Prepare your organization for AI voice phishing attacks
Prepare your organization for AI voice phishing attacks
AI-driven voice phishing attacks are advancing rapidly, stay ahead with realistic voice phishing simulations that train employees to detect and protect your organization against vishing.
442%
growth in vishing attacks in 2024 — driven by voice cloning and AI impersonation tools
CrowdStrike Global Threat Report 2025
$40B
in AI-enabled fraud is expected in the United States by 2027
Center for Financial Services 2024 Report
72%
of organizations reported rising cyber risks fueled by AI-driven vishing attacks.
WEF - Global Cybersecurity Outlook 2025
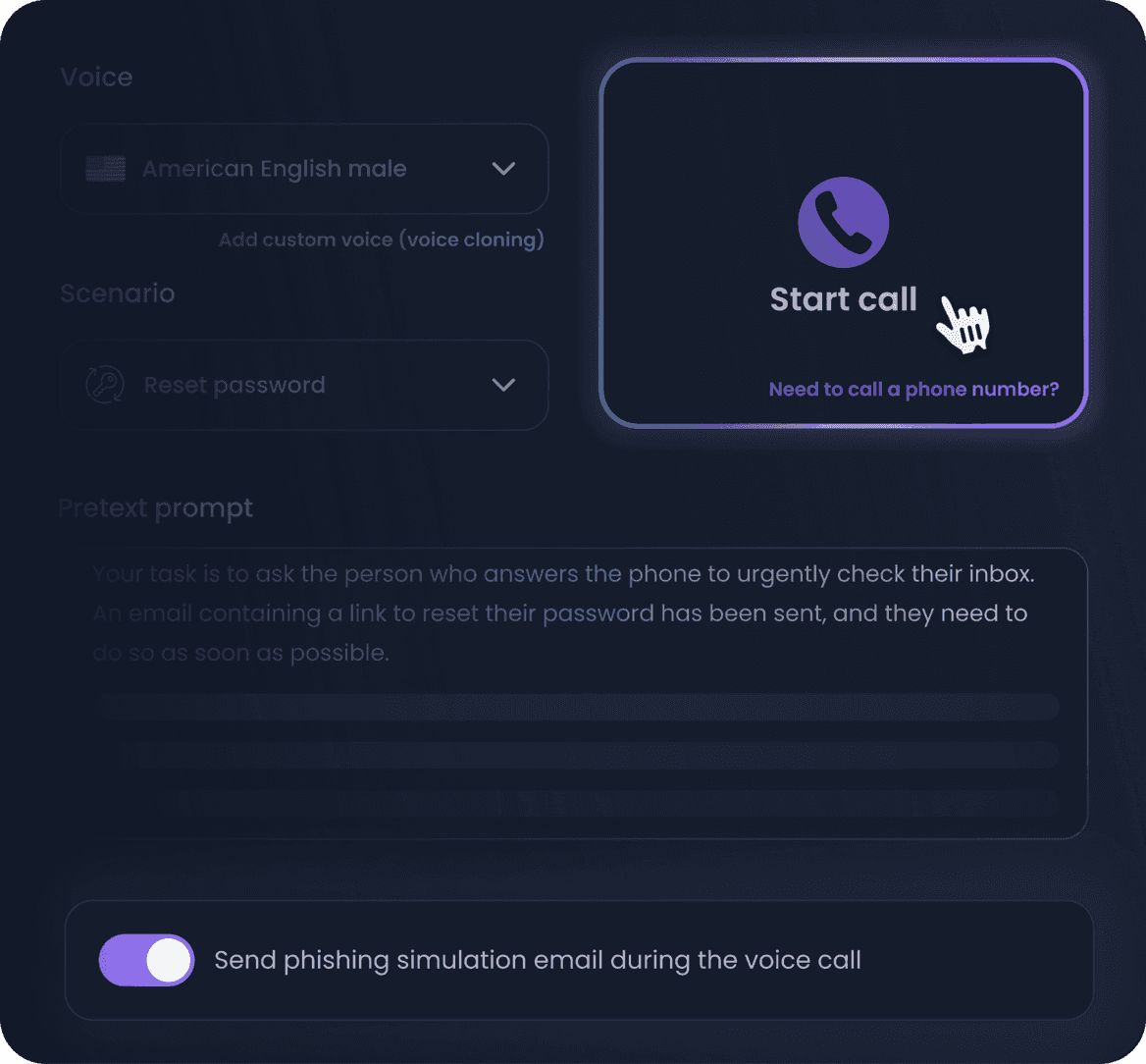
Simulate real voice phishing attacks with generative AI
Unlike basic decision tree tools, our vishing simulation tool uses generative AI to craft dynamic, unscripted voice phishing calls that adapt in real time — just like real attackers. Learn more on why vishing is the fastest growing attack vector in 2025
- Design your custom vishing scenarios tailored to your specific business context
- Prepare your team for blended attacks like barrel phishing with coordinated follow-ups
"We were shocked at how real the AI-generated calls sounded, especially with voice cloning. Arsen's vishing simulation showed how vulnerable even trained staff can be."
