At Arsen, we love Gophish.
It’s by far the most comprehensive open-source solution for deploying phishing, whether for evaluation, training, or research purposes.
That being said, GoPhish has numerous limitations that add significantly to the cost of use.
Whether for your business or your clients, we are going to discuss three aspects where Arsen can help you save a considerable amount of time and ensure reliability for your campaigns.
Infrastructure Deployment and Maintenance
When it comes to setting up your phishing campaign, GoPhish allows for great flexibility, but at the cost of some deployment effort.
Indeed, you have to configure an email sending server on one hand, and quite often handle the SPF, DKIM, and DMARC settings to maximize your deliverability.
You will then have to create a sending profile for each domain and identity you wish to use in your campaigns.
The same goes for the web server: at a minimum, you need to configure a domain and its SSL certificate to enable serving credential theft pages from your GoPhish infrastructure.
Once your phishing infrastructure is deployed, you will then have to maintain it and keep it alive against various inspection tools, including Google Safe Browsing.
This work is time-consuming, substantial, and may lead you to have to restart certain phishing campaigns that could have been compromised.
At Arsen, these deployments are fully automated.
You benefit not only from more than 60 default attack domains, but you can also import your domain names by simply changing the nameservers.
Email configurations — including SPF, DKIM, and DMARC — and web configurations — including SSL — are automatic.
We also have our own traffic filtering technology to detect and filter inspection tools like Google Safe Browsing.
Campaigns Realism
From a certain workforce size to test, creating realistic phishing campaigns becomes more complex.
Indeed, you cannot send 100 people the same email, with the same email address, and the same links and credential theft pages.
No. You want maximum variability among these emails to prevent the repetition of the same scenario from sounding an alarm among colleagues or worse, leading to the detection of simulations and not real threats.
However, creating a phishing campaign with multiple senders, varied scenarios, and different domain names is a very time-consuming task.
Without going back to the infrastructure deployment, you will have to create a campaign for each scenario and group on GoPhish.
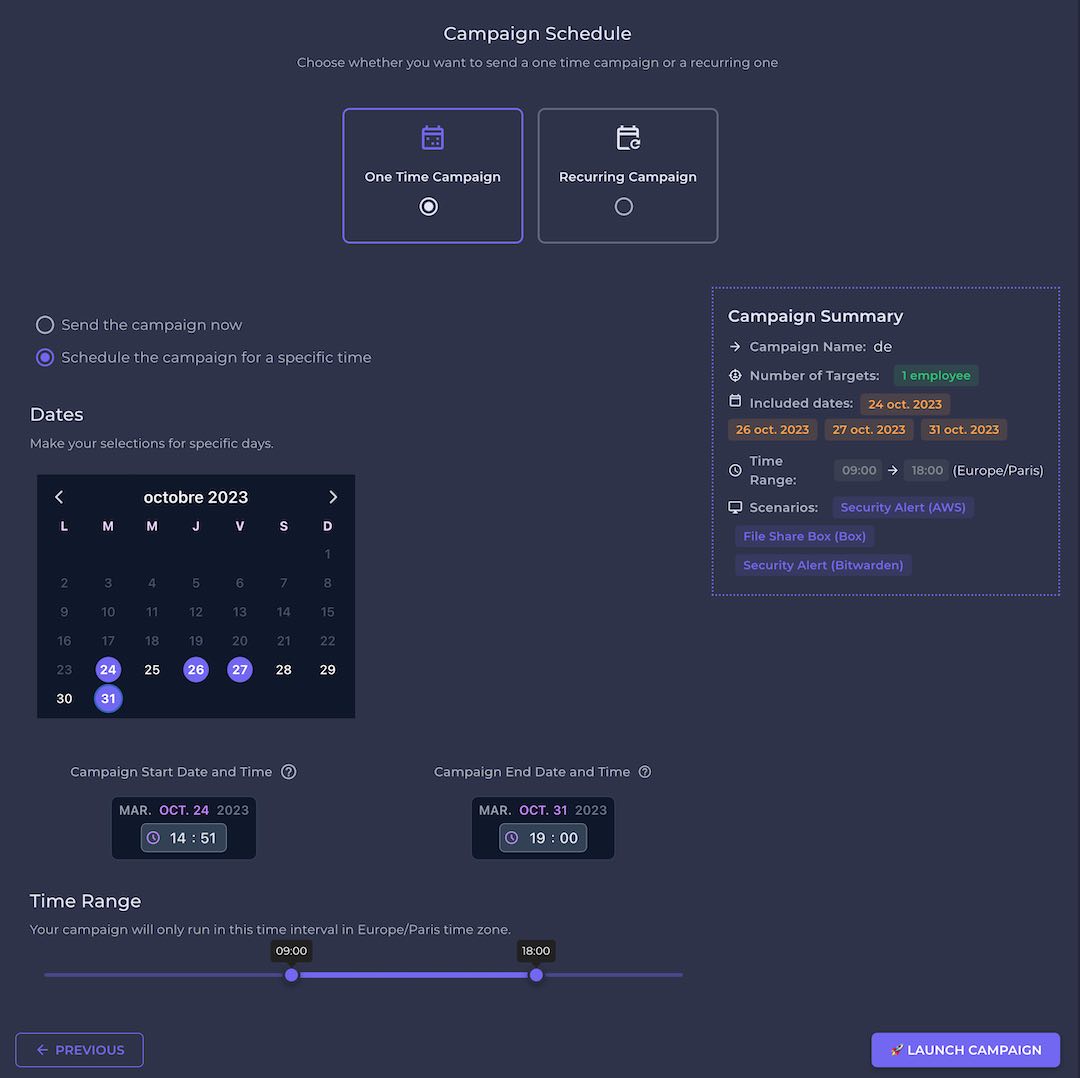
The same goes for distributing campaigns over time, on specific days. Choosing whether or not to send on weekends, with a pseudo-random distribution of sending dates, is extremely complicated (if not impossible) with GoPhish.
