From the early days of phishing to the present, almost 30 years have passed, with a constant evolution of the techniques used by cybercriminals.
These fraudsters have been active for much longer than the emergence of the first phishing emails: from the telegraph in the 19th century through the telephone and the Minitel to the Internet today, new practices have always been targeted.
Phishing is primarily an attack vector. Just like an employee deciding to sabotage a system (internal threat), phishing is an external threat where email is used as an attack vector. A large part of today's cyberattacks (botnet, ransomware, malware, etc.) use social engineering and phishing to achieve their ends.
The Origins of Phishing
It is common to trace the emergence of phishing back to the 1990s, specifically in 1995, when a 17-year-old developed AOHell, a program that could steal passwords from AOL users.
It was also during this time that the portmanteau "phishing" was born, merging "phreaker" (telephone hacker) with "fishing." In French, this term became "hameçonnage" in 2004, although the Anglicism "phishing" is still widely used today.
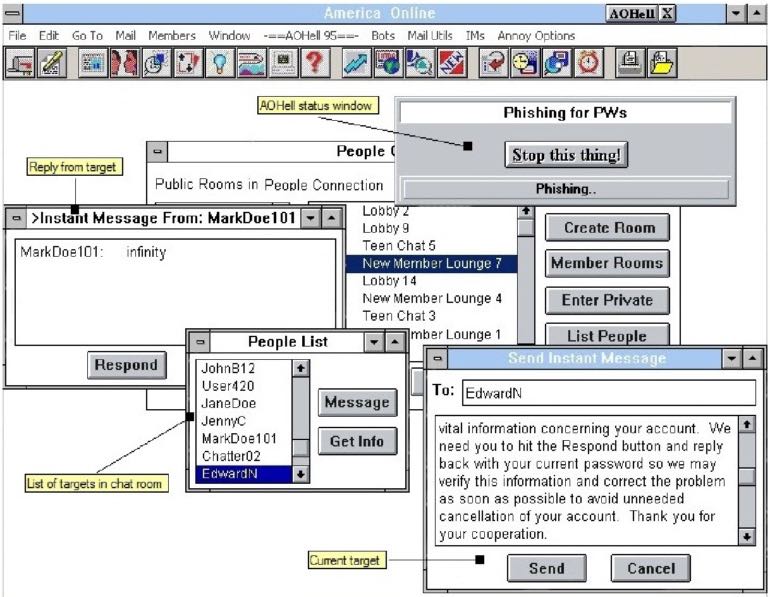
AOHell
In 1994, like many others, AOL did not warn its users about the dangers of phishing.
AOHell's attack method was simple and effective:
- Obtain an anonymous AOL account by creating it with a fake bank account or use an account stolen in a previous attack.
- Create a pseudonym on the new account.
- Write the "phish" message explaining to users the need to verify their passwords or billing information. For example: "Hello, I am a chat room moderator. Due to a problem with our records, we need you to respond to this message with your AOL password to avoid being disconnected."
- Locate a chat room for new AOL internet users and open the list of participants online.
- Send a private message containing the phish to each user.
To understand this, one must consider the context of that time: the AOL application allowed connection to chat rooms, some of which were dedicated to newcomers on AOL.
By newcomers, we mean internet novices. It's highly likely these individuals were experiencing the internet for the first time in their lives. Their lack of experience with the internet's dangers made them very vulnerable targets for attackers.
It wasn't until 1995 that AOL took the necessary measures to protect its users, and 1997 before the first public messages on AOL media were broadcast using the now-familiar term "phishing."
Phishing in the 2000s
Fast forward to the early 2000s, AOL is losing the race, Yahoo and MSN are gaining momentum, and Google is beginning to take market share from Lycos and Altavista. Phishing is now a term known to some regular internet users, while just over 10% of the French population has home internet access.
In these years, phishing was not yet the greatest concern in terms of cyberattacks. People were more afraid of the Y2K bug, the ILOVEYOU virus, or the frequent Denial of Service (DoS) attacks that affected internet giants like Yahoo, CNN, eBay, and Amazon.
Yet, the dawn of this new millennium saw the popularization of tools—open-source—for mass mailing, meaning the mass sending of phishing emails.
Email quickly became commonplace, rapidly replacing AOL chat rooms and newsgroups. Email is everywhere, its use increasing by 50% each year between 2000 and 2005. This new means of communication is confidential and anonymous (you don't know who's behind the sender). In essence, email has become the perfect medium for the development of mass phishing.
The Case of E-gold
One of the first companies to pay a heavy price for a phishing attack was E-gold. This startup, founded in the dot-com bubble of the 2000s, allowed people to buy a global alternative currency convertible into gold and use this currency on third-party sites.

In 2001, E-gold was handling $2 billion in transactions annually and saw its user base growing rapidly. 📈
The attack targeted E-gold users, and spoofing was the new trend. This technique fooled a user into believing that e-goId.com was the same site as e-gold.com... where the capital "I" had replaced the lowercase "l" in "gold." This domain name had nothing to do with the E-gold company, and for a human, it was very hard to detect the deceit.

