QR code phishing, commonly called "quishing", represents an increasingly common attack method that merges physical accessibility with online fraud. As companies have strengthened their protections against conventional email phishing, attackers have pivoted to quishing, capitalizing on vulnerabilities in both security systems and user psychology.
Among others, state-sponsored actors are constantly refining their playbooks to bypass security controls. In a recent flash alert, the FBI warned that the North Korean hacker group Kimsuky (also known as APT43) is now utilizing malicious QR codes in spearphishing campaigns targeting U.S. organizations. Quishing isn’t new, but its adoption by state-backed threat actors highlights just how effective this technique remains as a security bypass.
Let’s recap. 👇
The Kimsuky Quishing Campaign
Kimsuky is a state-backed North Korean threat group known for deploying sophisticated attacks, exploiting vulnerabilities, and using supply-chain intrusion tactics, mostly to fund illegal North Korean military developments. Their latest campaigns target organizations involved in policy, research, and analysis, including NGOs, think tanks, academic institutions, and government entities. Most notably, it targets selected individuals through spearfishing methods, where the attempt to get people to click or scan the QR codes is tailored to the person.
According to the FBI, these attackers send emails containing QR codes that redirect victims to malicious locations disguised as:
- Questionnaires targeted at policy and research analysts to harvest information.
- Secure drives purporting to host shared files or confidential documents.
- Fake login pages that specifically impersonate trusted portals like Microsoft 365, Okta, VPNs, or Google.
To build trust, the attackers impersonate foreign investors, embassy employees, or conference organizers. In one specific instance in June 2025, Kimsuky actors sent a strategic advisory firm a targeted email inviting recipients to a non-existent conference.
Quishing is an "MFA-Resilient" Threat
Traditional phishing techniques are increasingly mitigated by stronger protections such as 2FA and MFA. These controls are effective because the authentication environment is the same as the target environment the attacker is attempting to access. As a result, attackers must deploy more sophisticated attack architectures, such as man-in-the-middle attacks and proxy-based approaches, to bypass these defenses.
The FBI describes these quishing attacks as an "MFA-resilient identity intrusion vector." When a victim scans the QR code, they are routed through attacker-controlled infrastructure that fingerprints their device (collecting OS, IP address, and screen size). The QR code not only allows the attacker to bypass verification controls and more easily obfuscate a malicious link, but it also leverages a personal mobile device that is often unknown to the organization’s IT services. As a result, no security alerts are triggered, giving the attacker a largely unobstructed attack path.
Quishing: A "Siloed" Defense No Longer Works
A siloed approach to security awareness no longer works. Quishing exploits the gap between your secure corporate environment and your employees' own devices. It blends physical simplicity with digital deception. While many organizations have matured their defenses against text-based phishing, quishing exploits new gaps in both technology and human behavior.
1. Obfuscating the Link
With typical phishing emails, a vigilant user can hover over a hyperlink to verify the URL. QR codes remove this visual layer entirely. The destination only becomes visible after the code is processed by the mobile device’s camera.
2. Evading Email Security
Most Secure Email Gateways (SEGs) are designed to scan textual links and attachments. While some advanced systems now attempt to decode QR images, detection remains spotty due to variations in file type and resolution. This allows quishing emails to slip past filters that would otherwise block a malicious hyperlink.
3. The Mobile Gap
Perhaps the most critical factor is that quishing intentionally moves the attack from a secure workstation to a mobile device. These devices often lack the Endpoint Detection and Response (EDR) or strict network monitoring present on corporate laptops. Once on a mobile browser, phishing sites or credential stealers face fewer detection hurdles.
Strengthening Your Human Firewall
Attackers know that users simply don’t view QR codes as dangerous. They are ubiquitous in our daily lives, used for menus, payments, and check-ins, building a baseline of trust that attackers exploit. To defend against these attacks, the FBI recommends targeted employee training and QR code source verification.
At Arsen, we believe that phishing simulations are necessary, but no longer sufficient if they only test for clicked links. Your awareness program must simulate cross-channel attacks.
Test Your Defense
Addressing the quishing threat means going beyond legacy email security. It requires realistic simulations that test how your people respond when faced with these specific vectors.
