An attack via USB drive, also known as USB Drop, is a danger that is still underestimated. USB drives are very effective in helping us store and transport small amounts of data. We use them regularly, and many people cannot imagine the lack of security in these tiny devices. Indeed, these storage spaces represent an extremely efficient vector for cyberattacks.
That's why we're going to introduce you to the different USB drive attacks, their consequences, and how to protect against them.
What are the different types of USB drive attacks?
There are three main types of USB drive attacks.
Each type of USB attack can only work if the victim connects the drive to their computer. So, part of the attack always involves persuading the victim to plug in the drive.
The human factor is therefore crucial in carrying out a USB drop attack.
#1 Using social engineering to execute a malicious file
Social engineering aims to manipulate the victim. The goal is to make them click on malicious files present on the drive.
For example, the drive may contain files named TopSecret.html or _CodesAcces.xls_x. These names arouse curiosity and increase the chances that the target will open the files to discover their contents.
These files aim to compromise the victim's security, either by executing malware or by redirecting the target to a web page.
Executing malware is often the simplest way to compromise the target. However, the victim's antivirus could trigger and thwart the attack.
Redirecting the victim to a phishing site is a less immediate but potentially more discreet way to hack them.
#2 HID spoofing: Making the drive appear as a USB keyboard
Human Input Device (HID) spoofing is a technique designed to deceive the victim’s computer. It will recognize the USB drive as a keyboard. The drive then sends a series of commands as if someone were using this keyboard to compromise the target computer.

The Rubber Ducky key, a famous HID tool
This is equivalent to plugging in a keyboard and entering a series of shortcuts and commands, executing a series of malicious operations.
#3 Exploiting a USB driver vulnerability: driver zero-day
Lastly, the driver zero-day is an attack that targets specific software. The USB drive has code that exploits vulnerabilities in the victim's computer to perform unauthorized operations.
The driver zero-day exploits an unpatched flaw in the USB driver: the program meant to allow the computer to use the USB drive properly. The malicious program exploits the driver to corrupt the victim when the drive is plugged in.
The drive exploits the USB driver's flaw upon insertion to inject malicious code, leading to the hacking of the host computer and potentially its network.
Do USB Drive Attacks Work?
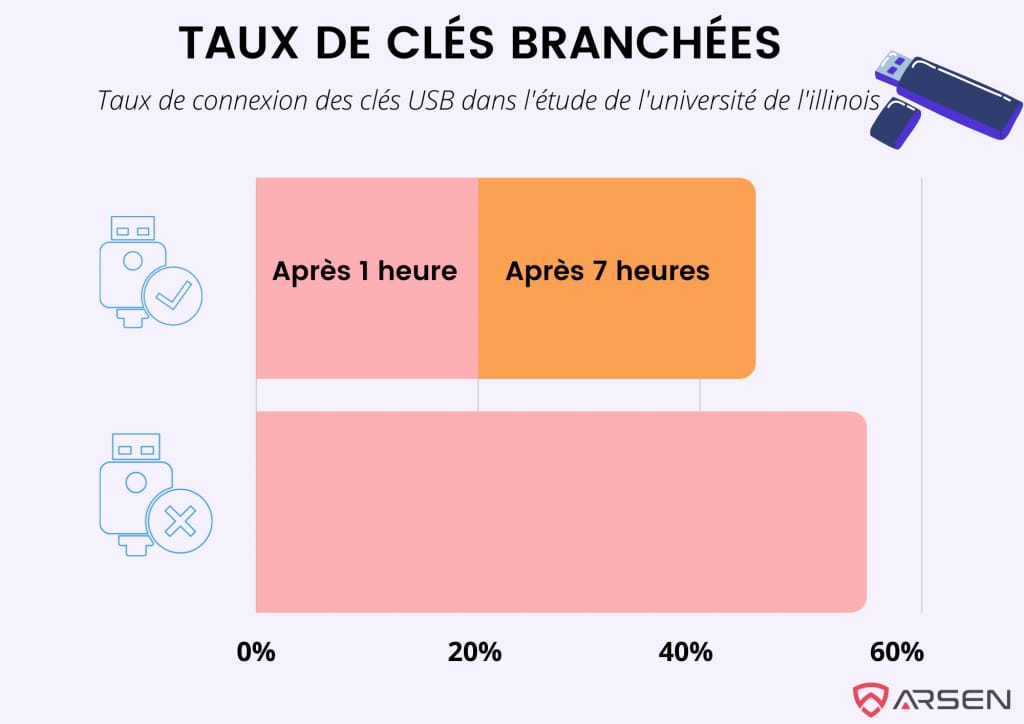
In 2016, researchers conducted a USB drop test: they dropped 300 USB drives across the University of Illinois at Urbana-Champaign campus. They then collected data on the number of USB drives that were plugged into a computer. Subsequently, they interviewed the students who explained their reasons for their actions.
