Not all phishing emails are equal.
When I ask someone what comes to mind when they think of a "phishing email," the descriptions vary greatly.
Among these descriptions, the level of difficulty — that is, how difficult it is to detect the fraud — also varies.
Chris Hadnagy, an undisputed expert in social engineering and phishing, presents in his book "Phishing in Dark Waters" a classification of the level of difficulty of phishing emails.
In this article, we will talk about this classification and how, as cybersecurity experts, we can use it for educational purposes to improve our phishing risk awareness programs.
Level 1: the unlikely scam
Let's start with the lowest level of difficulty. These attacks are often detected due to the many clues they leave behind.
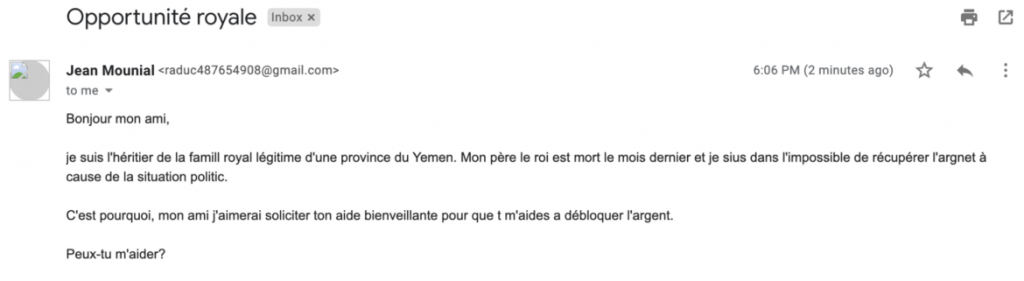
Phishing level 1 does not inspire trust.
Nevertheless, if they continue to be used, it's because they work. The production cost of such a campaign is very low, and it only takes a few victims to generate an interesting return on investment.
Several elements should alert you when encountering a level 1 phishing email:
- The message is often impersonal. It does not address the victim by their name and uses generic elements.
- It contains spelling and grammar mistakes, casting doubt on the professionalism of the sender.
- The message is very simple, and the pretext is highly improbable. For example, "you have inherited millions..."
- The scenario appeals to greed, fear, or curiosity, using very "basic" instincts to prompt action and compromise the target.
- The email contains links that lead to target pages, suspicious domain names, or attempts to initiate a discussion that quickly leads to extortion.
- The sender's address is unknown; we do not know the sender or their address.
All these elements make the threat easily detectable. Their obvious signs make these emails easily detectable by both technical protections and the recipients who receive these emails.
Level 2: the improved variant
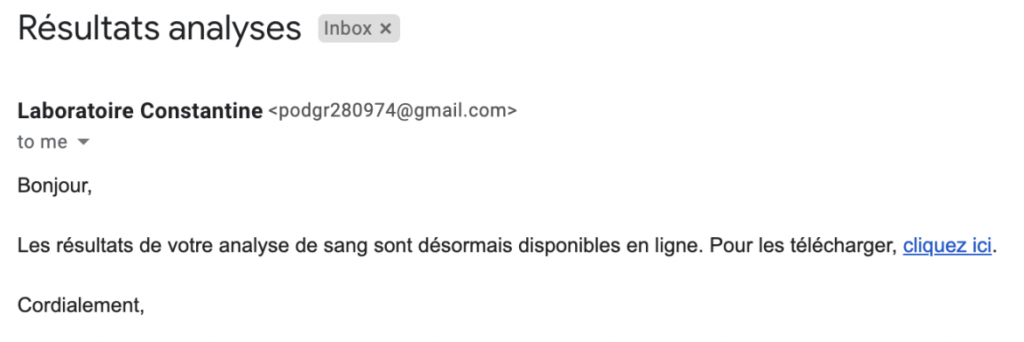
Phishing level 2 lacks context but is better constructed and disguised.
Where a level 1 phishing email is highly unlikely, level 2 phishing emails are slightly better executed:
- The spelling is much better.
- The scenario is somewhat more realistic, avoiding completely unrealistic pretexts.
However, there are still many signals that automatically raise suspicion in a somewhat trained employee.
- The email is impersonal, potentially indicating a mass email with little initial research on the target.
- The attack often uses links in the email body that point to domains that often appear illegitimate. A simple mouse-over of the link reveals these inconsistencies and identifies the email as fraudulent.
- The origin of the message always comes from an unknown sender from whom we do not expect communication.
- The pretext used is still very basic, appealing to curiosity, greed, or fear in a very obvious way.
Level 1 and 2 phishing emails are often referred to when trying to define or express what phishing is.
These emails are often basic scams or scams and are generally sent using mass emailing tools, without much sophistication.
However, the level of difficulty does not stop there, and there are levels where the attacks are more difficult to detect.