In the same way as for the fake website, hackers were able to send emails from support@e-goid.com, making the attack even more believable.
E-gold lost millions in this debacle and couldn't stem the tide of fake e-gold accounts, allowing hackers to hide their loot in virtual currency. These incidents eventually led to E-gold's downfall a few years later.
Certainly, here's the English translation of the text you provided:
The Evolution of Phishing 2003-2010
As internet users became increasingly aware of the dangers associated with phishing and more informed about the signs to watch for to protect themselves, cybercriminals, on the other hand, developed increasingly sophisticated techniques. These techniques notably include URL obfuscation to create emails and websites that appear legitimate and exploiting browser vulnerabilities to allow the downloading and execution of malicious code from a hostile site.
Let's take another leap back to 2003, in the midst of the "browser war," when Google Chrome and Firefox did not yet exist, and Internet Explorer had just stolen almost the entire market share from its competitor, Netscape.
Microsoft's browser was then the worst enemy of web developers but also... of IT security managers who knew full well that this browser was very vulnerable, much to the delight of cybercriminals.
Among the most used techniques of that period, some are still relevant today, although increasingly difficult to implement.
URL Obfuscation
URL obfuscation misleads victims by making them believe that the link or website displayed in their browser is that of a trusted site. Although this attack is simple to implement, it is terribly effective.
The underlying techniques that involve URL obfuscation include HTML redirects, the use of images in emails, the use of character sets other than UTF8, or even the registration of very similar domain names as seen above with the e-gold case.
Internet Explorer Vulnerabilities
Internet Explorer without its security flaws is not Internet Explorer. More than 1000 flaws have been identified over the past 20 years, more than half of which are considered critical.

Number of known vulnerabilities in Internet Explorer from 2004 to 2020
These flaws have allowed cybercriminals to use phishing techniques such as URL obfuscation via pop-ups, or the exploitation of flaws allowing an attacker to use the ActiveX control DHTMLEdit by loading it from a malicious website to modify the content of another legitimate browser window and replace the content of the legitimate window with malicious content.
Today, this type of attack has become much more difficult, if not impossible, thanks to modern web browsers that are much more secure than before.
Abuse of Internationalized Domain Names
This type of attack, also known as a homographic attack, was trendy because it was almost undetectable to the victim: it involves using the similarity of characters in different written languages (Latin, Cyrillic, etc.).
This allows for the registration of domain names like "аmazon.com" instead of "amazon.com." The first "а" is actually a Cyrillic "a," the difference being invisible to a human.
ℹ️ Today, and since 2003, the use of "punycode" syntax allows the use of internationalized domain names in a way that's transparent to the user. Characters not from the Latin alphabet are automatically replaced by their equivalent in punycode, making this homographic attack more easily identifiable, provided one has the right reflex to carefully check the URL displayed by the browser.

amazon.com with a Cyrillic “a” in Punycode
The Democratization of Phishing Kits
Phishing kits are sets containing all the paraphernalia needed to trap a victim: fake web pages, pretext email templates, payment gateways, etc.
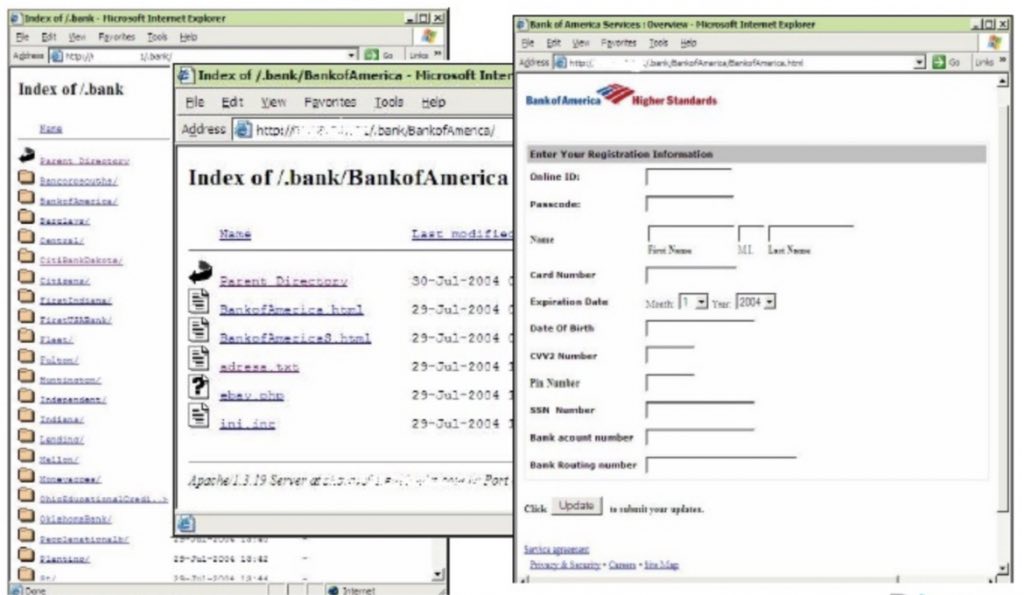
Phishing kit containing a fake registration form for Bank of America
These kits became democratized in the first part of the 2000s as cybercriminal groups organized themselves to become more efficient.
Cybercrime began to bring in big money and was considered by the FBI in 2004 as a full-fledged branch of organized crime. It was also around this same time that the general public discovered the existence of cyber-gangs such as the Russian RBN, Evil Corp, or Fancy Bear.
The Advent of Social Networks
Finally, the 2000s marked the arrival of major social media players: MySpace, Facebook, YouTube, Twitter, etc.
This revolution in usage gave hackers a significant boost: gathering victims' personal information becomes a piece of cake, personal information is now public and accessible to all. Users are barely aware of the danger, and they don't hesitate to share their vacation photos, reveal who they vote for, their health problems, or even their love troubles.
This information is crucial for cybercriminals who will take advantage of these new online media to improve their attack scenarios and even better manipulate their victims into divulging their confidential data.
Social networks have also facilitated the development of "spear phishing" attacks, or harponnage in French. This type of phishing attack is sent to a selected target (an individual or organization) with a highly personalized attack scenario and typically a larger reward.
👉 The rest of the article, where we will discuss the evolution of phishing from 2010 to the present, as well as the future of phishing, is available here 👨💻🎣

