
Modern Phishing Detection: Why It’s So Hard and How to Get Better at It
Modern phishing detection is notoriously difficult. As technology evolves, so do attack patterns. What was once a simple scam exploiting an emotional lapse has become a sophisticated, multi-layered...

MFA Fatigue: The Growing Threat Undermining Multi-Factor Authentication
Multi-factor authentication (MFA) was supposed to be the silver bullet. By requiring a second step—typically a push notification or a one-time code—organizations could drastically reduce the risk of...

Quishing: The Rise and Dangers of QR Code Phishing
Quishing — short for QR code phishing — is a rapidly growing threat vector that blends physical simplicity with digital deception. While many organizations have matured their defenses against...

QR Code Phishing: The Complete Protection Guide
QR code phishing, sometimes called “quishing,” is a rising threat that cleverly blends the digital and physical worlds. Attackers embed malicious URLs inside QR codes, hoping victims will scan them...
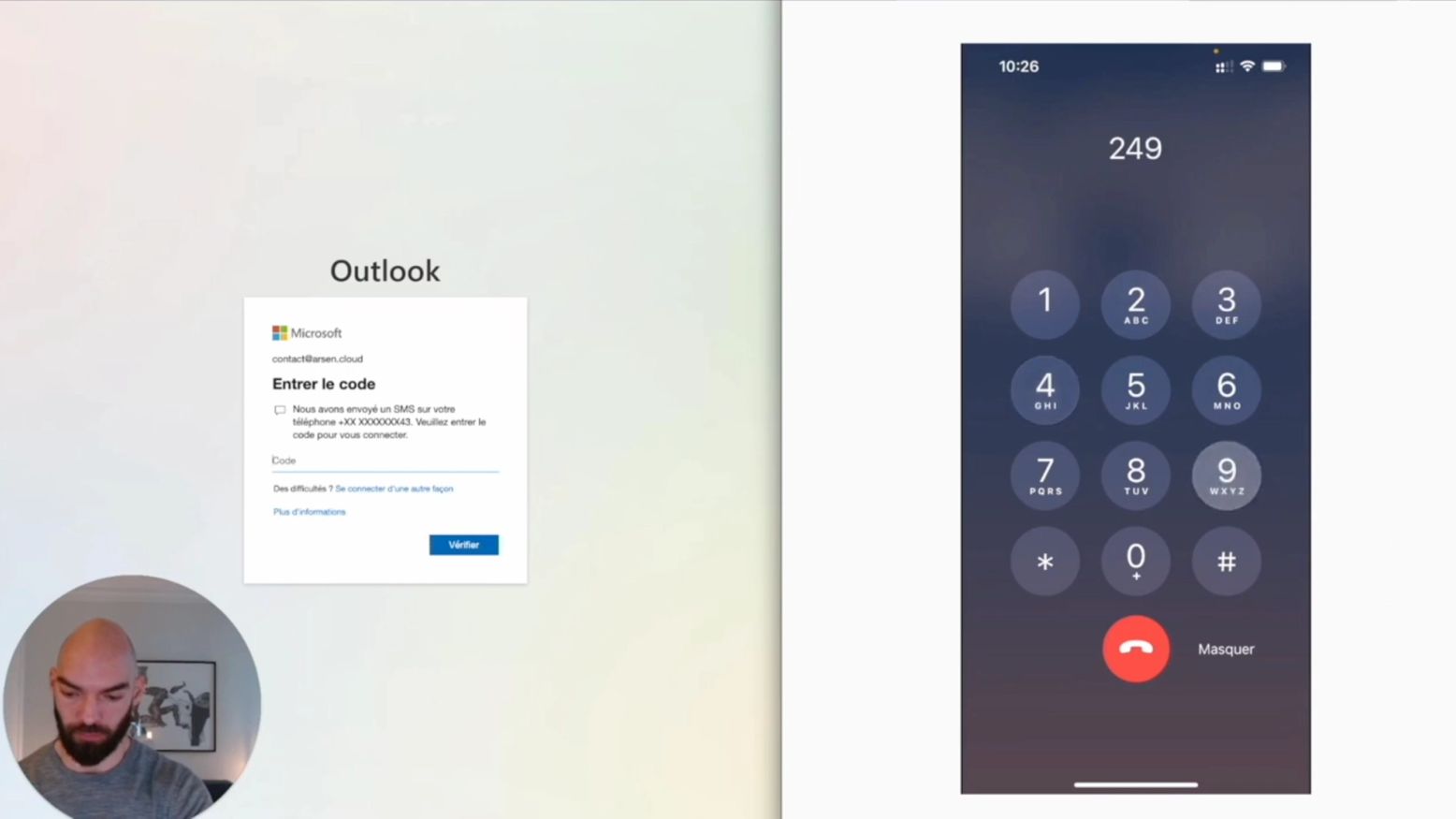
Bypassing Multi Factor Authentication (MFA) with a callbot
Call bots, a kind of vishing automation can be used to trick victims and defeat MFA. Here's how.

