With the rise of large language models and AI, we are witnessing a fundamental paradigm shift in how cyberattacks are conducted. Attackers now rely on sophisticated, AI-powered kits that automate the entire attack lifecycle, from generating compromise materials to configuring operational workflows and technical parameters.
For CISOs, this evolution creates a new challenge: building security awareness programs that accurately reflect how modern attackers operate, using sophisticated attack kits. These attacks are increasingly complex and coordinated, with a single adversary able to engage victims across multiple channels simultaneously. AI further amplifies the threat by enabling large-scale campaigns with unprecedented precision, personalization, and speed.
Let’s take a closer look at attack schemes recently uncovered in the cybersecurity landscape that reveal how generative AI is reshaping the threat environment.
InboxPrime: Phishing Email Generation on Autopilot with Generative AI
Identified by AbnormalAI, InboxPrime AI has surfaced on cybercrime forums for approximately $1,000. The kit reframes phishing as a high-end marketing operation rather than a crude attack. It includes a real-time spam diagnostics module powered by large language models that generates highly polished, tailored phishing emails.
By recommending precise edits to evade email security filters, the tool enables low-skill attackers to launch professional, error-free phishing campaigns across multiple languages. At the core of this approach is InboxPrime’s AI-driven content engine, which automatically produces complete phishing assets, from subject lines to full HTML email bodies, designed to closely mimic legitimate business communications.
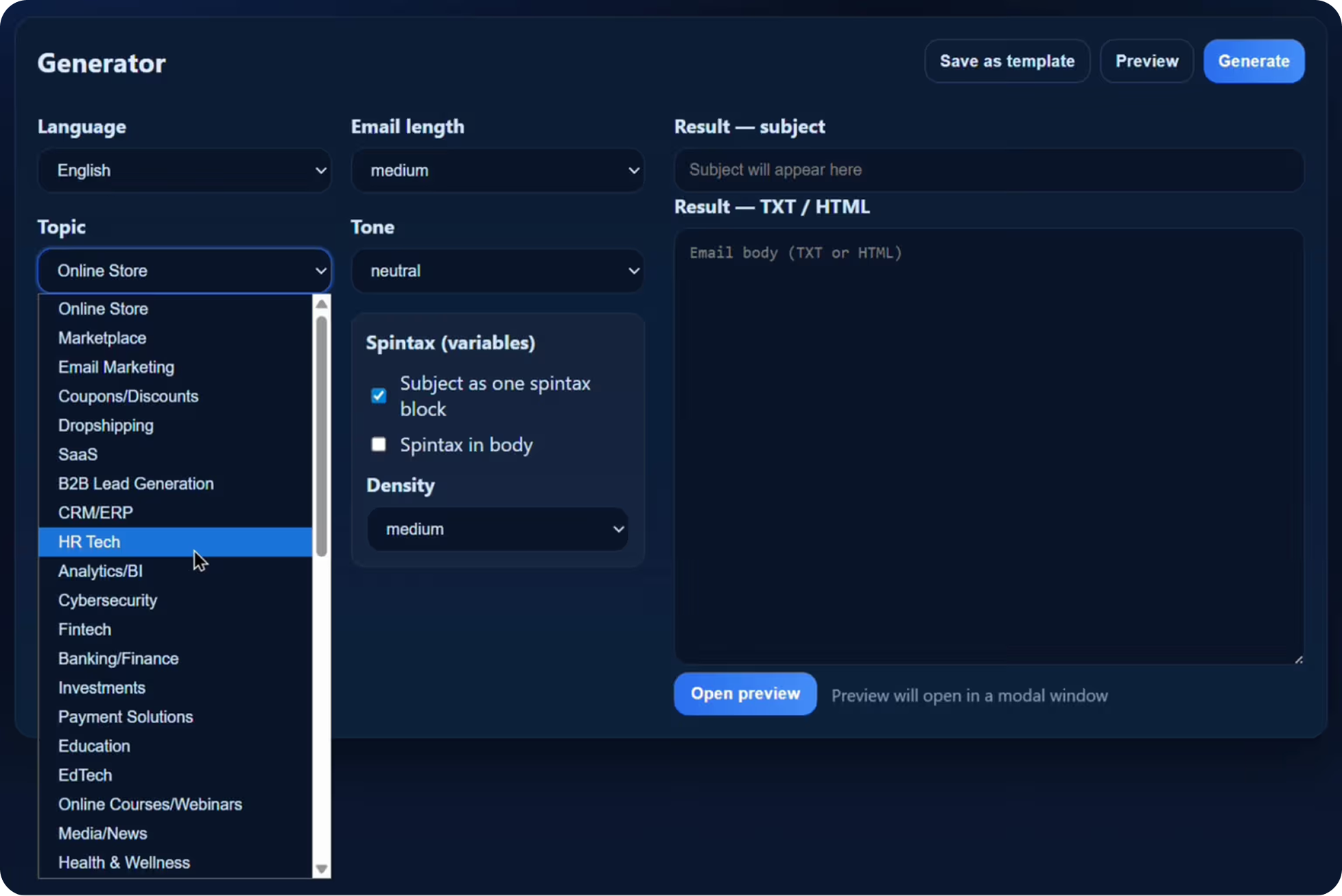 The attacker-facing setup panel used to specify a phishing email’s theme, language, and communication style prior to content generation. The interface includes tone controls that allow messages to be tailored to distinct audience profiles. Image courtesy of Abnormal AI.