Level 3: the threat
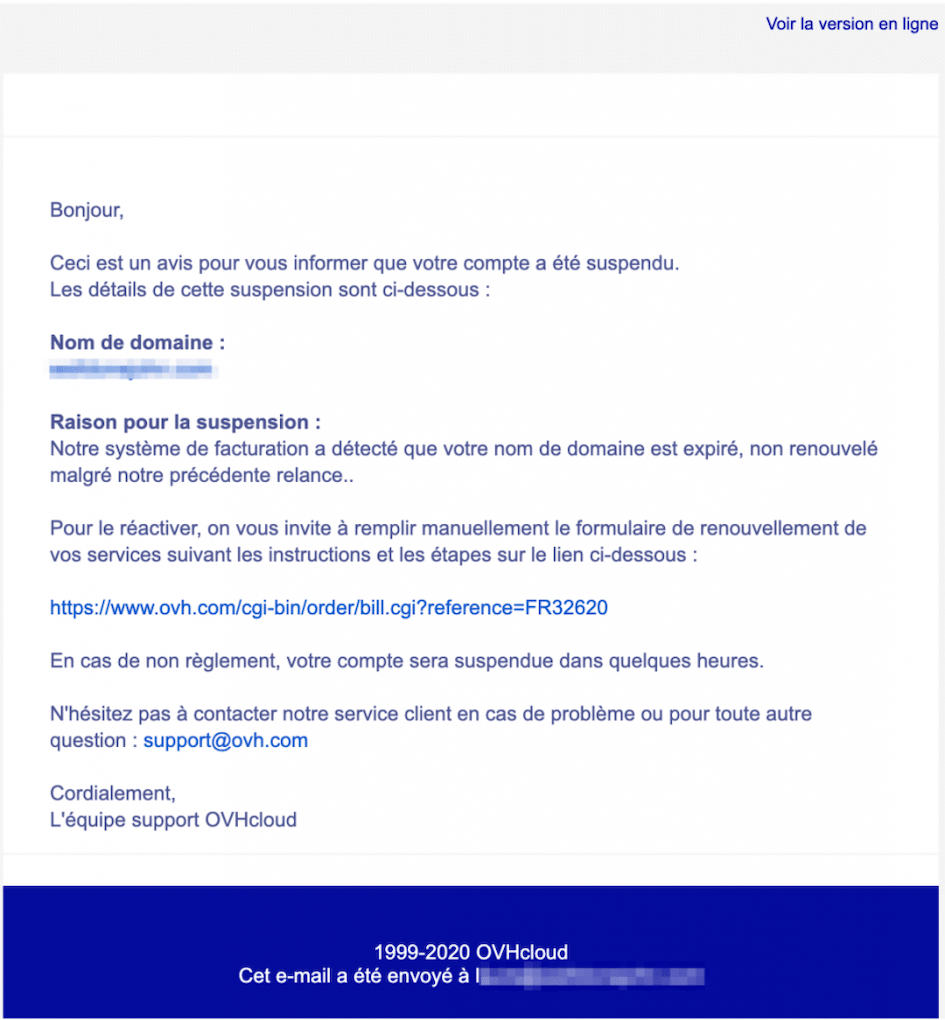
Phishing level 3 is often more convincing.
The next level is much more dangerous. It is still a relatively large-scale attack, and they often use a link to a rigged page. This creates a repetitive pattern that can be detected.
However:
- The communication is personalized. It contains data specific to the target, such as their last name.
- The spelling and grammar are good.
- The message and its pretext are realistic, consistent, and use fear or curiosity to prompt action. It is a contextualized attack.
- There is often identity theft that correctly reproduces the visual identity of the alleged sender.
- The sender appears legitimate.
The most striking example of a level 3 phishing attack is the phishing campaign targeting OVH customers.
In this scenario, the attacker uses the fear of website suspension, implying potential financial loss and reputational impact, to prompt action—the inputting of credit card information on a payment form.
Level 4: spear-phishing
Unlike the previous levels, spear-phishing does not have a specific pattern it reproduces.
The scenarios are personalized and contextualized, often even individualized. They are coherent, sometimes with branding, sometimes appearing to come from a colleague or authority figure, and they do not include any branding—the email then appears more personal.
These emails can include a corrupted link, an attachment, or simply instructions to perform a compromising action.
They are particularly difficult to detect and often only target a few people within the company, further reducing the chances of detection.
These emails are dangerous, and a good level of training in detection must be acquired to prevent cybercriminals from taking advantage of the opportunities they can create.
Practical application
At Arsen, our goal is to improve the detection and reporting capabilities of our clients' employees when faced with attacks, making them active protection elements.
To do this, we carry out two parallel actions:
- Simulating real-life conditions, during which we expose employees to phishing campaigns.
- Sending microlearning programs that allow them to quickly acquire usable skills in a real situation.
This notion of the level of difficulty allows us to adapt employee training based on their level.
This level is deduced from their behavior during the first simulations.
This allows us to improve pedagogy and create an adaptive learning experience where the difficulty is personalized based on each individual's level.
In short, our goal is not to continually trick employees, but to enable them to detect our simulations and follow the reporting procedures.
Using easily detectable emails can sometimes create a good initial detection experience and reinforce employees' investment in the training experience.
Knowing the average level at which all employees are tested also allows us to adjust your company's security score: the higher the level, the more resilient the company is to phishing attacks, and the safer it is.
Practical application
During your phishing simulations, make a rough estimation of the level of difficulty.
If you use Arsen, it couldn't be easier: when configuring a scenario, you can declare a level of difficulty on the first page of phishing scenario settings.
This level of difficulty will be taken into account in weighting employees' security scores and therefore in calculating your company's resilience level.
The elements that influence the difficulty level of your scenarios often include:
- The realism of the emails and landing pages of the phishing campaign, ranging from spelling to design.
- The clues you leave regarding links, domain names, and information related to the sender.
- The level of realism of the internal campaign: tools, timing, and quality of the pretext compared to the company's environment.
Based on these parameters, determine the difficulty level of your campaign scenario.
If you do not use our phishing simulation solution, this information will still be useful for understanding your employees' performance in this campaign when presenting the results.
Conclusion
Phishing emails can be more or less detectable. From poorly spelled emails, lacking context with an improbable scenario, to highly personalized spear-phishing content, the range of possibilities is broad.
Ideally, everyone should have the knowledge and reflexes necessary to detect phishing emails, even if they are highly developed.
In the absence of this, this article already prevents you from underestimating cybercriminals by thinking that their arsenal is limited to misspelled emails.