Domain Doppelgängers: Protecting Against Domain Spoofing
Cybersecurity threats continue to evolve, and one of the rising concerns for businesses is the domain doppelganger. These deceptive domains are crafted to mimic legitimate websites, luring...

Typosquatting: How Misspellings Can Lead to Fraud
Typosquatting, also known as URL hijacking, is a form of cyberattack that exploits common typing mistakes made by users when entering website addresses. A single misspelling can redirect users to...

Which Type of Phishing Simulation Should You Choose?
Phishing comes in different shapes and forms. This means you have a lot of choices when it comes to creating a phishing simulation, and most companies get confused as to what type of simulation...

How to launch a phishing simulation to better protect your company?
In this post, we'll explore the key steps to launch a phishing simulation that will help you protect your company from phishing attacks.

Quishing: When Phishing Meets QR Codes
Quishing is a new phishing tactic where attackers use malicious QR codes to deceive users into visiting fraudulent websites or downloading harmful software. Learn how quishing works, real-world...

What Is a Common Indicator of a Phishing Attempt?
Identifying common indicators of a phishing attempt is crucial for staying secure online. Look out for suspicious sender addresses, generic greetings, urgent language, unusual links, and requests for...

Phishing Attack Types Every CISO Should Know
Phishing attacks come in various forms, from deceptive emails to fraudulent text messages. Understanding the types of phishing—including email phishing, spear phishing, smishing, vishing, and clone...

Understanding Spear Phishing: Focused Cyber Attacks
Spear phishing is a targeted cyberattack that uses tailored information to trick individuals or companies into revealing sensitive data. Learn what spear phishing is and discover key prevention tips,...

What Is Spear Phishing? Definition & Defense Tips for CISOs
Spear phishing is a targeted form of phishing that uses personalized tactics to deceive specific individuals or organizations. Unlike regular phishing, spear phishing exploits trust by mimicking...

Spam vs Phishing — Key Differences & How to Stay Protected
Spam and phishing are common types of unwanted emails, but they serve different purposes and pose different risks. While spam typically promotes products or services, phishing aims to steal sensitive...

Smishing vs Phishing: What Cybersecurity Pros Must Know
Smishing and phishing are cyber threats that use deception to steal personal information. While phishing typically targets victims through email, smishing uses text messages to trick individuals into...
Examples of Phishing Emails and Prevention Tips
Phishing emails are crafted to deceive and steal sensitive information. Understanding various phishing email examples, such as fake security alerts, unexpected invoices, and prize notifications, is...

How to Identify a Phishing Email & Protect Your Organisation
Phishing emails use deceptive tactics to trick you into revealing sensitive information. Learning to identify phishing email techniques, such as manipulated sender addresses, urgency tactics, and...

Phishing Detection: Tools and Techniques
Phishing detection is essential to prevent cyberattacks that trick individuals into revealing sensitive information. Combining advanced tools like email filters, web filtering, and anti-phishing...

How to Spot a Phishing Email: Key Indicators
Phishing emails are a favorite tool of cybercriminals, designed to steal sensitive information. Knowing how to spot a phishing email is key to staying protected. Look out for unusual email addresses,...

Facebook Phishing: Protecting Your Profile
Facebook phishing is a common scam where attackers attempt to steal your login credentials and personal information. By recognizing tactics like fake login pages, malicious links, and impersonation,...

Phishing Email Examples: Spotting the Signs
Phishing emails often disguise themselves as legitimate communications to trick you into revealing sensitive information. Recognizing an example of phishing email is crucial for protecting your data....

TOP 5 Common Indicators of a Phishing Attempt
Phishing attempts are designed to trick you into revealing sensitive information. Recognizing the common indicators of a phishing attempt is essential for online security. From suspicious sender...
Clone Phishing: Recognize and Avoid
Clone phishing is a deceptive cyberattack where legitimate emails are replicated with malicious intent. Attackers use nearly identical copies of trusted communications but replace links or...

Check Phishing Link: How to Verify Safe URLs
Phishing attacks often involve malicious links disguised as legitimate URLs. Knowing how to check phishing links is essential for your online security. Be cautious with suspicious URLs, hover over...

What is Catfishing? | Identifying Online Deception
Catfishing is a form of online deception where individuals create fake identities to manipulate others. Learning how to identify catfishing is essential to protect yourself from these scams. This...

Catfishing meaning: Definition & Examples
Catfishing is a form of online deception where someone creates a fake identity to lure others into fraudulent relationships. This practice can involve emotional manipulation, financial scams, or...

What is Spoofing? | Cybersecurity Risks
Spoofing is a deceptive cyberattack where criminals disguise themselves as trusted sources to steal sensitive information or spread malware. One of the most prevalent forms is email spoofing, where...

Spoofing Definition: What It Is & How to Prevent Email Attacks
Email spoofing is a deceptive cyberattack where hackers forge an email's sender address to appear as though it's from a trusted source. This tactic is often used in phishing schemes, business email...

How to Prevent Spoofing: Strategies & Best Practices
Email spoofing is a dangerous cyber threat that can compromise your organization’s security and reputation. Attackers disguise their emails to appear as though they come from a trusted source, often...

