 Image courtesy of Zscaler ThreatLabz
Image courtesy of Zscaler ThreatLabz
In the current cyber threat landscape, email phishing remains the first entry point for social engineering, but attackers have evolved far beyond the inbox. The Zscaler ThreatLabz team recently uncovered a new sophisticated phishing toolkit called BlackForce. Such toolkits are redefining the penetration chain by focusing not just on stealing passwords, but on hijacking the entire authentication session. For CISOs, the challenge is clear: traditional awareness training must evolve to reflect how attackers actually operate, moving from simple "link-clicking" metrics to defending against real-time multi-channel pressure.
Anatomy of the BlackForce Attack
Summary of the BlackForce attack model
- The Tool: BlackForce is a specialized phishing kit designed to bypass Multi-Factor Authentication (MFA) through session hijacking.
- The Chain: It uses a transparent reverse proxy to sit between the user and the real service, capturing credentials and MFA tokens in real-time.
- The Vulnerability: Man-in-the-Middle (MitM) attacks can break traditional forms of multi-factor authentication, with the exception of FIDO2, where the cryptographic key proving user identity is securely bound to the device and cannot physically be extracted or intercepted.
- The Action: Organizations must unify attack simulations into a single social engineering playbook.
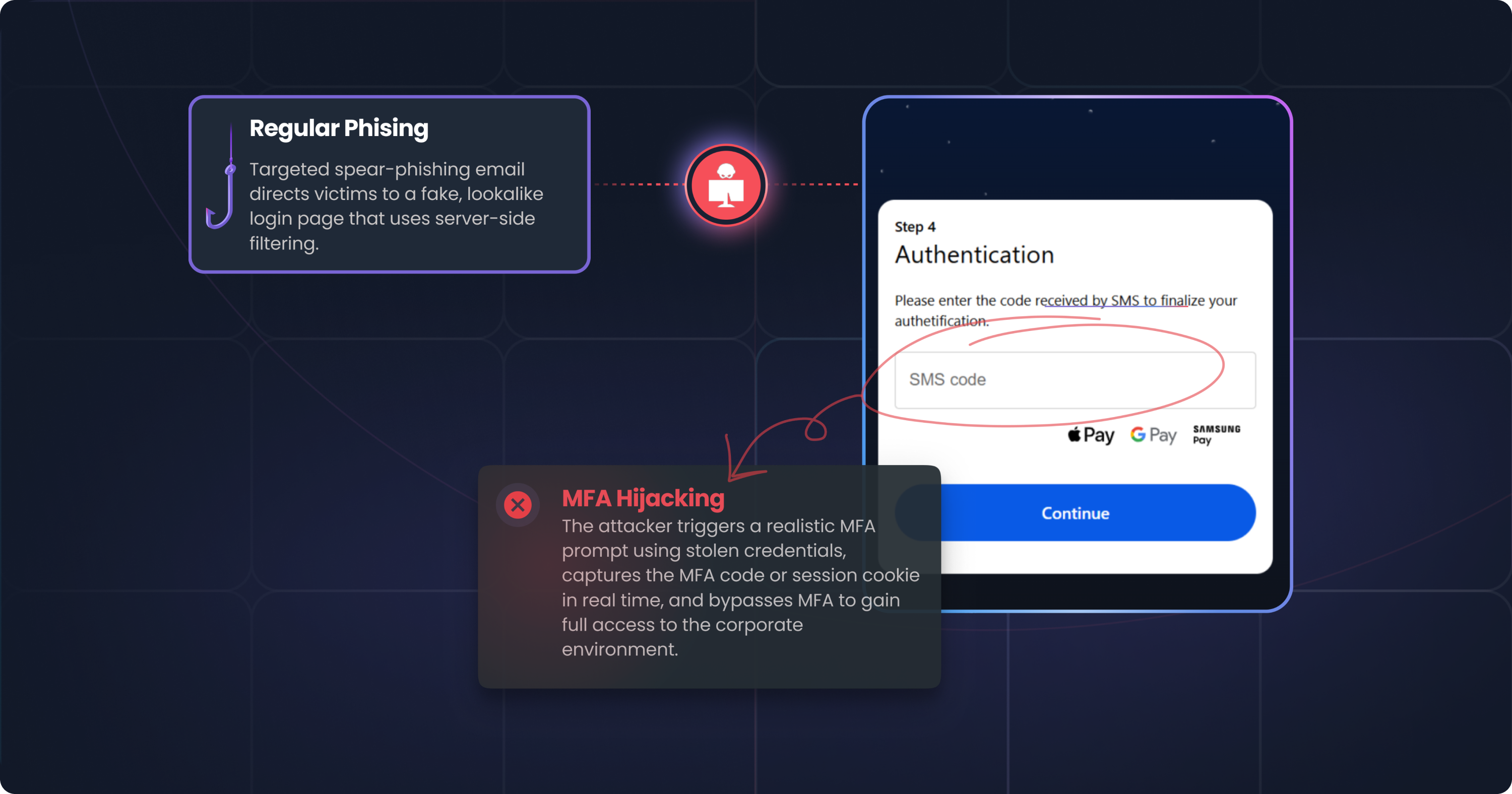
The attack starts with a targeted email that lures a victim to a site designed to look like a legitimate login. To stay hidden, the kit uses server-side filtering to block security scanners, showing the fraudulent content only to the intended target. Once the employee enters their credentials, the data is immediately sent to the attacker’s command center.