The attacker-facing setup panel used to specify a phishing email’s theme, language, and communication style prior to content generation. The interface includes tone controls that allow messages to be tailored to distinct audience profiles. Image courtesy of Abnormal AI.
Key capabilities include:
- Customizable Parameters: Attackers can specify language, industry, message length, and tone, allowing the AI to generate highly targeted and believable phishing content.
- Scale and Consistency: Automated content generation removes manual effort, accelerates campaign deployment, and maintains consistent quality without requiring copywriting skills.
- Tone Selection: The interface supports specialized styles, such as an “expert” tone for Analytics or Business Intelligence themes, producing professional-looking emails that exploit trust in technical subject matter.
- Evasion via Spintax: Template variables are used to introduce subtle variations in each email, ensuring no two messages are identical and helping bypass basic signature-based detection mechanisms.
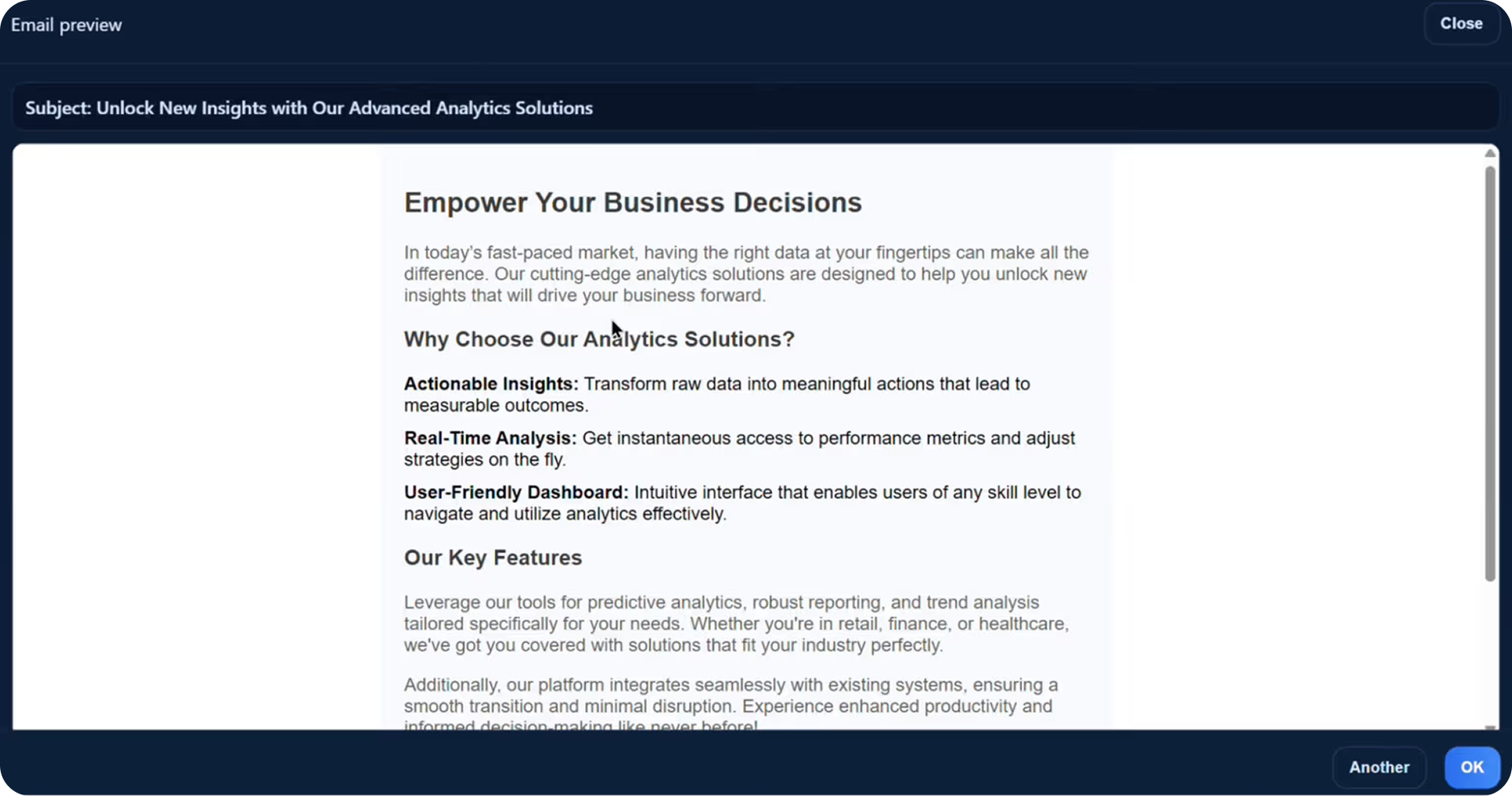 A sample HTML phishing email automatically generated based on the chosen topic and tone configuration. Image courtesy of Abnormal AI.
