A paradox has captivated me for several years.
Every professional I talk to agrees on the significant risk posed by human factors. The internet overflows with statistics linking initial access breaches to employee behavior in corporations. Yet, this critical issue receives only a fraction of the resources devoted to other layers of security.
“Awareness” is often demoted to a mere compliance issue.
We rush to implement solutions that merely check the boxes needed to comply with our cyber insurance requirements, ISO standards, or corporate security policies.
My theory is that human behavior remains an enigmatic black box - challenging to predict, quantify, and definitively improve.
So why invest considerable amounts of money — and valuable time — in training employees?
We understand that with enough persistence and creativity, it's feasible to deceive an employee and exploit them as a gateway for breaches.
Consequently, we pour substantial resources into subsequent security layers, as if these cannot also be bypassed with some ingenuity — or a clever ChatGPT prompt.
Hence, the motivation for this article.
My goal is to advance the discussion on this topic and, as always, to enhance our collective resilience against cyberattacks.
Understanding Defense in Depth
Defense in depth is an approach to cybersecurity where a series of security measures are implemented across an information system.
The aim is to ensure maximum protection by creating multiple layers of defense that attackers must overcome.
If one layer is compromised, the subsequent ones should thwart the attack and preserve the system's security.
That's why we don't (or shouldn't?) rely solely on installing basic antivirus software on a device.
No single layer is unbreakable, but the accumulation of defenses makes an attack much more complex and less profitable for the cyber attacker, thus making it less likely.
That’s why we see protections at every level:
- Physical: access badges, safety management, building security, etc.
- Technical: particularly relevant in cybersecurity
- Administrative: policies and procedures, insurance, and so on.
Common protections at the technical level include:
- Access and identity control
- Data encryption
- Endpoint surveillance and protection with EDR solutions
- Network surveillance and protection with firewall and NDR solutions
- Backup systems
The layers and solutions vary depending on each individual's context, as well as the budget and maturity level of the company or organization.
What's crucial is understanding the implications for an attacker.
To compromise a target with ransomware, considering the above protections, an attacker must compromise one or multiple access points, evade the surveillance of EDR and NDR, and take control of the backup system.
Each of these tasks is potentially risky, noisy — creating a risk of detection and at least a partial failure of the attack — and time-consuming, thus expensive.
Securing the Human Element
To secure the human element, in addition to technical protections that limit human exposure to threats, we now have "awareness training".
Protection solution to limit exposure: Among the technical protections that help limit employees' exposure to threats are tools like anti-phishing filters, which filter out malicious emails, and solutions like proxies that block access to malicious, unauthorized, or simply unknown websites.
The bet is that someone who is aware of cybersecurity, who better understands the risks and stakes, will be more capable of slowing down an attacker and contributing to the security of their company.
Hygiene and Awareness
Most awareness efforts focus on creating a culture of cybersecurity and respect for cybersecurity hygiene rules.
A favorite analogy in the world of awareness is road safety, particularly the adoption of seat belt use.
Thanks to numerous communication campaigns, a legal framework, and interventions by road safety professionals, courses, etc., over a period of 30 years, motorists have developed the reflex to buckle up their seat belts.
The goal of cybersecurity awareness operations is, therefore, to instill safer behavior regarding the use of information systems.
There are many solutions available, including the Information Hygiene Guide and the SecNumAcademie of ANSSI, which you can access for free.
Behavioral Training
At Arsen, our primary goal is to foster more secure behaviors in response to manipulation attempts.
These attempts use social engineering. They manipulate employees, leading them, unwittingly, to engage in risky behaviors.
Awareness, when based solely on theoretical knowledge, often fails to translate into practical situations where the employee is being manipulated.
Of course, everyone agrees that one shouldn't click on a link in a malicious email.
However, a phishing email — or any social engineering attack — exploits our heuristics and cognitive biases to make us perform potentially compromising actions despite our knowledge.
By employing well-known psychological techniques, it's possible to improve behavior, even when faced with manipulative tactics.
Returning to the road safety analogy, at Arsen, we focus on the practical test: knowing the rules of the road is necessary but not sufficient to drive a vehicle.
After passing the theory test, one can't immediately drive a Porsche, handle the clutch, 7 gears, or merge onto a highway, even if they made fewer than 5 errors on the theoretical knowledge test.
What's important is behavior behind the wheel: are we truly capable of driving safely and traveling from point A to point B without endangering ourselves and other road users.
There's No Such Thing as 100% Security
"We can never make a human invulnerable."
True, but just as an attacker might not get detected by an EDR, bypass MFA protections, or clone access badges, that doesn't justify not deploying and properly implementing these security measures.
In other words, just because someone can pick your front door lock doesn't mean you don't lock it when you leave for work in the morning.
The principle here is the same: we need to add a layer focusing on human conditioning in our defense-in-depth strategy.
