
The Era of "Dark LLMs": How AI is Supercharging Social Engineering
The AI revolution of the 2020s has positioned Large Language Models (LLMs) as the new foundation for digital transformation. With unparalleled data processing power and text comprehension, LLMs can...

How Sophisticated Vishing Attacks are Currently Bypassing SSO for Wide-Scale SaaS Data Theft
The ShinyHunters group is currently orchestrating vishing attacks and exploiting SSO to bypass multi-factor authentication. These sophisticated campaigns have led to breaches of cloud platforms like...

The New Vishing Playbook: Attackers Can now Control the Flow in Real-Time and Break SSO
Identity attacks are evolving into hybrid vishing operations. New phishing kits allow attackers to manipulate a victim’s browser in real-time, syncing web visuals with phone scripts to perfectly...
New in Arsen: Turn a Simple Prompt into a Comprehensive Defense Strategy
Our latest release note: Building effective cybersecurity training takes time. Arsen’s new AI-assisted builder combines hyper-realistic simulations with customizable learning paths that blue teams...

How Quishing Can Be Weaponized to Target Top Organizations: The North Korea’s Kimsuky Case
The FBI warns that North Korean group Kimsuky is using quishing to target organizations. Discover how bad actors exploit QR codes to bypass security controls and how to test your defense against...