- 20% of the USB drives were connected within an hour, and an additional 25% within the next six hours.
- Individuals who plugged in the USB drives opened and executed files on the drive in 48% of cases.
Why Do They Work?
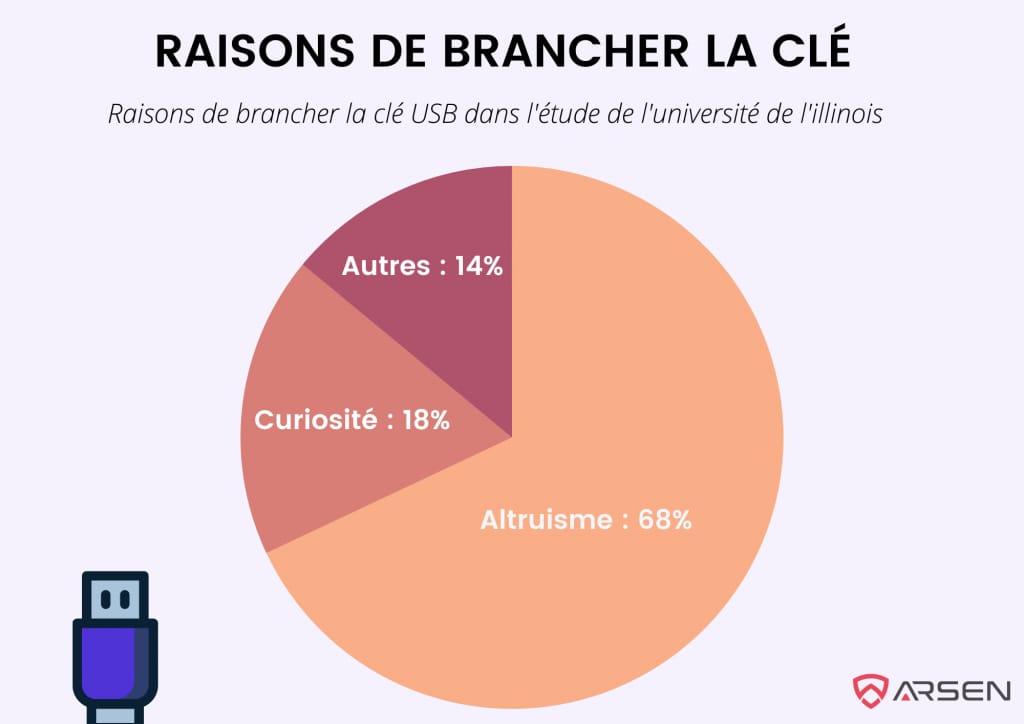
In the study, 68% of respondents said they plugged in the USB drive for altruistic reasons. The goal was to find out who owned the drive to return it to its owner.
Curiosity was the second most cited reason, at 18%.
Interestingly, the victim was more likely to open various files if physical keys — house keys — were attached. This indeed gave the impression of a genuine loss rather than a laid trap.
45% of the USB drives were connected despite the risks, indicating a real lack of understanding of the dangers and potential for USB drive attacks.
If you hadn't read this article and found a USB drive on your desk tomorrow morning with your first name written on it, what would you do?