Integrating the Human Element into Your Defense-in-Depth Strategy
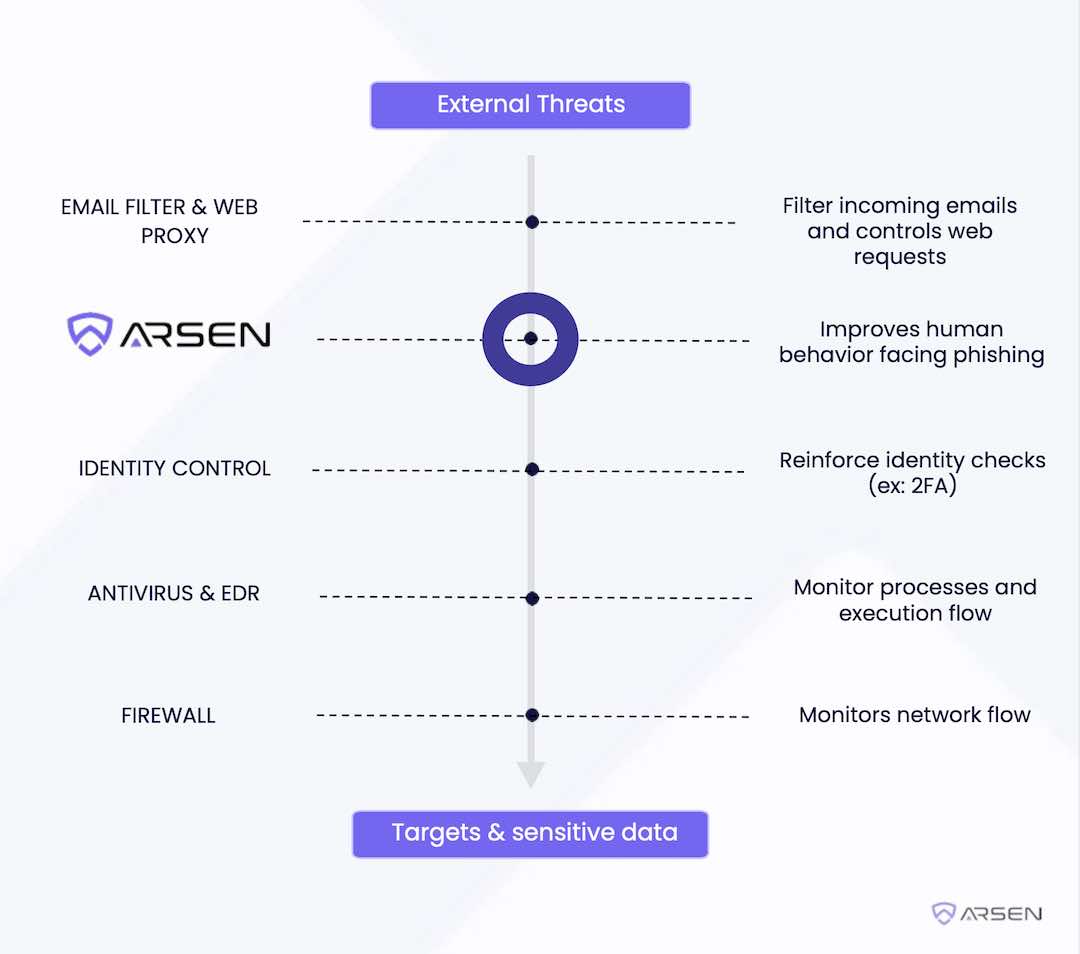
Given that humans play such a crucial role in most kill chains, it's essential to integrate them into your defense-in-depth strategy.
Kill Chain: The cyber attack kill chain is a model describing the stages that cybercriminals typically follow when launching an attack against a target. This model was developed by Lockheed Martin and is used to identify and prevent cyber attacks.
Considering Humans as an "Asset"
Humans are an integral part of the information system. They interact with various services, have privileges, a level of resilience, and are consistently exposed to the external environment.
Failing to recognize this is to overlook a significant portion of your attack surface.
Implementing an Observation Solution
A unique aspect of employees is that they have lives outside the company — hopefully, unlike your terminals and servers.
Therefore, certain actions or equipment not directly related to your employees' professional activities can compromise the security of your information system.
For example, the use of shadow IT can be a source of cyber attacks. If an employee uses a potentially infected personal phone to connect to professional services, they might fall victim to an infostealer, which remains undetected and allows initial access.
Shadow IT: Shadow IT, or ghost IT, refers to the systems and IT solutions used within an organization without the official approval of IT departments. This can include the use of software, applications, services, and equipment not sanctioned by the company's IT department.
Infostealer: An infostealer is a type of malware designed to steal personal or sensitive information stored on an infected system. This can include details such as usernames, passwords, credit card numbers, browsing data, and other identification information.
That's why it's crucial to observe the actual, tangible behavior of employees.
At Arsen, for example, we offer “the hacker's point of view”. We provide a visualization not only of behavior in response to potential or confirmed threats but also of the equipment used when an employee is targeted in an attack.
Reinforcing Employee Security
When a vulnerability is detected, a system requires an update, or an asset is compromised, a series of operations is necessary to restore a higher level of security.
Similarly, after assessing the resilience level of employees, it's important to improve it.
I won’t delve into methodological details, but the two operations — assessment and training — are distinct.
Where software is patched, behavioral conditioning principles must be applied to employees to create reflexes that will serve them not only in their professional lives but also personally.
Cognitive and behavioral sciences are a major asset here and should form the foundation of the methodologies employed.
Integration with Existing Tools Since we can't just bury our heads in the sand and leave the work to subsequent security layers, it's necessary to incorporate these elements into your security tools.
That's why your tools for better managing human risk should be able to integrate with your SIEM or at least communicate with your SOC or cybersecurity service provider.
Conclusion
Despite the plethora of solutions addressing human risk in cybersecurity, there's a huge room for improvement and necessity.
Rather than viewing awareness as merely a compliance issue, observability solutions and behavioral conditioning must be integrated into the layers constituting defense in depth.
Besides awareness from decision-makers, a significant responsibility also lies with the publishers of awareness solutions.
We need to enable easier and quicker integration of solutions into already deployed equipment.
We must also introduce greater rigor in measuring the effectiveness of the proposed solutions and methodologies.
Merely measuring a click rate during phishing simulations does not in any way provide a better view of employees' resilience levels.
Phishing remains the most used vector for initial access today and with great success; it's high time to address this issue correctly.

