Social engineering means psychologically manipulating or “tricking” someone to get something valuable out of them. Cyber attackers use social engineering tactics to trick your employees into divulging company secrets, leaking confidential data, or handing over large sums of money.
98% of all cyberattacks apply social engineering in some way to initiate the attack. The global average cost of an attack in 2024 was USD 4.88 million - including financial theft and regulatory fines. The loss of brand reputation costs much more, and it is hard to put a number to it—some 60% of small businesses shut down within six months of an attack.
How can you protect your organization from social engineering and their adverse impacts? This article explores different attack strategies, real-world examples, and prevention methods.
What are social engineering attacks?
Social engineering is a broad term for any attack technique that exploits human behavior. Instead of targeting system vulnerabilities, attackers target human vulnerabilities. They try to create a sense of fear, urgency, or some other psychological pressure in humans, so they reveal confidential information. Sometimes, they could also attempt to get the employee to click on malicious links or download malicious files. This results in malware entering your system and causing further damage.
There are many different types of social engineering attacks. We give some examples below.
Phishing
It is the most common social engineering attack. Bad actors send communications that appear to originate from a trusted source.
Email phishing
Attackers send fraudulent emails pretending to be from legitimate organizations. The emails contain links to fake websites where victims are prompted to enter sensitive information.
For example - Bad actors impersonating the United States Department of Labor (DoL) sent emails to businesses in an attempt to steal employee Office365 credentials. Emails originated from fake domains that closely matched the original DoL domain - dol.gov —for example,
- dol-gov[.]us
- dol-gov[.]com
- bids-dolgov[.]us The emails contained professionally arranged content, valid letterhead, and a three-page PDF attachment form with a submit button. Users had to submit a bid application that required them to log in with their Office365 credentials. The form even gave an error message on 1st login attempt to ensure users entered the proper credentials.
Spear phishing
Attackers customize their messages with personal details to target specific individuals (typically high-profile employees).
For example, Belgian Bank Crelan was the victim of a fraud campaign aimed at their CFO, resulting in a loss of over 70 million euros. The attacker posed as a client demanding an urgent money transfer for a business transaction.
Vishing
Instead of emails, attackers use phone calls to trick victims into providing personal information. They pose as legitimate company representatives, tech support, or senior employees. With AI voice cloning technology becoming commonplace, the risk has increased significantly.
For example, a finance employee at a multinational firm in Hong Kong was tricked into paying $25 million to criminals who used AI voice cloning to pose as the company’s CFO in a video conference call.
Barrel phishing
Attackers send several innocent emails to gain employee trust before sending the scam email.
For example, hackers impersonated Dropbox support and started sending emails with general Dropbox information and cloud storage tips to employees at a U.S. firm. Eventually, they sent an email claiming that a file a colleague sent was too large and needed to be viewed in Dropbox (link to view). Once users clicked the link, they were directed to a counterfeit Dropbox login page, and their credentials were stolen.
80% of organizations report that phishing has worsened or remained the same. (Source).
Mobile phishing
Attackers use text messages to send fake warnings, alerts, or other notifications with links that redirect to fake copies of genuine websites. For example,
- Attackers pose as local tax authorities and send messages claiming unpaid taxes due.
- Attackers pose as parcel delivery services, claiming you have an undelivered parcel.
- Attackers pose as a big brand, claiming you have won a prize.
Pretexting
While pretexting, criminals fabricate a convincing scenario (or "pretext") to steal information. They pose as someone trustworthy, like a colleague, service provider, or authority figure. They then ask for personal details such as passwords, account numbers, or other confidential information under the guise of a legitimate need.
For example, MacEwan University, Canada, sent almost $12 million to a scammer posing as a contractor. The attacker asked staff to update payment information meant for a construction vendor partner through email. No one noticed until the legitimate vendor requested payments months later!
Quid pro quo
Attackers offer something in exchange for information or access. Victims think they're getting help, but they end up giving valuable information to the attacker.
The most common quid pro quo attack is tech support. The attacker pretends to be a legitimate tech support representative from a well-known company. They offer to fix a non-existent problem on your device, such as a fake computer virus. In return for their "assistance," they ask for remote access to your system. This seemingly harmless interaction often results in attackers gaining access to sensitive information or installing malware on your device.
For example, employees searching for “Microsoft support” or “Apple support” may inadvertently click on a sponsored ad from a scam company. They may even call the advertised scam number and assume they are talking to genuine Microsoft or Apple representatives. Unfortunately, they are sophisticated criminals who trick them into revealing confidential information.
Watering hole attack
Watering hole attacks target third-party websites that your employees or workers in your industry visit frequently. The attacker compromises the third-party website, so anyone visiting the website is redirected to a fake version for data harvesting.