The InboxPrime Case: AI-Based Phishing Kits, Or The New Frontier of Credential Theft
AI and LLMs are creating a paradigm shift in cyberattacks. Attackers now use AI-powered kits to automate the entire attack lifecycle with unprecedented speed and precision. CISOs must adapt awareness...
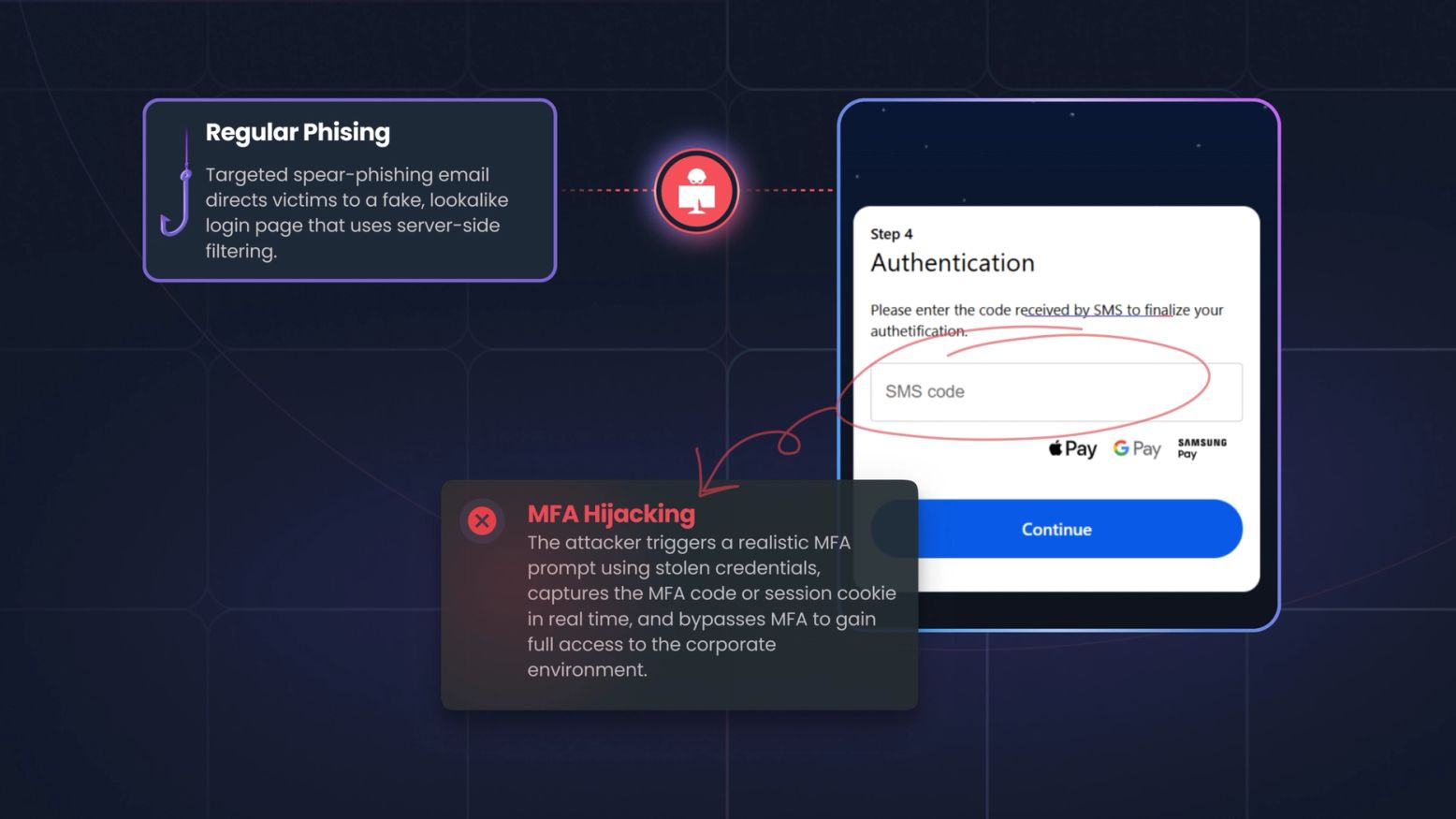
The BlackForce MitM Phishing Kit & MFA Hijacking: When Your Credentials Are No Longer Enough
Phishing has evolved. Zscaler ThreatLabz recently revealed BlackForce, a toolkit hijacking active sessions and bypassing MFA, using the "Man-in-the-Middle" (MITM ) attack tactic. CISOs must update...
