantine or receiving fake clicks from security systems.
- Employee sync: be it from a CSV import or an AD sync, make sure you have all your employees synced to your phishing simulation platform.
- Reporting button: you want to be able to track who's reporting an email as suspcioius. This is a good behavior you want to track and foster.
Initial assessment
Once your phishing simulation platform configured, if you have never done a phishing audit before, you need to assess the situation.
You need to run a phishing simulation that will serve as an initial assessment.
These simulations will have one purpose: observe the behavior of your employees in a very realistic attack.
You'll want a stealthy execution, as close to current attacks, without embedded learning elements to avoid employees talking between them and creating an artificially high score.
So here are some parameters you should follow for this first campaign:
- Use popular phishing scenarios (password reset, document share, security alerts, fake invoice, etc.). Don't go for the very specific and targeted scenario just yet but use multiple scenarios for this campaign as you don't want everyone receiving the same scenarios.
- Use high difficulty scenarios don't use specific training scenarios with typos or obvious flags, stay as realistic as possible
- Spread the campaign over time to be discrete and if you can, use advanced scheduling to target people randomly at the end of the business day
- Target everyone at this stage we want an assessment of the whole company, groups will come handy in the next phase.
This will provide you with data to conduct the simulations that will actually help you improve your security posture: the phishing training ones.
Improve behaviors with phishing simulations
Now that you've run a realistic simulation and have a better understanding of your employee's reaction, you can start creating phishing simulations that will move the needle.
For this, you need to combine several factors.
Group your people
There are two important properties to use to group your employees :
- Their level, based on how they faired in your initial assessment
- Their context: depending on their job title, position, exposure, you will train them differently
Depending on your phishing simulation solution and targeting parameters, you might need to create separate lists or campaigns.
In Arsen we use dynamic groups that will use filters to group people depending on their properties: AD groups, level, number of simulations they've participated in...
