
The ShinyHunters group is currently orchestrating vishing attacks and exploiting single sign-on (SSO) to bypass multi-factor authentication (MFA). These sophisticated campaigns have led to breaches of cloud platforms like Okta, Microsoft 365, and Google Workspace, resulting in significant identity theft and cloud data exfiltration. Mandiant (Google Threat Intelligence) has provided detailed insights into the group's evolving tactics.
Key Takeaways
- Attackers are bypassing sophisticated technical controls like SSO and MFA by exploiting human psychology through real-time voice pressure, using vishing and social engineering.
- Modern campaigns rarely stay in one channel; they often combine phishing emails with follow-up vishing calls to build credibility and force rapid action. This is the case here with this hybrid attack.
- Using IT help desk impersonation, attackers persuade employees to reset credentials or install remote access tools, providing a direct gateway to corporate SaaS environments like Okta or others.
- While most organizations have established phishing simulations, very few effectively test employees against voice-based social engineering, leaving a critical blind spot for CISOs.
ShinyHunters and SaaS Data Theft
The threat landscape has shifted as the threat actor group known as ShinyHunters (also tracked as UNC5537) has evolved its tactics to target high-value cloud environments. These attackers are moving beyond simple data theft to orchestrate sophisticated campaigns that exploit the very infrastructure designed to protect corporate identities. By focusing on SaaS platforms—specifically targeting Single Sign-On (SSO) and Multi-Factor Authentication (MFA)—the group has successfully breached major cloud-based systems including Okta, Microsoft 365, and Google Workspace.
Mandiant, now part of Google Threat Intelligence, has identified that this group leverages these entry points to gain broad access to corporate data. Unlike traditional attackers, ShinyHunters specifically seeks to bypass modern security controls to perform large-scale data exfiltration and identity theft across an organization's entire cloud footprint.
Anatomy of the Attack
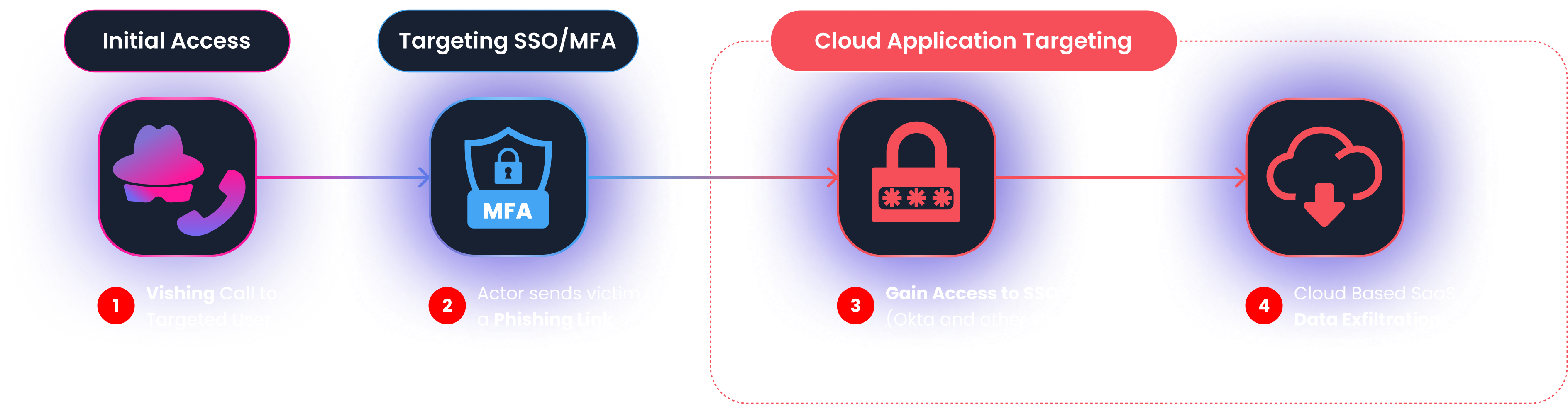
The Mandiant inquiry highlights how various clusters (UNC6661, UNC6671) use vishing to breach enterprise networks. These sophisticated campaigns follow a structured path to bypass modern defenses:
1. IT Help Desk Impersonation
Threat actors initiate the attack by pretending to be IT staff. They contact employees at targeted organizations, establishing trust to deceive them into believing the call is a legitimate internal request.
2. Social Engineering for MFA Access
Under the guise of providing instructions to update multi-factor authentication (MFA) settings, attackers direct victims to fraudulent, victim-branded credential harvesting sites. The goal is to capture both primary credentials and MFA authentication codes in real-time.
3. Persistence and Lateral Movement
Once the credentials are stolen, the attackers use them to register their own devices for MFA. This grants them a persistent foothold, allowing them to move laterally across the network and access critical SaaS platforms like Okta, SharePoint, and OneDrive.
4. Data Exfiltration and Weaponization
The threat actors leverage tools like PowerShell to download sensitive corporate data for the purpose of large-scale data theft and extortion. In some instances, they weaponize compromised email accounts to send further phishing emails to external contacts, such as cryptocurrency-focused companies, before deleting the messages to hide their tracks.
Closing the Gap
Phishing simulations are a necessary foundation, but they are no longer sufficient on their own. To defend against groups like ShinyHunters, organizations must move toward a unified awareness strategy that integrates voice-based threats into their training playbooks.
Relying on siloed training is no longer effective; employees must learn to pause, verify, and report across all communication channels. To counter sophisticated, real-time threats, CISOs should modernize their awareness programs to reflect actual attacker behavior.
1. Integrate Phishing and Vishing Simulations
Training for email threats in isolation leaves critical security gaps that attackers will exploit.
- Merge phishing and vishing into a single social engineering strategy.
- Ensure the reporting process for both suspicious emails and calls is identical and familiar.
- Use simulations based on actual tactics like IT desk scams and CEO fraud that blend multiple techniques.
Prepare for Multi-Stage Hybrid Flows
Modern campaigns use cross-channel layering to build fraudulent credibility.
- Simulate emails that prompt victims to call a fraudulent support line.
- Test employees with phone calls that "confirm" a previous phishing email.
- Prepare staff for deepfake voicemails that direct them toward phishing sites.