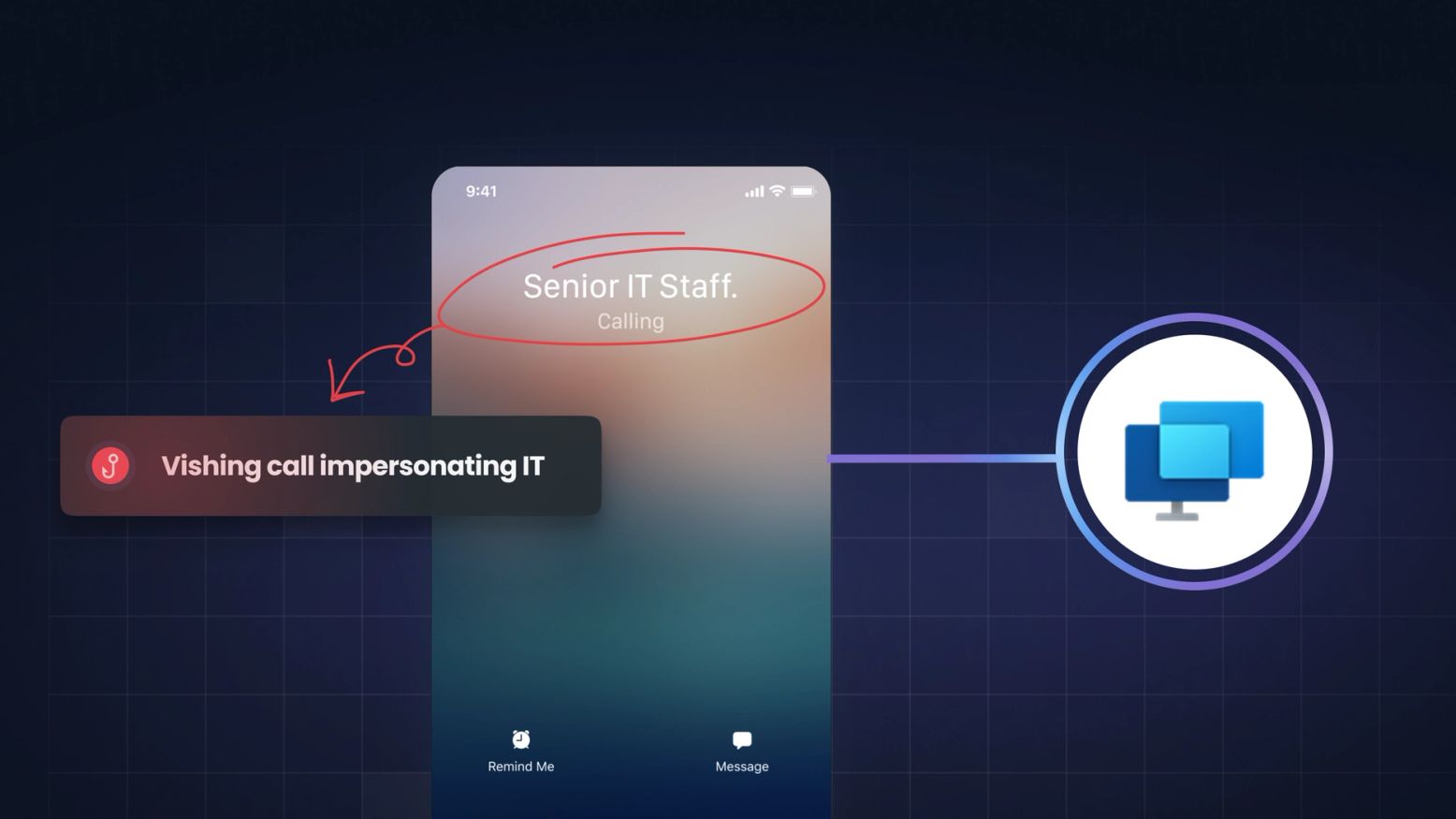
Vishing And The "Quick Assist" Trap: How Attackers Weaponized A Trusted Microsoft Tool
A new vishing campaign weaponizing Microsoft Teams and Quick Assist for fileless malware execution was recently revealed. Learn how this hybrid attack bypasses defenses and why AI-driven vishing...
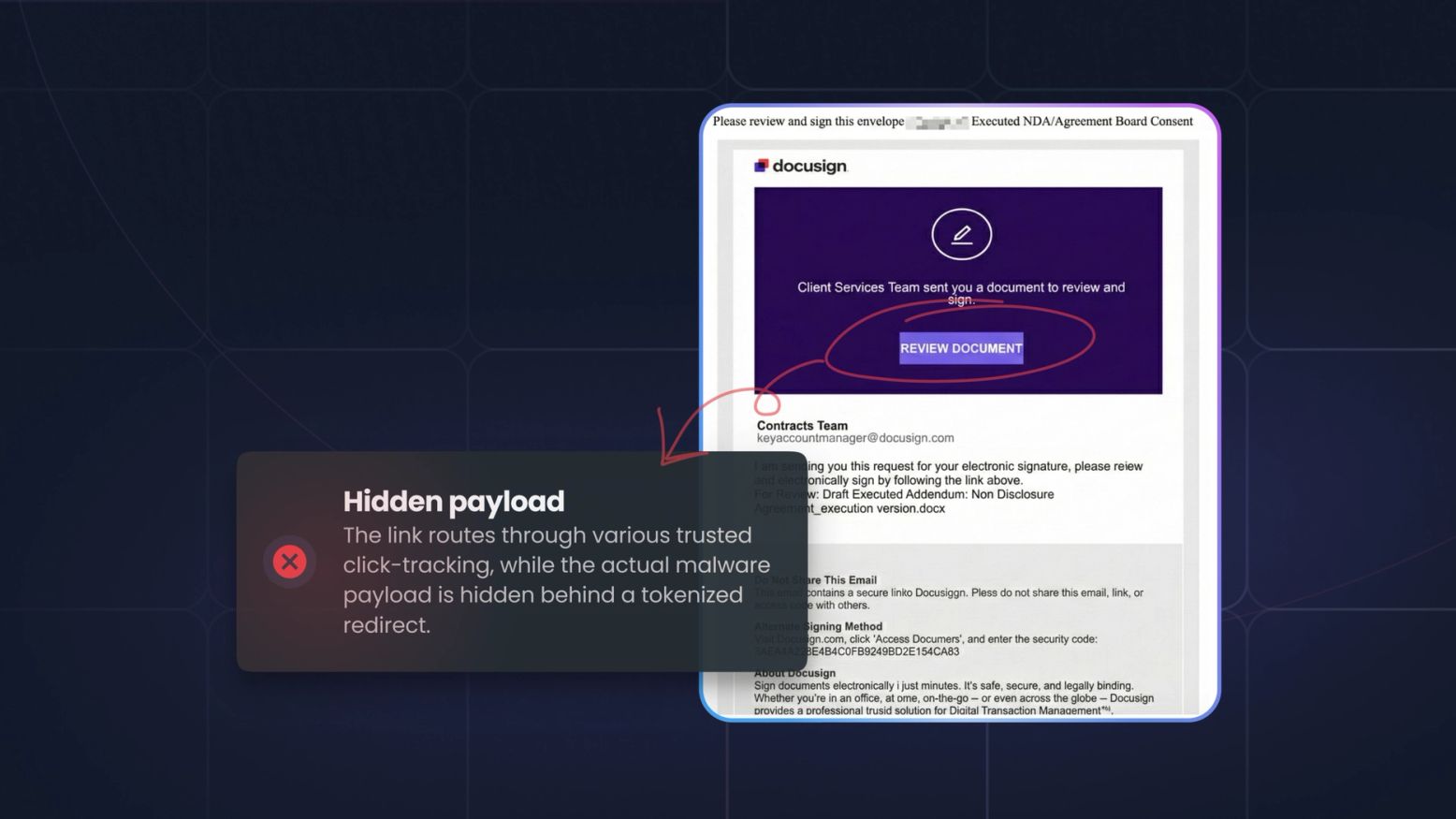
How Hundreds of Financial Institutions Were Hit by Massive Phishing and How to Prevent It
A recent massive phishing campaign targeted financial institutions by weaponizing trusted services like Mimecast and DocuSign. Discover how these attacks bypass filters and learn how to protect your...