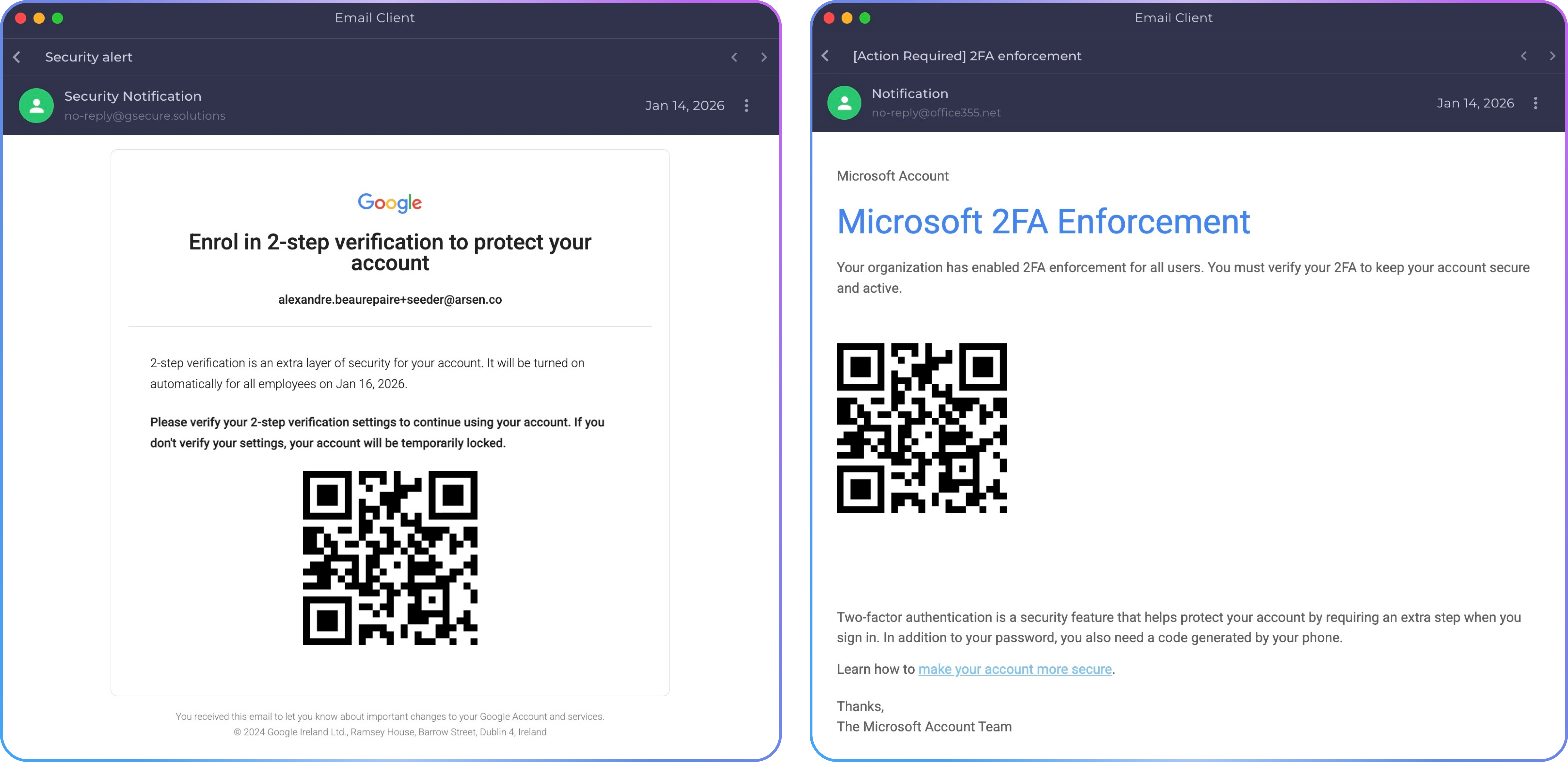 Examples of quishing simulation templates available in Arsen.
Examples of quishing simulation templates available in Arsen.
We offer free tools to help you identify your blind spots on quishing before malicious actors do:
- Try our QR Code Phishing Free Simulation: Curious to see if your team is prepared for modern threats? Test their behavior against QR code phishing today.
- Free QR Code Phishing Test: Do you think your mailbox is protected against phishing using QR Codes? Test it for free!
- QR Code Phishing: The Complete Protection Guide: Read our complete guide to learn how to protect your organization against QR code phishing attacks.