3 advantages Arsen has over Gophish
At Arsen, we love Gophish. It’s by far the most comprehensive open-source solution for deploying phishing, whether for evaluation, training, or research purposes. That being said, GoPhish has...

Alternatives to GoPhish for Comprehensive Phishing Simulations
Phishing simulation tools have become the front line of defense in cybersecurity training. By mimicking real-life phishing attempts, these tools assess human vulnerability in digital landscapes. One...

The Multi-Scenario Campaigns
A new feature has arrived on Arsen: multi-scenario campaigns. It allows you to use multiple phishing scenarios within a single campaign. The benefit? Stay realistic by not targeting all your...

USB Drop: Discover the USB drive powered attack
An attack via USB drive, also known as USB Drop, is a danger that is still underestimated. USB drives are very effective in helping us store and transport small amounts of data. We use them...

"OVH: Domain suspension", analysis of the phishing campaign
At Arsen, we help businesses protect themselves against phishing. Part of this work involves simulating attacks on employees. We are therefore particularly attentive to real attacks that can be...
How to customize a scenario with Arsen?
In this article, we will see how to customize a phishing test with Arsen. More specifically, what elements can be included in the email to have a realistic, personalized, and more or less difficult...

How to effectively raise awareness against phishing?
In this video, we explain [how to effectively raise awareness against phishing](https://arsen.co/blog/sensibiliser-efficacement-phishing). The objective of this awareness is to improve the behavior...

What is phishing? Cyberattack's most popular initial access vector
Whether it's clicking on a malicious link or sending confidential data to a fake third party, if the threat is always external, 90% of effective cyber attacks involve an error resulting from human...

What are the results to observe during a phishing simulation?
During a phishing simulation, you will retrieve behavioral data and be able to determine your level of resilience. But what are the results to observe following a false phishing campaign and how to...

Classification of the difficulty level of phishing
Not all phishing emails are equal. When I ask someone what they think of a "phishing email," the descriptions are very varied. Among these descriptions, the level of difficulty, that is to say, how...
Click campaigns: lightweight phishing simulations to train people
Click campaigns are now available on Arsen! When you schedule a phishing campaign, it is possible to do Credential Harvesting or a click campaign. If an employee clicks on the link during a...
How to Conduct a Successful Phishing Simulation
Why conduct a fake phishing exercise? Phishing is the entry point for 91% of attacks*. The objective of phishing simulations is to prevent the hacking of your company in order to avoid financial...

Defeating Multi-factor Authentication through a Simple Phishing Email
In this article, I will show you in a video how, from a simple phishing email, we can bypass multi-factor authentication, also known as MFA or 2FA."

How often to conduct phishing simulations?
When a company adopts a new phishing simulation solution, the question often arises: "How often should I conduct phishing simulations?" The frequency of phishing simulations is a crucial parameter...

Managing the risks tied to phishing
The risks associated with phishing are often underestimated. Many still believe that the consequences are limited to having to change a few passwords, scan their network, or even have a comprehensive...

BEC Definition: Understanding Business Email Compromise
The compromise of email addresses, or Business Email Compromise (BEC), is a popular attack aimed at compromising a company's mailbox for malicious purposes. The simplest monetization is generally to...
Instagram Phishing: Risks and Protection Measures
Instagram is a highly popular social network, making phishing on the platform equally prevalent. According to the "Digital Report 2021" by Hootsuite and We Are Social, Instagram ranks fifth among the...

The slow but steady evolution of phishing attacks
Discover the evolution of phishing attacks over time, from the first phishing attack to the most advanced attacks occurring today.
What to do after a phishing simulation?
It is not always easy to know the steps that follow a [phishing test](https://arsen.co/test-phishing). Many of our clients contact us initially for a phishing test and ask us what they should do once...
How to Run a Phishing Test & Measure Security Awareness
In this article, we will analyze the process of a phishing test, from its setup to reporting. We will discuss framing, technical deployment, execution, and post-mortem of the exercise.

Smishing Definition & 10 Tips to Stop SMS Phishing
Did you know that SMS has an average open rate of over 95%? The definition of smishing is a digital attack through SMS that can have serious consequences. SMS marketing has become a strategy that...

Managing Campaigns as a Team.
Managing numerous phishing campaigns takes time. That's why many of our clients share the various tasks related to phishing test management or scenario design. Our awareness platform allows you to...

"Browser in the Browser": A New Variant of Phishing
A new variant of phishing has been observed lately, called Browser in the Browser (BitB). It is simply an attack aiming to deceive usual human detection techniques by generating a fake window inside...

How to Assess Phishing Risk & Strengthen Your Defenses
Phishing is the entry point for 90% of cyberattacks today. This threat poses various risks to a company, including organizational, reputational, financial, and legal risks. It is therefore...

The phishing of Instagram accounts
Instagram is a very popular social network, so it is logical that phishing on Instagram is just as popular. According to a study, "Digital Report 2021" published by Hootsuite and We Are Social,...

Why carry out phishing simulations with groups of employees?
The aim of your phishing campaigns is to get as close as possible to real attacks threatening your company in order to improve your resilience against them. Some hackers are increasingly focusing on...



