Approving transactions, signing contracts, and sharing critical financial workflows now happens with a single click, with trusted and famous platforms. But as security professionals as well as hackers know all too well, convenience is often the enemy of security. Recent research from Check Point has uncovered a massive phishing campaign that turns trusted tools against firms. By impersonating file-sharing and e-signature giants, attackers have launched a precision strike against the financial, real estate, and consulting sectors, targeting thousands of companies.
Here is a breakdown of this latest campaign and how financial institutions can build a defense that actually works.
 Image courtesy of Check Point
Image courtesy of Check Point
1. The Classic "Trusted Source" Threat
In this recently discovered incident, attackers didn't just spoof a brand; they abused the security infrastructure itself. Over a two-week period, 40,000 phishing emails were deployed, targeting roughly 6,100 customers around the world.
The innovative part was mimicking Mimecast’s secure-link rewriting feature. All malicious links were funneled through https://url.za.m.mimecastprotect.com. Because Mimecast Protect is a known, trusted domain, these links bypassed automated filters and, critically, lowered the user's suspicion threshold.
But it did not stop there. Attackers relied on high-fidelity social engineering to mimic the notifications employees receive daily, combining visual deception with advanced technical evasion.
2. Anatomy of the Attack
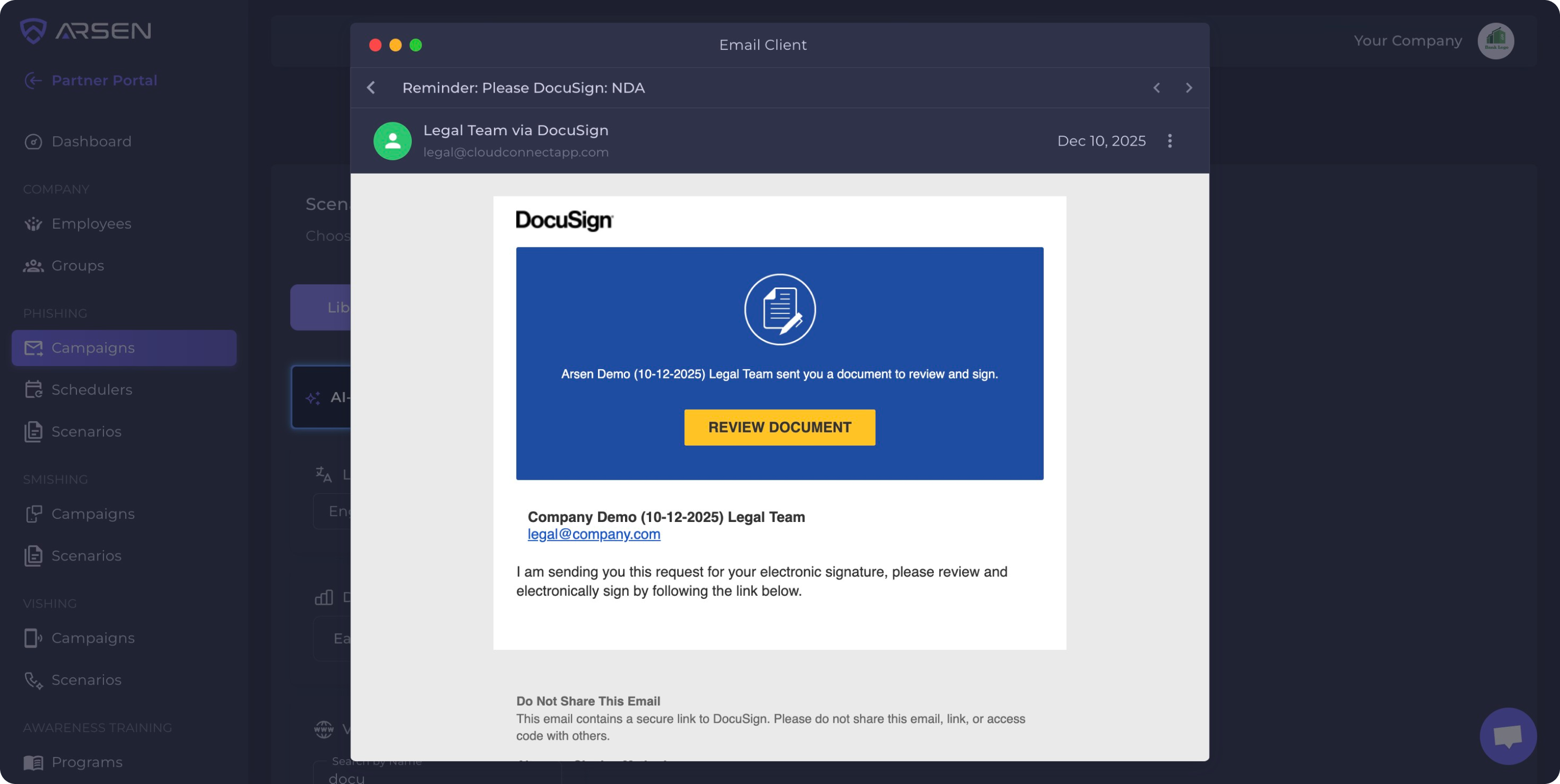
Researchers at Check Point have analyzed two distinct, elaborate email phishing campaigns targeting businesses: a massive one using the Mimecast strategy explained above, and a smaller, highly sophisticated, and stealthier variant targeting DocuSign users.