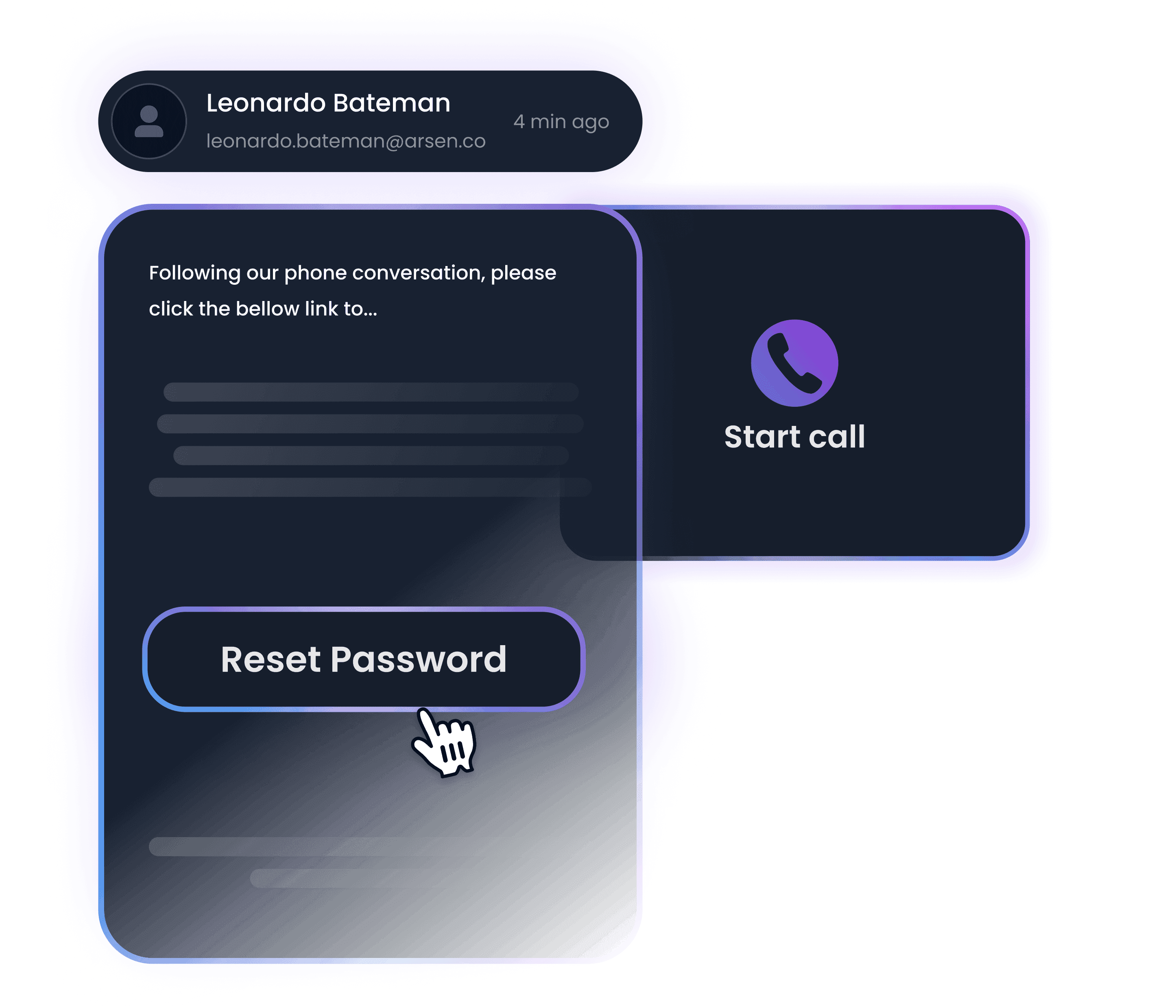
Built for phone-based threats
Deliver realistic, AI-generated voice phishing scenarios, from urgent impersonation calls to multi-stage fraud attempts, giving your team direct exposure to the tactics real attackers use.