Faced with these limitations, we have integrated multi-scenario campaigns into Arsen, allowing the creation of phishing campaigns with scenarios randomly distributed across all targets.
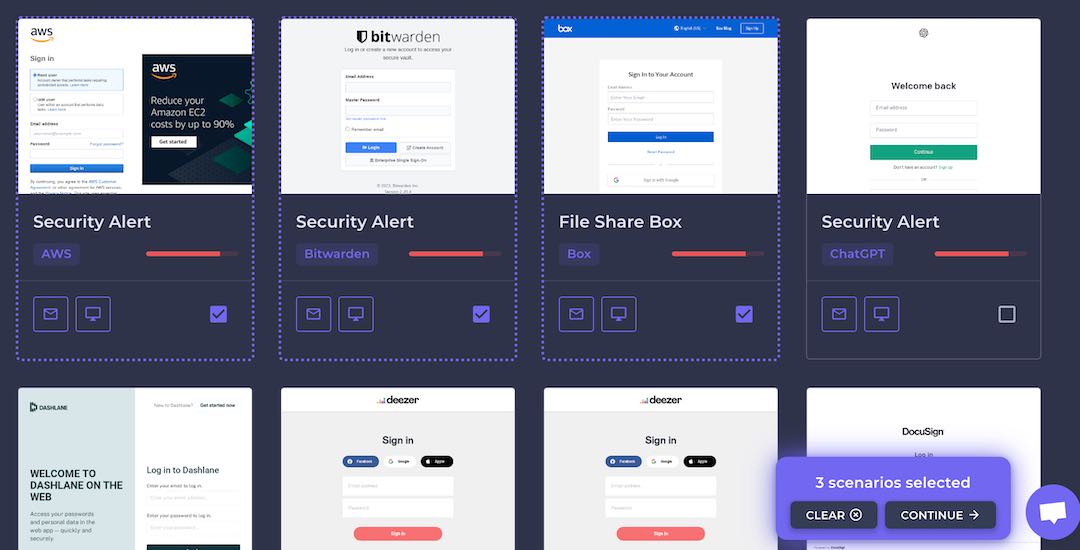
We also developed a campaign scheduler that enables the distribution of emails according to a specific calendar.
The realistic execution of phishing campaigns is key, whether to assess or train employees' behavior in the face of attacks.
Advanced Reporting
GoPhish and many phishing kits provide the "basic" information of a phishing campaign: open rates when possible, click rates, and information input.
However, this leaves a lot of information unvalued.
Indeed, a phishing simulation attack offers a unique perspective on employee behavior and helps better understand a company's organic response to these attacks.
Our platform, in addition to standard indicators, allows:
- the deduction of a security score, taking into account the difficulty of the phishing emails sent,
- indexing of the devices detected during the opening of emails and phishing pages,
- measurement of reaction times between each step of the kill chain,
- calculation and measurement of password strength (entropy).
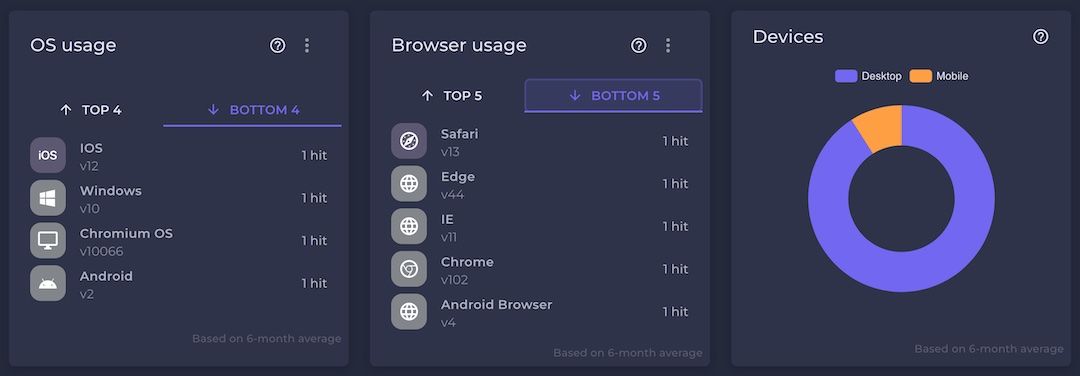
These reports utilize a larger amount of data collected in simulations to build a more accurate vision of the risk level and sensitivity of employees.
Conclusion
GoPhish remains a very good tool that makes phishing operations much more accessible to many specialists.
However, when it comes to conducting large-scale campaigns, the operational cost of performing realistic (and therefore useful) operations is very high.
Arsen Partner Opportunities
At Arsen, we're committed to helping our partners sell more and grow their businesses. We offer a variety of partner programs to fit your business requirements.
We are opening the doors of our platform to our partners to allow them to save time, improve simulation quality, and approach more complex accounts. Do not hesitate to contact us for a demonstration.