To boost credibility, the emails in the main campaign were nearly indistinguishable from legitimate notifications. They deployed:
- Official Visuals: Microsoft and Office product logos were used to establish immediate trust.
- Service-Style Formatting: Headers, footers, and “Review Document” buttons matched authentic notification patterns perfectly.
- Spoofed Display Names: Senders appeared as “X via SharePoint (Online)”, “eSignDoc via Y”, or simply “SharePoint.”
The DocuSign variant is particularly dangerous because of its complex redirect chain designed to blind security scanners:
- Initial Redirect: The link moves through a Bitdefender GravityZone URL.
- Tracking Layer: It then passes through Intercom’s click-tracking service.
- The Payload: The final malware destination is hidden behind a tokenized redirect.
Unlike the main campaign, where the query string might still reveal the phishing URL, this "DocuSign" method conceals the final URL entirely. A dangerous evasion method, making the attack stealthy and incredibly hard to detect for standard email gateways.
This campaign was a very large operation spanning the U.S., Europe, Canada, and the Middle East. While it affected industries that routinely exchange contracts—such as Consulting, Technology, and Construction—the Financial Services sector was particularly targeted as well. Attackers capitalized on the high volume of sensitive transactional documents exchanged by banks and investment firms, making the "Sign this document" bait highly convincing and significantly increasing the risk for institutions managing client assets.
3. Protecting Financial Institutions
This attack highlights a critical reality: Trusting the sender or the URL domain name ISN’T ENOUGH. If Mimecast and Bitdefender links can lead to credential harvesting, employees must go further than the classic "hover to verify" advice.
At Arsen, we empower financial services and assurances firms such as the one impacted here to assess and train employee at scale and regularly against the most ingenious and insidious types of threats. We do this by allowing organizations to send ultra-realistic simulations to test staff resilience, including classic email phishing, smishing, and sophisticated AI-generated voice phising attacks.
Here is your checklist to close these security gaps using a unified approach:
- Mirror Real-World Attacks: Don't rely on generic templates. Launch simulations that mimic similar, sophisticated DocuSign attack vector, as well as account takeover, CEO fraud, and SWIFT manipulation attempts. Every campaign should be tuned to the tools your frontline teams use daily.
- Personalize Payloads by Function: A teller faces different threats than a trader. Customize your phishing scenarios for wealth management, commercial banking, capital markets, or payment operations to ensure relevance and high engagement.
- Turn Errors into Instant Enablement: When an employee clicks a simulated malicious link, deliver just-in-time micro-learning immediately. Eliminate long classroom sessions in favor of bite-sized, AI-enabled lessons that relationship managers and executives will actually complete.
- Monitor Beyond the Inbox: Defense isn't just about what comes in; it's about what is already out there. Discover your human risk exposure by monitoring dark web sources for compromised employee credentials before they are used in a credential stuffing attack.
- Enforce Manual Verification: Train teams to spot mismatches between display names and actual sender addresses. Encourage employees to open sensitive platforms (like SharePoint or DocuSign) directly in their browser rather than trusting email links, even if they appear to pass through security filters.
Audit-Ready and Resilient Financial Firms, with Arsen
For financial services, effective awareness is also a compliance necessity. By centralizing phishing simulations, security training, and risk reporting, Arsen helps you satisfy FFIEC, DORA, PCI DSS, and SWIFT CSP expectations without slowing down the business. Whether it is reducing payment fraud exposure through targeted drills or safeguarding third-party workflows by benchmarking partner exposure, the goal remains the same: prove compliance in minutes and ensure your human firewall is as sophisticated as the threats targeting it.