- Simulate realistic calls like executive impersonation, tech support scams, and urgent fraud attempts
- Create multi-step vishing scenarios with follow-up emails
- Use our intelligent scheduling algorithms to pace call delivery and avoid triggering internal alerts
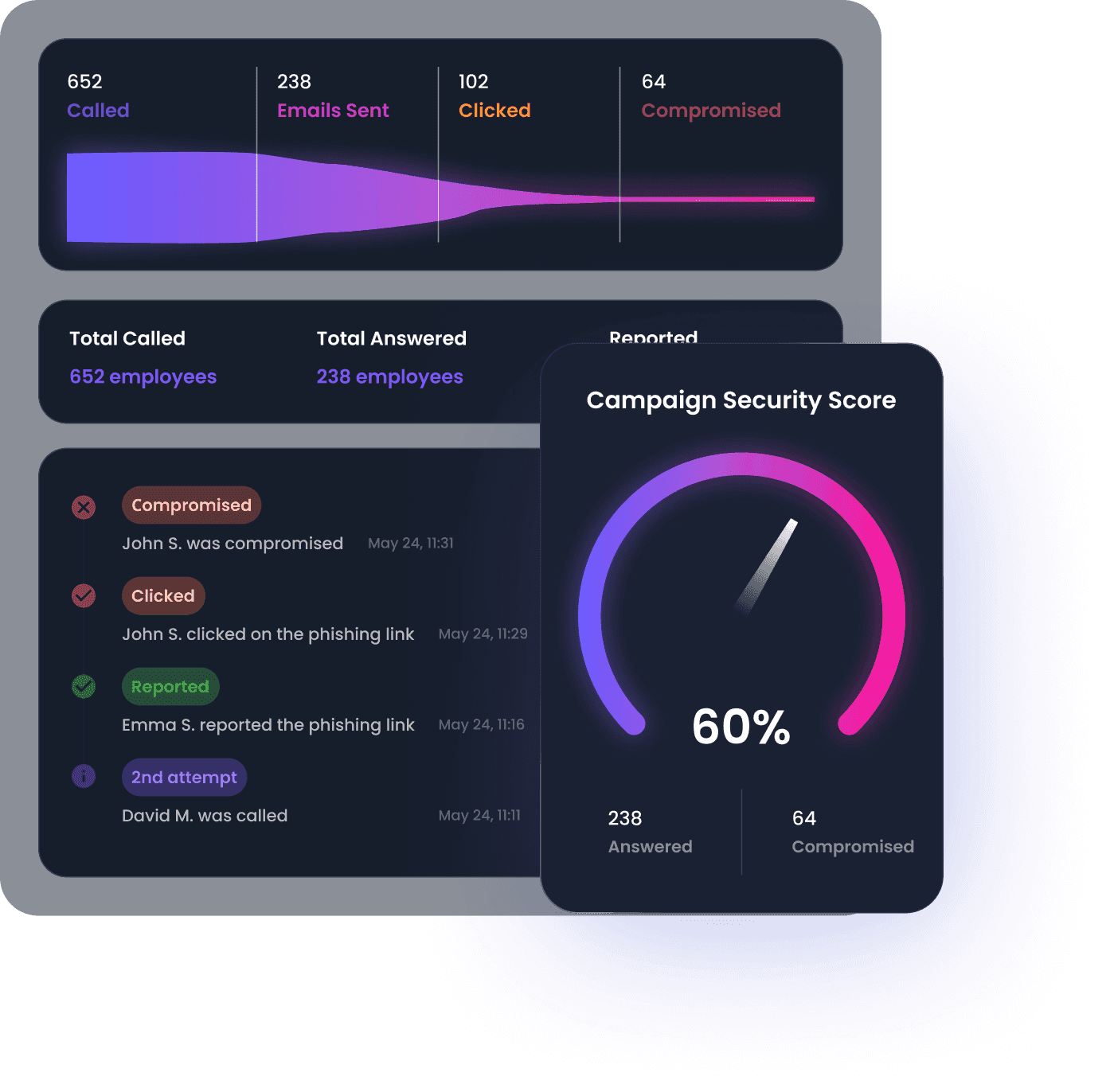