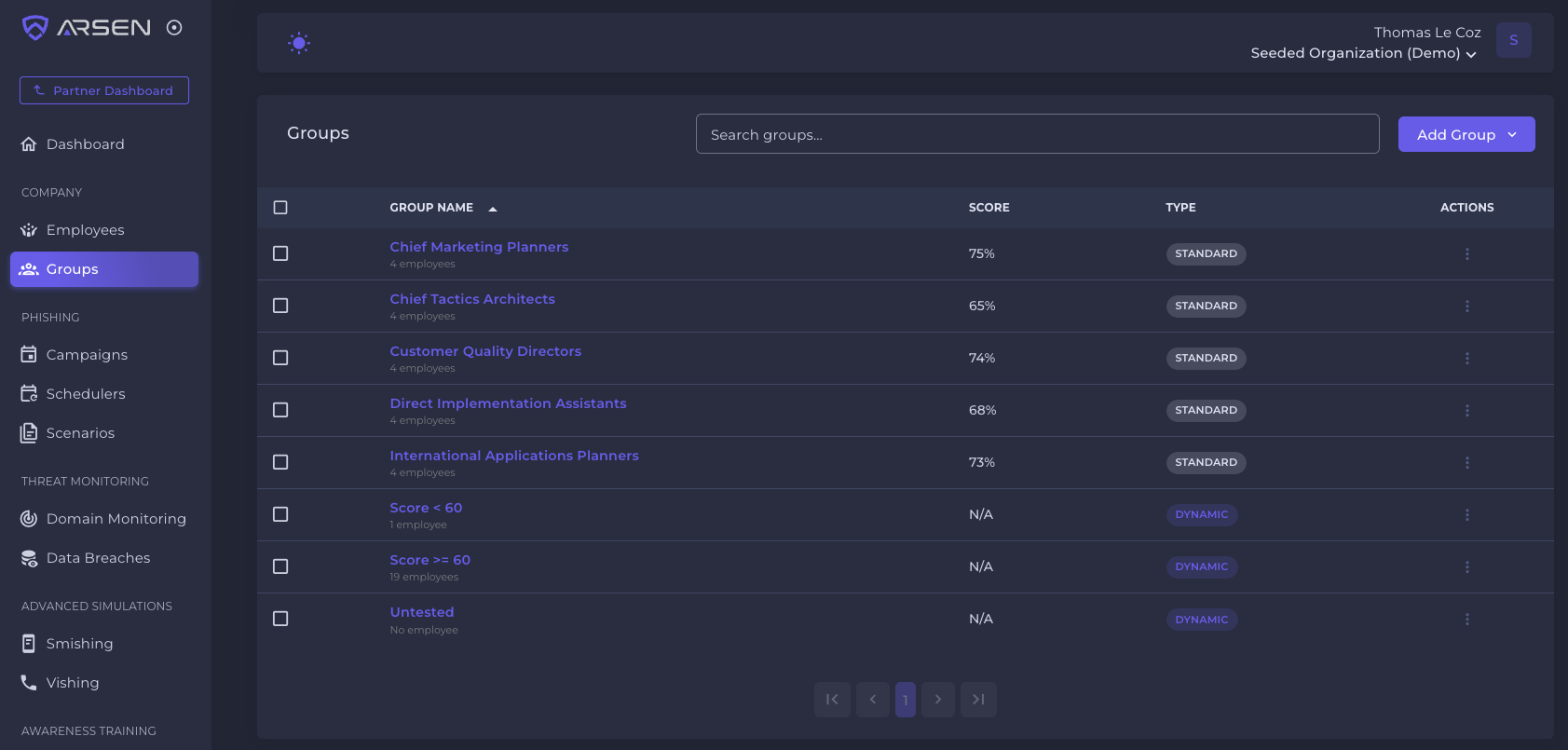
This allows a much better targeting to take into account the following points.
The right frequency
Too many phishing simulations might deter people from learning and have adverse effect.
The content might be ignored or people might even click voluntarily to as a sign of protest.
On the other hand, if you don't run enough simulations, people will lower their vigilance over time, and you won't benefit from it.
At Arsen, our platform targets people with a lower security score more frequently so that they can build reflexes and people with a higher score less frequently to just maintain them.
The right level of difficulty
Not all phishing is created equal. You need to take into account the difficulty level.
So to really improve behavior, you need to create progressive difficulty and use your groups to target them accordingly.
Our platform targets people with a low security score with a lower difficulty, so they can catch clues such as an obvious domain name, a typo or a broken design and improve to gradually more complex scenarios.
Higher security score employees will be targeted with much more complex and realistic attacks, to keep them on their toes.
The right context and scenario diversity
If you train your employees with the same scenarios over and over, you will create specialization: they will learn to detect your simulations, not the overarching principles of phishing and social engineering.
This is why you need diversity and why having different scenarios is key: you can use various scenarios to the same effect.
This is when having groups by job title or business unit can come handy: your sales will be more likely to click on a CRM notification but will probably ignore a PDF resume, when your HR people will do the opposite.
At Arsen we not only use this but also a healthy dose of AI to help provide more targeted diversity to our simulations.
The platform can even create unique conversations with each one of your employees, trying to trick them into clicking on a phishing link.
Instant Feedback
Because learning that you've been phished, even if it's a fake phishing and part of a training simulation, creates a strong emotional reaction.
This reaction can be leveraged to make sure people retain more knowledge.
This is why it's the best timing to show them a very short e-learning page.
At Arsen, we replay the email sent and highlight the clues that should have been seen by the employee so they can better detect them in the next campaign.