The attacker then uses these stolen credentials to log into the legitimate service, triggering a real MFA prompt on the victim's device. By sitting between the user and the real website, the kit captures the MFA code or session cookie as the victim enters it. This allows the attacker to bypass MFA entirely, gaining authenticated access to the corporate environment.
Phishing is the use of psychological manipulation to influence targets toward a specific outcome. While the medium is often text or email, the strategy is increasingly asynchronous, designed to lure a victim into a trap that triggers a real-time response. With the BlackForce kit, the attack chain follows the "Man-in-the-Middle" (AiTM) approach, enabling real-time MFA bypass:
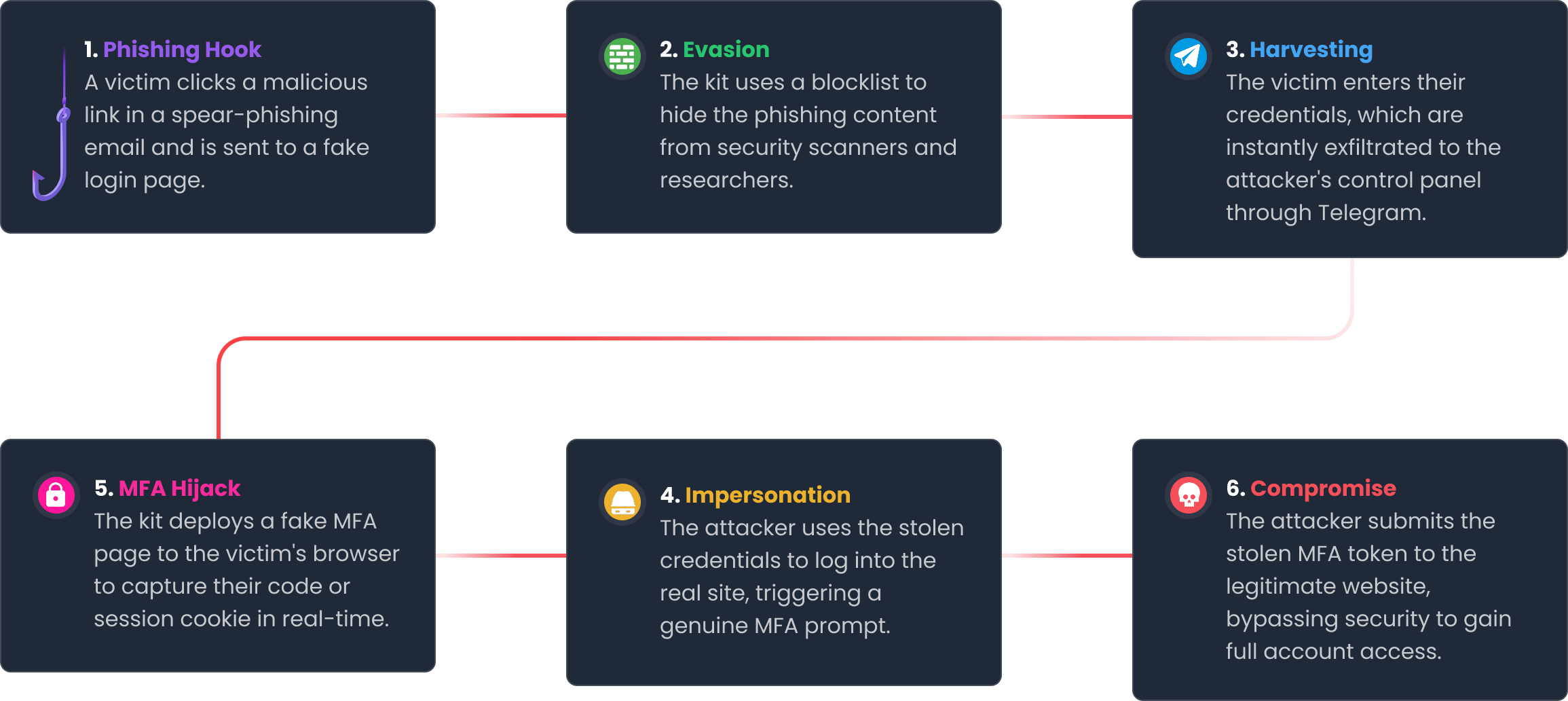
- The Lure: The victim receives a highly targeted spear-phishing email, impersonating HR or a trusted supplier.
- The Proxy: The link directs the victim to a fake login page that closely replicates a legitimate service. The kit transparently proxies the real login flow.
- The Intercept: As the victim enters their credentials, the kit captures the session and relays it to the legitimate service, triggering a real MFA challenge while simultaneously intercepting the MFA response.
- The Compromise: With the captured MFA token or session, the attacker fully bypasses MFA and gains authenticated access to the corporate environment, without needing to crack or brute-force anything.
The Rise of MFA Hijacking and MITM Attacks