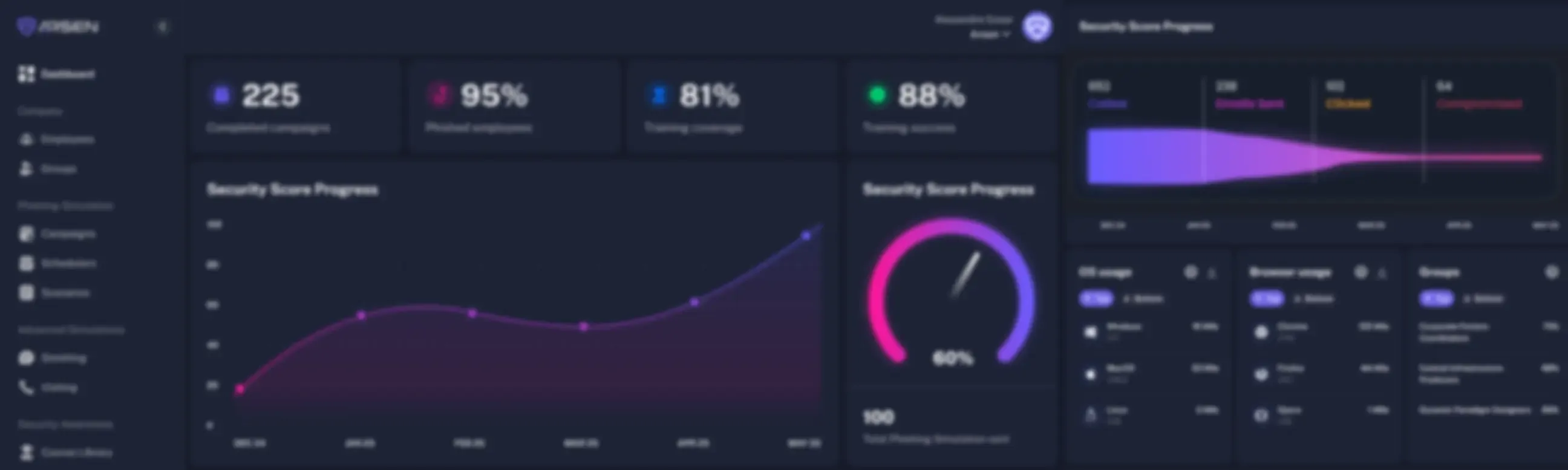
Real-time and actionnable insights to improve your security posture
Vishing reporting is available in real-time and provides insights on your employee's behavior. In-depth reporting is available from the organization down to the employee level.