Cybersecurity Awareness Training and FERPA: Securing Student Records Through Education
The Family Educational Rights and Privacy Act (FERPA) protects the privacy of student education records in the United States. While FERPA places legal obligations on schools, universities, and...

How Cybersecurity Awareness Training Supports the NIST Cybersecurity Framework
The NIST Cybersecurity Framework (CSF) is a widely adopted set of best practices for managing cybersecurity risks across all sectors — from critical infrastructure to cloud-native startups. It...

Cybersecurity Awareness Training for CCPA / CPRA Compliance: Empowering Employees to Protect Consumer Privacy
The California Consumer Privacy Act (CCPA) and its expanded version, the California Privacy Rights Act (CPRA), have redefined how businesses must handle personal data in the U.S. These laws emphasize...

PCI-DSS and Cybersecurity Awareness Training: Protecting Cardholder Data from Human Risk
The Payment Card Industry Data Security Standard (PCI-DSS) is a mandatory framework for any organization that stores, processes, or transmits cardholder data. While most PCI compliance efforts focus...

HIPAA Compliance and Cybersecurity Awareness: Training for Healthcare Data Protection
The Health Insurance Portability and Accountability Act (HIPAA) mandates the protection of Protected Health Information (PHI) across healthcare providers, insurers, and business associates. While...

Cybersecurity Awareness Training and NIS2 Compliance: Securing the Human Layer in Critical Sectors
The NIS2 Directive (Directive (EU) 2022/2555) represents a significant expansion of the EU’s cybersecurity legislation, aimed at strengthening resilience across critical infrastructure and digital...

Cybersecurity Awareness Training for DORA Compliance: Managing Human Risk in Financial Services
The Digital Operational Resilience Act (DORA) is the European Union’s new regulatory framework aimed at strengthening the operational resilience of financial services — including banks, fintechs,...

Cybersecurity Awareness Training and ISO 27001: A Practical Compliance Guide
ISO/IEC 27001 is one of the most widely recognized standards for Information Security Management Systems (ISMS). Whether you're pursuing certification or maintaining compliance, one thing is clear:...

Meeting SOC 2 Type II Requirements with CSAT
SOC 2 Type II has become the gold standard for demonstrating security and trustworthiness in the SaaS and technology sectors. Unlike Type I, which evaluates controls at a point in time, Type II...

How Cybersecurity Awareness Training Supports GDPR Compliance
Since the introduction of the General Data Protection Regulation (GDPR) in 2018, organizations operating in or serving the EU have faced strict requirements for how they handle personal data. While...

What Is Bad Rabbit Ransomware? How It Works & How to Stop It
In the world of cybersecurity, Bad Rabbit ransomware has made headlines as one of the more sophisticated and dangerous ransomware attacks. This malware first surfaced in 2017, targeting companies...

WannaCry Ransomware Attack: A Case Study
The WannaCry ransomware attack, which occurred in May 2017, stands as one of the most significant and destructive cyberattacks in recent history. It serves as a critical lesson for organizations...

Cybersecurity Regulatory Compliance — Key Strategies for CISOs
In today's digital age, regulatory compliance is a critical aspect of running a successful business. Ensuring that your company adheres to applicable laws and regulations helps avoid legal penalties,...

Compliance Risk: Identification and Mitigation
In today's highly regulated business landscape, compliance risk is a critical concern for organizations across industries. Failing to comply with laws and regulations can result in severe penalties,...

Compliance Monitoring: Ensuring Policy Adherence
Effective compliance monitoring is critical for ensuring that organizations consistently adhere to internal policies and regulatory requirements. As companies face increasing scrutiny from regulatory...

Compliance Management: Effective Strategies
Effective compliance management is essential for organizations to meet legal obligations, protect their reputation, and maintain operational integrity. As regulations evolve, businesses must adopt...

CCPA (California Consumer Privacy Act) Compliance: Complete 2024 Guide
The California Consumer Privacy Act (CCPA) is a pivotal data privacy law that grants consumers more control over their personal information. For businesses operating in or interacting with California...

IT Compliance: Navigating Regulations in Tech
In today’s rapidly evolving tech landscape, **IT compliance** plays a critical role in ensuring organizations meet legal and regulatory requirements. Failure to comply can lead to severe penalties,...