While MFA is a vital layer, the "standard" version is no longer a silver bullet. Sophisticated threat actors have shifted their tactics from simple password theft to MFA Hijacking, using Man-in-the-Middle proxies to bypass even the most robust authentication chains.
It functions by hijacking an active, authenticated session in real-time rather than simply stealing static credentials.
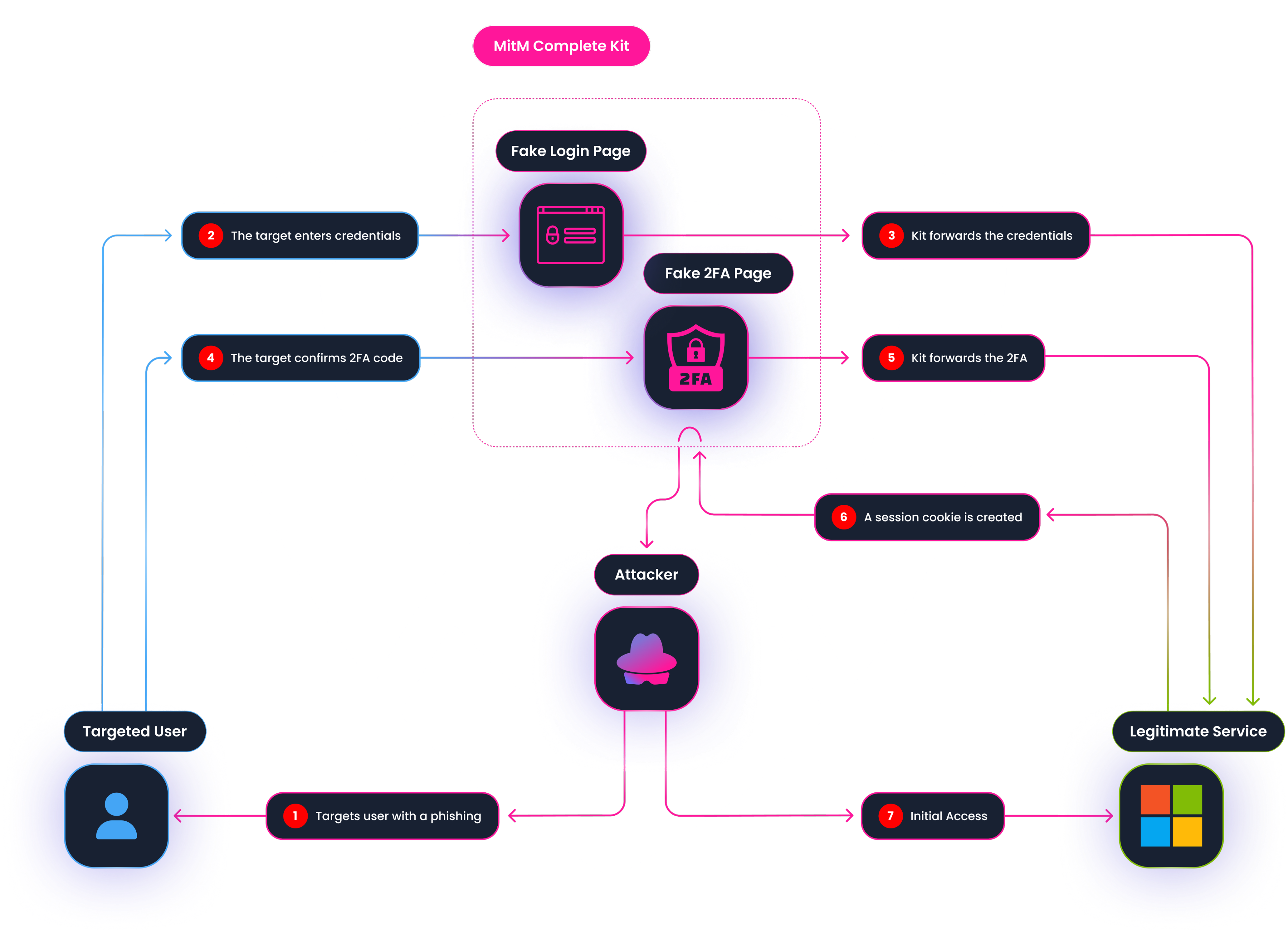
→ As we saw with BlackForce, the process begins with a coordinated lure that directs the victim to a reverse proxy server controlled by the attacker. This server acts as a real-time bridge, fetching and displaying the actual login page from a legitimate service to the user.
→ As the victim enters their password and MFA code, the proxy intercepts these inputs and passes them to the legitimate site to complete the login.
→ Once the real site validates the session and issues an authorization token (a session cookie), the attacker intercepts this token before it reaches the victim's browser. By injecting this stolen cookie into their own browser, the hacker can impersonate the victim and gain full account access, effectively bypassing the MFA requirement because the security challenge has already been solved.
The technical proxy could be paired with Vishing (Voice Phishing) to increase the success rate. A realistic login chain, sometimes rendered even more realistic thanks to AI-assisted kits, including a genuine-looking page and a real MFA request, layered with a convincing human voice or a sense of urgency, makes a victim far more likely to comply. By the time the victim realizes something is wrong, the attacker has already hijacked the active session.
Actionable Takeaways for CISOs
The evolution of these threats proves that "standard" phishing training is no longer enough. Attackers are no longer just looking for passwords; they are hijacking your identity in real-time.
- Train for Multi-Stage Attacks: Employees must be taught to recognize that a phone call or an MFA prompt following an email can be part of a single, coordinated hybrid attack.
- Focus on MFA Behavior: Training should move beyond "don't click" to "don't comply on the spot." Employees should be taught to verify any unexpected MFA request through an official internal channel before taking action.
- Deploy Advanced Simulations: Use platforms like Arsen to simulate these exact scenarios, combining AI-driven phishing with vishing and MFA tentatives, to prepare your team for the next generation of threats.
Mastering the Human Factor with Arsen
At Arsen, we help organizations close the training gap by simulating the threats attackers actually use today. Our platform goes beyond simple email tests to provide a comprehensive resilience strategy:
- Phishing & Spear-Phishing: Deploy realistic simulations that test your team’s ability to spot the most advanced lures and proxy-based redirections.
- Vishing & Smishing: Test how your employees handle real-time voice and SMS-based pressure during a login attempt.
- Deepfake & AI Simulations: Prepare for the next generation of voice-cloning and hybrid threats designed to bypass traditional security layers.