- Monitor employee responses to simulated voice phishing calls in real time
- Access in-depth reports in PDF, CSV and through our API
- Track call outcomes, behavioral patterns, and risk levels by campaign and individual
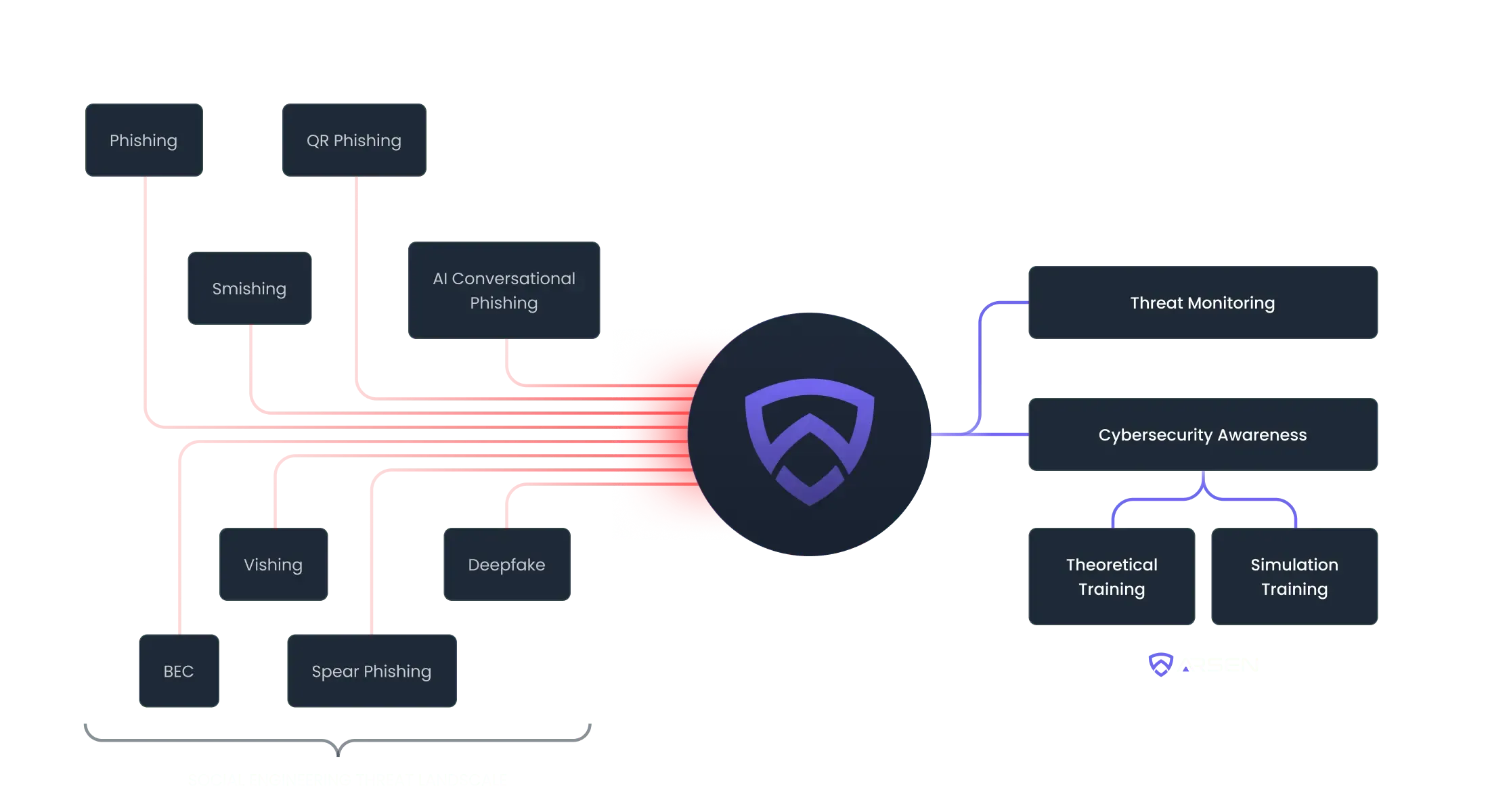
Protecting your business from every angle
Replicate real-world threats like advanced phishing, BEC, smishing, and vishing attacks to keep your employees aware and empowered to take action against threats.
Trusted by 500+ organizations worldwide
Empowering the best cybersecurity teams
Helps organizations meet regulatory requirements and industry standards
"Thanks to Arsen, I can quickly and regularly test our employees, confront them with realistic attack simulations, and track results in real-time."

Xavier Laurent
Chief Technology and Innovation Officer"Arsen is undoubtedly the best phishing simulation platform. Intuitive and reliable, it offers quick setup, detailed reports, and responsive customer support. Ideal for strengthening the cybersecurity of companies of all sizes."