Possible Consequences of a USB Drive Attack
A successful USB drop attack can lead to the total compromise of the victim's computer. Depending on the context and environment in which this computer operates (permissions, network security level, etc.), the consequences can be dire.
Extraction of Sensitive Information
The hacker can extract sensitive information from the computer by automatically targeting certain directories or file types. It is easy for them to access passwords, personal information, or banking details.
Remote Access
The hacker can exploit the infected computer as well as the network and devices connected to it: webcam, microphone, keyboard, etc.
Indeed, the USB attack allows the installation of a RAT (Remote Access Tool) and other malware that enables control of the targeted equipment.
Hardware Destruction
There are also USB drives known as “USB Killers” that can instantly destroy the hardware they are plugged into.

These drives temporarily store the energy provided by the USB port. They then send an electrical discharge of much higher voltage (between 100 and 200 V) through the circuit usually used for data transfer.
Sometimes the USB killer only destroys the USB port, but generally, the overload fries the computer's motherboard. Most often, this attack destroys the hardware into which the key is plugged.
Examples of USB Drive Attacks
In 2008, a USB Drop attack infected a U.S. military computer and then infiltrated the entire military base. The hostile program spread undetected and then transferred confidential data to foreign servers.
Another example: In 2009, Stuxnet, a computer worm, infected Iranian nuclear industrial sites via a USB drive. This was the first cyberattack on nuclear infrastructure.
The United States and Israel reportedly developed Stuxnet starting in 2005. They were concerned about nuclear bomb development in Iran and thus developed a virus to slow down the Iranian research program.
The sites were physically isolated from any computer network (air-gapped). Therefore, other attack vectors had to be used to infect the targeted systems.
The attackers decided to first target the suppliers and contractors of the plants — this is a supply chain attack.
They then waited for an individual to insert a USB drive containing the virus inside the site.
Stuxnet was thus able to target the PLCs — Programmable Logic Controllers — controlling the centrifuges needed for the separation of nuclear materials, causing them to accelerate until they were destroyed.
More than a thousand centrifuges were destroyed, thereby slowing down the development of nuclear weapons in Iran.
8 Tips for Protection
Fortunately, there are several ways to protect against USB attacks, here are 8:
Prevention is Key: It's essential to conduct prevention awareness within your company. Your colleagues must be aware of the dangers posed by unidentified USB drives and the possible consequences of using them.
Use a Secure Transfer Station: Consider using a dedicated secure device, like those offered by Hogo, as a buffer between your computer and an unknown USB drive. These 'white stations' can analyze and verify data before it reaches your network.
Invest in Antivirus Software: Use robust antivirus software that can scan USB drives. If it's not the default setting, activate the option for systematic scanning of new USB devices to detect known malware.
Immediate Response to Threats: If you suspect a USB drive is malicious after connecting it, immediately disconnect the affected computer from your network. Contact your IT service without restarting your computer to enable them to analyze the threat and the USB's content.
Disable Autorun Features: Although not often used nowadays, autorun features can be a significant risk when inserting removable media. If these features are active, they should be disabled. Without autorun, removable devices like USB drives cannot execute any programs automatically, reducing the risk of some types of attacks (though this does not protect against HID attacks).
Beware of USB Chargers: Some USB cables or chargers can be malicious, employing tactics known as juice jacking. You can use "power only" cables that don't have data transfer capabilities and will only charge your devices. These won't be able to transfer data or infect your devices.
Disable USB Ports When Not Required: Consider disabling USB ports on server bays or specific-use computers that do not require USB connectivity. This physical safeguard can prevent unauthorized devices from being connected.
Comprehensive Security Training: Train your staff on various attacks that target them (USB, phishing, smishing, vishing, etc.) to strengthen your company's digital security.
Remember, human vigilance is the first line of defense in preventing a USB attack. An attack requires human action: the USB drive won't connect itself! By training your employees, you can turn them into a genuine human firewall, spotting and reporting attacks, thereby enabling your security service to address threats proactively.