What Is a VPN? How It Works & Why You Need One
In today's increasingly digital world, safeguarding online privacy has become more crucial than ever. One of the most effective ways to protect your personal information while browsing the web is by...

What Does VPN Stand For? Understanding Its Use
In today’s interconnected world, ensuring your online privacy and security is more crucial than ever. One of the most effective tools for safeguarding your digital presence is a **VPN**. But what...

VPN Definition: Virtual Private Networks Best Practices
A VPN (Virtual Private Network) is a tool that enhances your online security by encrypting your internet connection and masking your IP address. This makes it an essential part of modern digital...

Examples of Data Breaches and Lessons Learned
Data breaches have become a persistent threat to organizations of all sizes. By analyzing data breaches examples, we can uncover key lessons for safeguarding sensitive information. Below are some...

Data Breach Response and Prevention Strategies
In today’s digital landscape, data breaches are a constant threat. Companies of all sizes are vulnerable to these attacks, making it crucial to adopt effective prevention and response strategies....

SSTP: Secure Socket Tunneling Protocol Explained
The Secure Socket Tunneling Protocol (SSTP) is an important player in ensuring secure and private communication over the internet. Often used in Virtual Private Networks (VPNs), SSTP provides a...

DNS Security: Best Practices to Protect Your Network
In today's digital landscape, DNS security is a crucial aspect of safeguarding any organization’s network. The Domain Name System (DNS) acts like the internet’s phonebook, translating domain names...

Watering Hole Attack: What It Is & How to Prevent It
Watering hole attacks are an increasingly sophisticated cyber threat, targeting specific groups or organizations by compromising websites they frequently visit. In this article, we will break down...

DNS Meaning: What Does DNS Stand For?
When exploring the complex world of the internet, the term "DNS" frequently pops up. But what does DNS stand for, and why is it important? This article will break down the DNS meaning and explain its...

Employee Phishing Training — Empower Your Workforce Against Attacks
Phishing training for employees is essential in building defense skills against cyberattacks. By educating employees on how to recognize and respond to phishing attempts, businesses can reduce the...

Phishing Training — Build Employee Awareness & Resilience
Phishing training is essential for protecting your organization from cyberattacks. By educating employees on how to recognize and respond to phishing threats, you can reduce the risk of data breaches...

Build Phishing Awareness & Protect Your Organisation
Phishing awareness is essential to safeguarding your business from cyberattacks. Learn how to recognize phishing attempts, understand common tactics used by attackers, and implement strategies to...

Defense in depth: the importance of the human factor
A paradox has struck me for several years now. Everyone I speak to is convinced of the predominance of human risk. The internet is full of statistics linking initial access to employee behavior in...
The cybersecurity of nomadic remote work
After seeing how to secure your remote work at home, we will now talk about mobility situations: working remotely outside. Laptops are blossoming on café terraces and it is pleasant to answer a few...

Companies: How to secure teleworking
The use of teleworking has exploded and represents a major trend. This brings new challenges in terms of cybersecurity. Between the perceived improvement in quality of life for many employees and...

Why generate a random password?
Often, when an individual needs to create a new password, they will rack their brains and choose personal information that relates to them, then modify it by changing elements or adding special...

How to properly manage your passwords
Managing identification, and more specifically passwords, is a key lever in cybersecurity. This is part of [good cybersecurity practices](/blog/personal-cybersecurity): if you have a good password...
What is Juice Jacking ?
Juice jacking is a type of cyber attack that exploits USB charging cables or chargers to compromise devices with USB ports, especially mobile phones. Charging cables don't just power your phone's...
General cybersecurity recommendations for businesses
Very often during discussions with our clients, we realize that some basics of cybersecurity are not necessarily mastered. It is both common and dangerous. Cybersecurity is everyone's business and...
Good practices of personal cybersecurity
We live in an increasingly connected world. Everyone has a phone with capabilities that surpass most computers available a few years ago, telecommuting is strengthening, most employees have a...

What is a sextorsion attack?
A sextortion attack involves extorting money by blackmailing with a sexual theme. For instance, the malicious individual contacts the victim claiming to have a video of them in a compromising...
Cybersecurity and work from home
In this article, we will focus on cybersecurity at home, or how to secure your telecommuting from home. The rules and best practices explained in this article apply to telecommuting of all kinds,...

Why are you losing money with your awareness solution?
In this article, we will discuss the limitations of different awareness solutions. The goal is not to criticize these types of solutions, but to present the missing parts so that you can either fill...

Securing telecommuting: the complete guide
How to secure telecommuting? In recent months, we have published various articles on cybersecurity and telecommuting. Indeed, the context of the health crisis has led to an increase in...


