Human Cyber Risk Scoring
Understand, measure and quantify human risk facing cyber threats.
Understand, measure and quantify human risk facing cyber threats.
By measuring behavior against current threats, you can get a precise understanding of the risk tied to human behavior.
Arsen reproduces current threats froM CTI feeds and tests its impact on human elements.
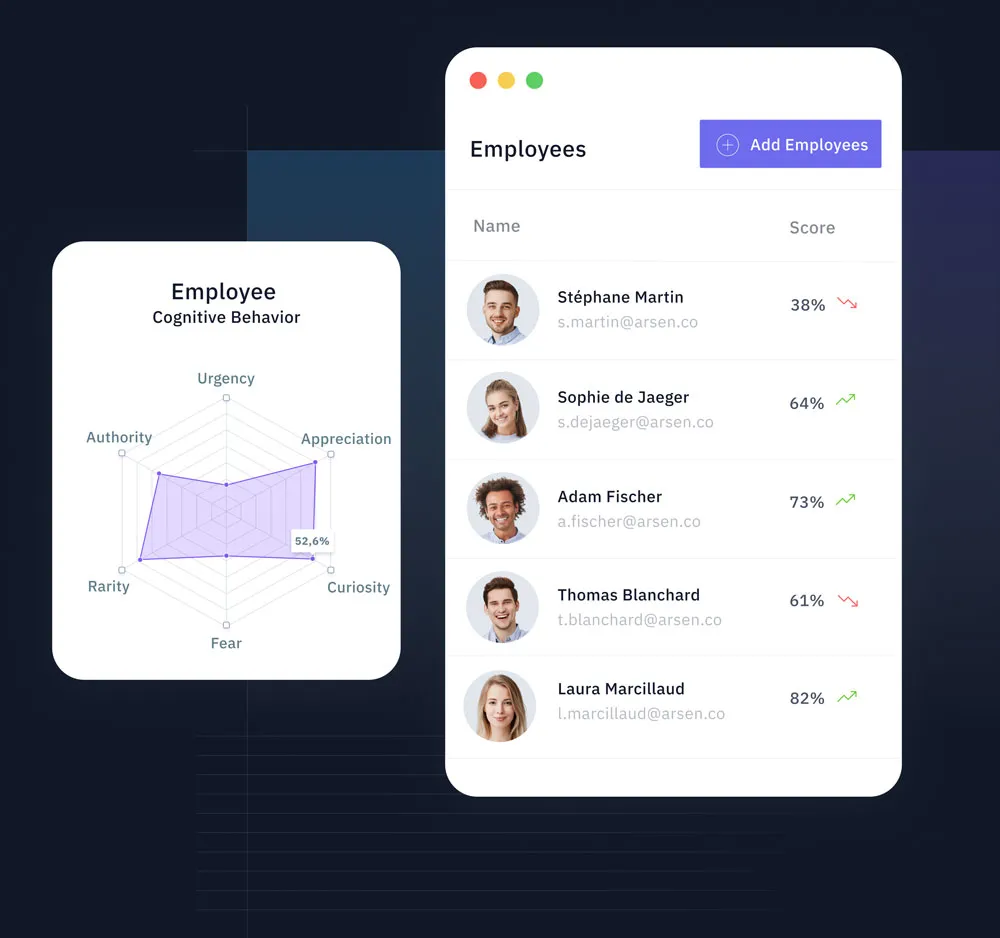
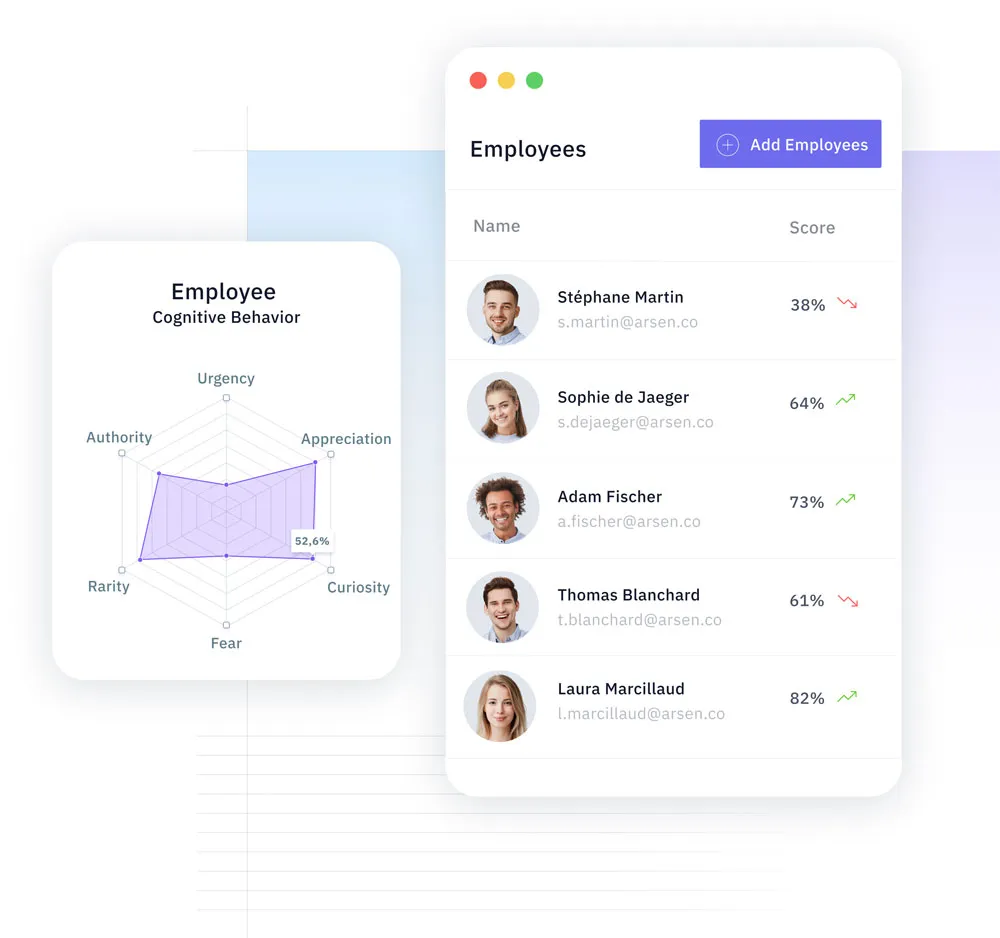
Based on the criticality of groups or employee profiles, Arsen determines the human cyber risk profile.
Behavioral Analysis
Elevate your cybersecurity without the upfront costs. Experience cutting-edge phishing simulations with a flexible payment model, ensuring you only pay for what you use.
Using Threat Intelligence feeds, Arsen analyses threats psychological levers and difficulty level to reproduce them.
Arsen analyzes the susceptibility of your employees to the influence levers used by hackers and identifies the most at-risk groups.
By running recurring threat simulations, Arsen adds a layer of Human Observability.
Arsen combines measures of difficulty, reaction time and interaction to maintain an accurate view of your risk.
Arsen allows you to see the devices and softwares used by your employees and detect unsecured IT.
How to evaluate cybersecurity human risk?
Simulate real, active threats and not facing dummy, unrealistic, cookie-cutter attacks. Simulation execution is also key here: the simulation process should follow the modus operandi of active threat actors to reflect behavior in realistic conditions.
Then, you need a precise understanding of how they behave in front of the threat. Not only if they detect and report it, but what kind of endpoint they use, how much time it takes them to detect the threat, at which stage, etc.
Depending on employees, their access level, their position of authority within your company, the risk level isn't the same. On one hand you need to evaluate the likelihood they get caught in a threat, one the other you need to take into account the risk if they do.
Experience the difference with our risk analysis, threat modelization, and sophisticated phishing simulations.