During a phishing simulation, you will retrieve behavioral data and be able to determine your level of resilience. But what are the results to observe following a false phishing campaign and how to exploit them?
Definition Of KPIs
Click rate, compromise rate, reporting rate, these are the performance indicators you have to evaluate your digital protection. The initial objective of the simulations is to strengthen your company's resilience against phishing. This involves improving the behavior of your employees when confronted with a phishing attempt.

Firstly, the click rate is a good overall indicator of your company's security. A simple click is the first entry point in a phishing attack. Even though its exploitation is more rare, a simple click can lead to the user being hacked, for example in the case of a vulnerability in an un-patched browser. Your employees who have "just" clicked have not identified any threats and are therefore likely to make other mistakes in a real situation.
In just one click, your company's activity can be impacted. That's why the goal of these tests is to get as close as possible to 0 clicks.
Secondly, we are interested in the total compromise rate, when an employee provides login credentials or opens an infected attachment. In a different context, if it were not a simulation, this action could have serious consequences for the company. Therefore, it is necessary to pay particular attention to the future results of these employees in order to reduce the compromise rate as much as possible.
Now let's look at the rate we want to see increase: the reporting rate. Indeed, this rate allows you to have an idea of the number of employees in your company who are properly trained in fighting against phishing and actively participate in your defense, at least for the phishing scenario used during your campaign.
The reporting rate

Reporting helps to fight against phishing in general. By raising the alarm when a threat is detected, your employees reinforce the company's security. The reporting rate is a good indicator of the development of your "human firewall." Over the course of the campaigns, the goal is to see an increase in the rate of reporting of phishing emails, which means that your employees are adopting good reflexes and reporting the threats they perceive.
It is necessary to report the threat, even when an employee provides login credentials or any other sensitive data. Some might hesitate to report it when they realize they have made a mistake. That is why it is important not to be perceived as an enforcement body but rather as a support, an assistance in the face of cyber risks. In real attacks, if they are not reported, the impact on the company can be significant. It is therefore essential to train your employees on reporting.
Arsen offers a reporting button directly integrated into the messaging service. Your employees can easily report the threat to the security service, whether it's an Arsen phishing exercise or a real threat.
Behavioral data
Following a phishing simulation, you have access to several indicators that allow you to evaluate your resilience against phishing. The various compromise timings allow you to deduce behavioral patterns, such as those who click on the received email without taking the time to read it. If you observe a too short timing between opening the email and stealing login credentials, you can deduce that the individual did not take the time to analyze either the email or the login page before taking a compromising action.

These patterns help you put yourself in the shoes of your employees and will be a valuable support in training your workforce. By having access to the user journey, you obtain details about the mistakes made. These will allow you to focus on specific points during the presentation of the campaign results.
Exploitation of results
Based on the behavioral information collected, you can identify the predominant problems. It is important to ask the right questions: Which groups of employees require particular attention? What are the most favorable times for phishing for your workforce? In which scenarios are your employees less vigilant? Then, tailor your next simulations based on what you have detected.
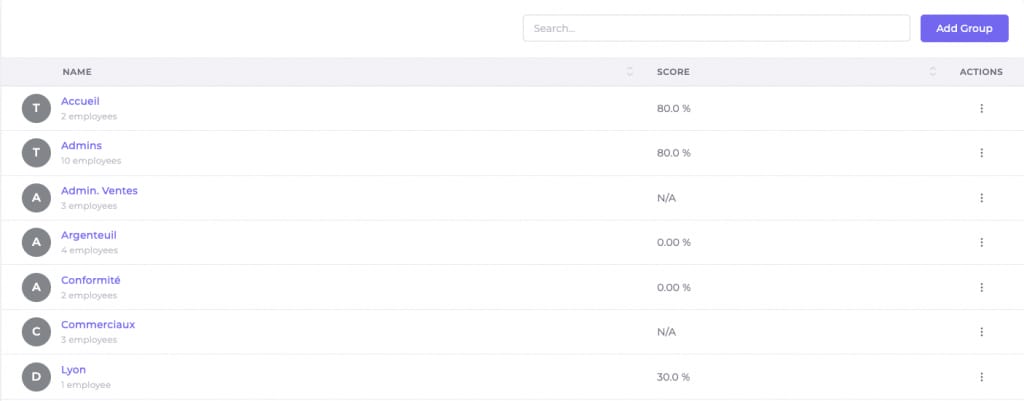
Comparing the scores of different groups in the phishing simulation platform allows you to determine which groups need to be prioritized for awareness.
Use awareness campaigns to evaluate and train your company's workforce and thus reduce the click and compromise rates. The data from future simulations will allow you to assess the effectiveness of these campaigns on your employees. Adapt these campaigns based on the vulnerabilities you have identified in the company. Some groups of employees will be more susceptible to certain psychological levers, so educate your employees about these social engineering techniques.
Finally, it is necessary to train your users on reporting. Whether using the Arsen reporting plugin or another internal process, reporting phishing emails should become a reflex at the slightest doubt about a potential attack. By increasing the reporting rate, your company will be better protected and operational against digital threats.
In summary, every compromise, whether it's a simple click or stealing login credentials, should not be taken lightly. Over time, you should observe a decrease in these rates and an increase in reporting.
The different behavioral data will then allow you to intensify the level of difficulty of your scenarios by adapting them to the vulnerabilities you have identified.