Automating everything
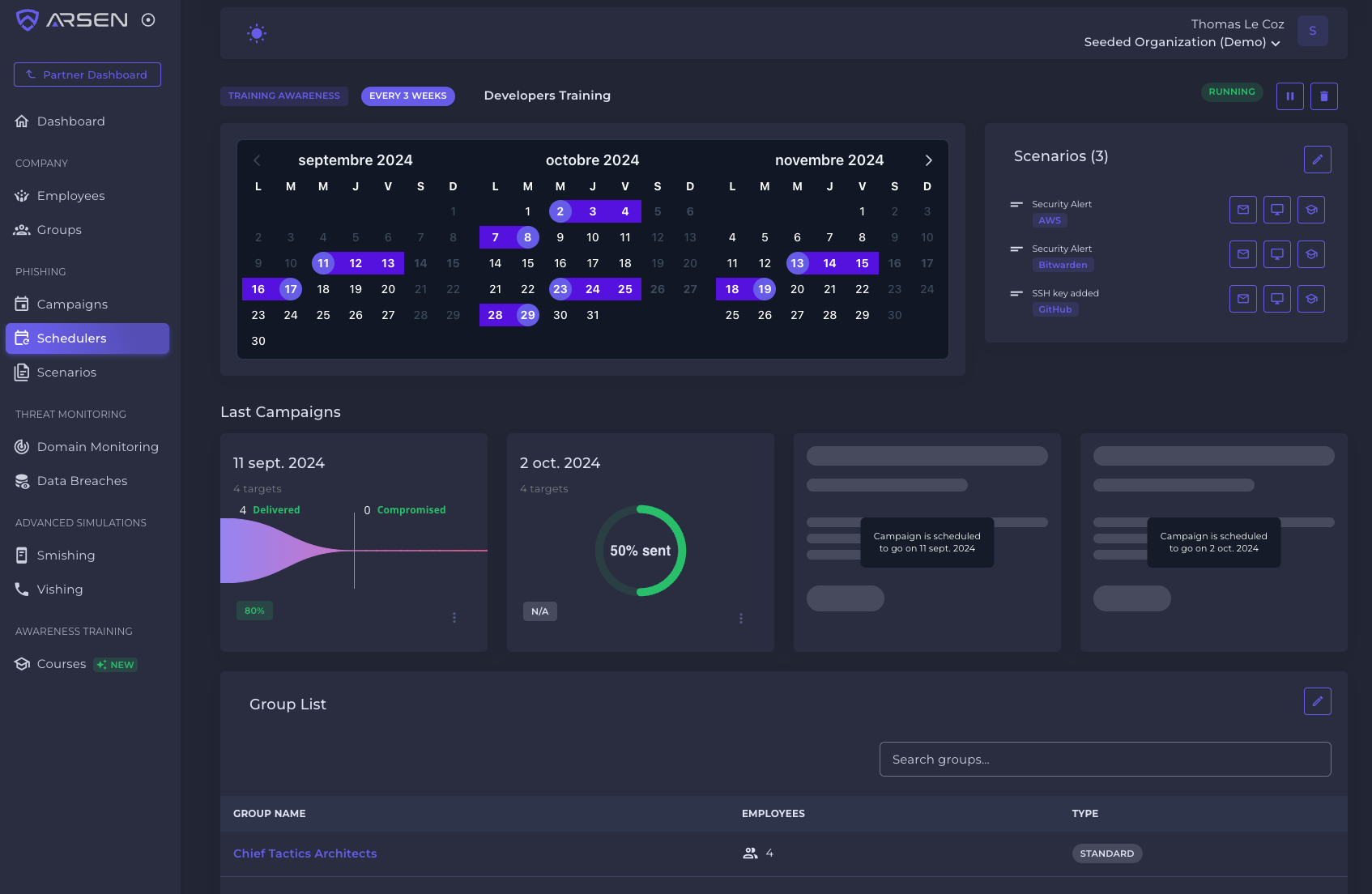
One phishing campaign won't change anything. You need recurring, adapted, diversified training campaign to foster new behaviors for your employees.
Keep the frequency to one campaign a month isn't easy but if you have the right platform it can be done in just a few clicks.
Conclusion
In this article, I've shown you the steps needed to use phishing simulation as a protection tool, not just an audit or compliance tool.
There are many finer points that can be done to protect your companies: checking for leaked credentials, password entropy or even detect unknown endpoints.
We do all of this as well, but this will be explained in another article.