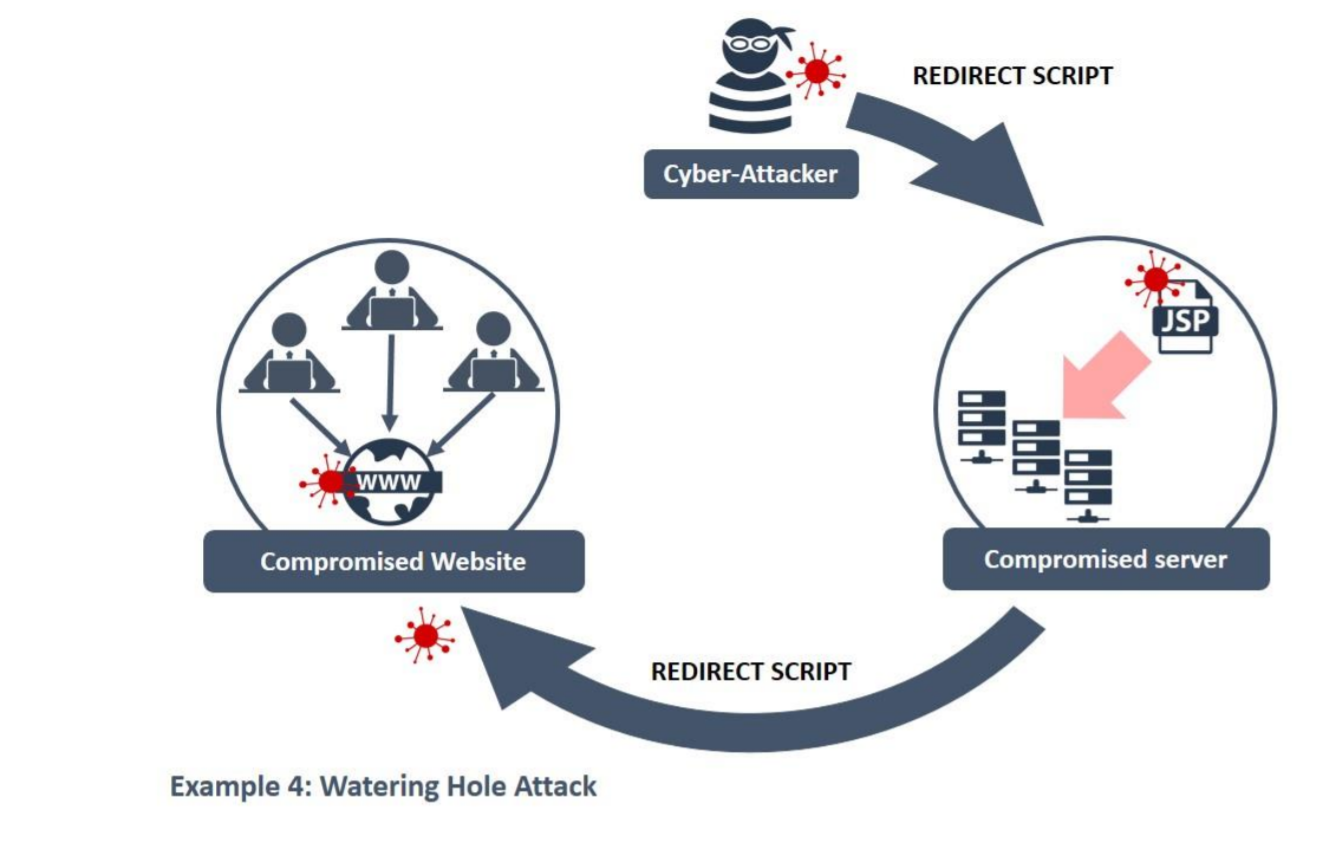 Watering hole attack (Source)
Watering hole attack (Source)
For example, APKMonk is a third-party app store used by enterprise developers to download Android Package files for Android app development. Attackers pretending to be APKMonk tricked site visitors into downloading spyware files. In just five months, the attackers gained access to data from infected devices of military members, government officials, medical professionals, and the general public. Security officials retrieved 6 thousand call recordings, 30 thousand images, and 600 videos containing private data. They found copies of detailed travel information, GPS coordinates of pictures, internal government communications, pictures of closed-door meetings, and other information relevant to espionage activities!
Prevention is better than cure
The attacks described above are only the tip of the iceberg. Like the many-headed Hydra of Greek mythology, social engineering attackers have nearly limitless ways of tricking innocent employees. Even as security authorities discover one attack type, two new ones emerge.
Cybersecurity solutions only provide baseline protection. Ultimately, it is up to your employees to remain vigilant in every digital and electronic interaction.
Arsen helps you fight back by providing cyber-aware training to your employees and simulation kits to your team. Our AI-powered simulations allow you to test and evaluate your company's ability to handle advanced social engineering attacks. Train everyone from CEO to junior employees so they recognize criminal activity, report it, and protect your assets.