A sample HTML phishing email automatically generated based on the chosen topic and tone configuration. Image courtesy of Abnormal AI.
The Massive Spread Of LLMs in Phishing Kits
Attackers are increasingly incorporating LLMs into their workflows, using them to produce linguistically precise, contextually relevant, and psychologically manipulative content that enhances social engineering across phishing, vishing, and business email compromise (BEC) campaigns, while also leveraging their code fluency to rapidly generate, modify, and debug functional code, including malicious scripts and customized malware, dramatically accelerating tooling and malware development; however, these same capabilities can also be harnessed by defenders to speed up detection, analysis, and response.
Learn more about AI-enabled cyber awareness training →
Recent findings from cybersecurity research teams show how the widespread adoption of LLMs and automation is reshaping phishing kits and enabling credential theft at scale, as tools like BlackForce, GhostFrame, and Spiderman increasingly rely on AI to optimize evasion, persistence, and targeting, BlackForce dynamically adapts man-in-the-browser evasion scripts based on the victim’s environment to bypass detection, GhostFrame uses intelligent fallback mechanisms to intercept MFA tokens and sustain attacks when primary scripts are blocked, and Spiderman, uncovered by Varonis, orchestrates highly polished, real-time credential harvesting by filtering victims through AI-driven geographic and ISP-based controls, illustrating how modern phishing operations now function as adaptive, data-driven attack platforms rather than static toolkits.
The Evolution of AI-Driven Phishing: Targeted Precision On Steroids
Historically, the risk imbalance in cybersecurity has favored the attacker. While an organization must defend every employee, an attacker only needs one successful point of entry. Until recently, this scale was limited by a manual bottleneck: attackers couldn't easily personalize high volumes of messages without sacrificing quality.
Generative AI has permanently shifted this landscape. We are moving away from the era of "mass spammers" toward highly sophisticated, targeted attackers who invest significant capital into bespoke infrastructure. These entities operate with a high ROI mindset, leveraging AI to eliminate the traditional "red flags", like poor grammar and clumsy formatting that employees are usually taught to spot.
The Rise of Contextual Intelligence
Modern attacks no longer rely on a single, suspicious link. Instead, they utilize Contextual Intelligence to build synchronized narratives that feel like native business processes.
- Hyper-Personalized "Barrel" Phishing: Attackers use Generative AI to scrape Open-Source Intelligence (OSINT), crafting multi-stage conversations that build rapport over days. By the time a "security" incident is raised, the victim has been primed to trust the source as a legitimate internal entity.
- AI-Generated Vishing: Voice attacks have evolved into highly personalized, AI-generated calls. For example, an "IT representative" may call a user to "warn" them about a security sync, establishing a verbal bond of trust minutes before a phishing email arrives. This multi-channel approach makes the subsequent digital attack feel like a sanctioned resolution.
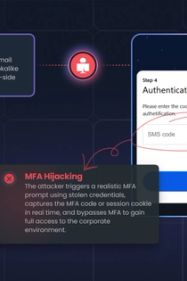
The New Frontier: Real-Time MFA Bypass
As organizations adopt Multi-Factor Authentication (MFA), attackers have evolved their methods to bypass it in real-time. The modern threat is no longer about tricking a user into reading a code over the phone; it is about the Man-in-the-Middle (MitM) attack.
Sophisticated attackers now deploy synchronized phishing kits that act as a live proxy between the victim and the legitimate service. When a victim enters their credentials on a perfectly cloned login page, the attacker intercepts the session token directly.
Why this matters: Intercepting tokens on the phishing page is far more effective than legacy methods. It creates zero friction for the victim and allows the attacker to maintain access without needing to repeatedly prompt the user for codes.
This "synchronous" phishing ensures that the moment a victim interacts with a prompt, the attacker is already inside the live session.
Strengthening the Human Firewall
Traditional, static phishing simulations can’t keep pace with the high-investment infrastructure used by modern attackers. To transform your employees into a resilient first line of defense, your training must evolve from generic templates to realistic, AI-driven offensives.
The Arsen Checklist for Modern Defense:
- Deploy Synchronized Hybrid Attacks: Move beyond simple emails by blending AI-generated vishing with phishing kits to mirror real-world multi-channel threats.
- Utilize Adaptive Narratives: Implement simulations that evolve based on user interaction, replicating the persistence and "barrel phishing" tactics of sophisticated attackers.
- Integrate Multi-Channel Playbooks: Train staff to use the same reporting protocols whether a threat arrives via email, a personalized voice call, or a hybrid conversational scheme.
- Highlight Real-World Attacker Playbooks: Focus on the most effective modern tactics, such as urgent IT help desk interventions and high-stakes executive impersonation.
- Leverage Defensive Automation: Use automated platforms to scale your awareness programs, ensuring your training frequency can match the rapid speed of AI-generated threat cycles.
Ready to see how your team stands up against the next generation of social engineering?