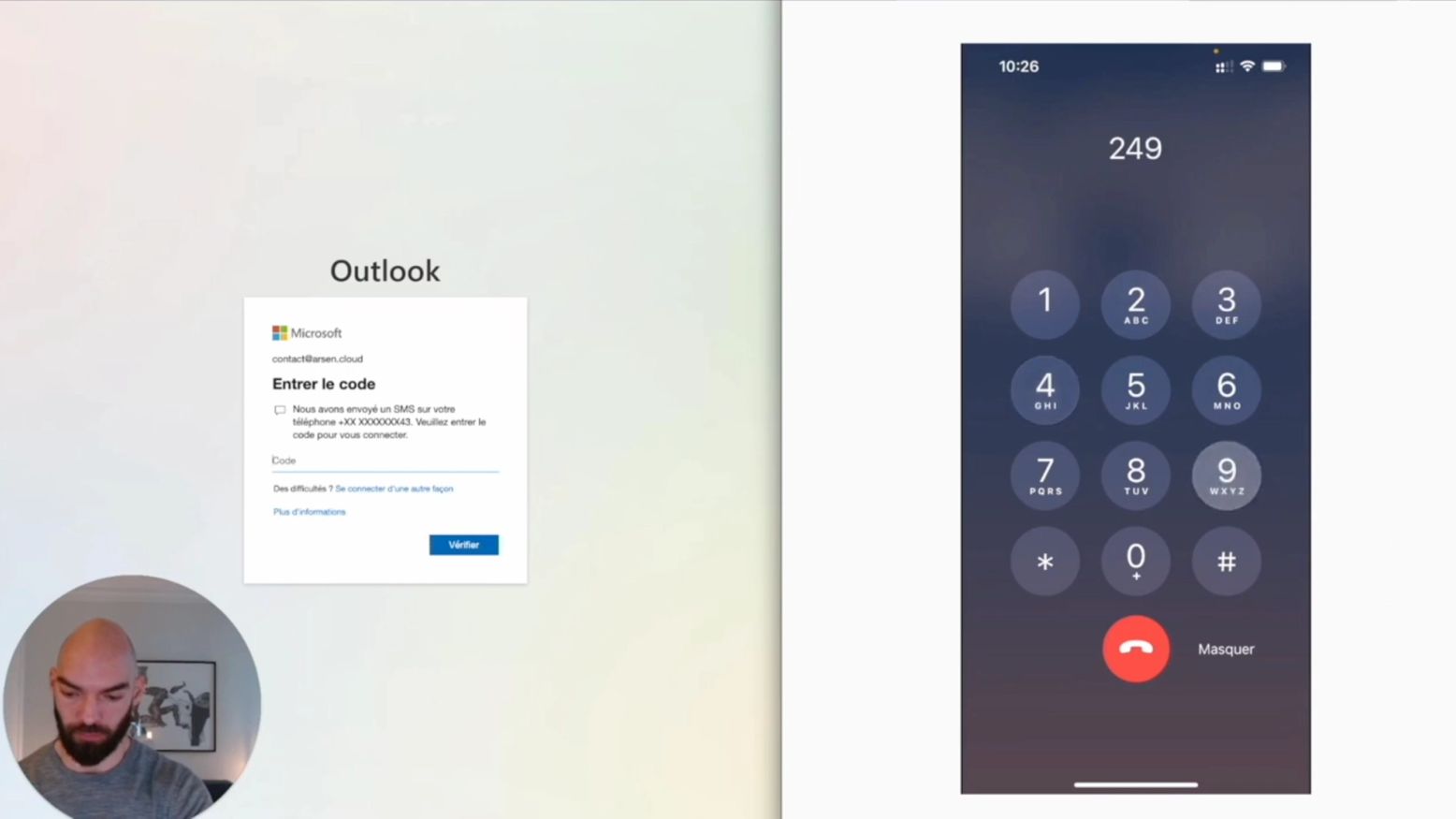
Bypassing Multi Factor Authentication (MFA) with a callbot
Call bots, a kind of vishing automation...

Domain Doppelgängers: Identifying and Protecting Against Domain Spoofing
Cybersecurity threats continue to...



How to launch a phishing simulation to better protect your company?
In this post, we'll explore the key...















Alternatives to GoPhish for Comprehensive Phishing Simulations
Phishing simulation tools have become...






What is phishing? Cyberattack's most popular initial access vector
Whether it's clicking on a malicious...

What are the results to observe during a phishing simulation?
During a phishing simulation, you will...

Click campaigns: lightweight phishing simulations to train people
Click campaigns are now available on...

Defeating Multi-factor Authentication through a Simple Phishing Email
In this article, I will show you in a...




What is Smishing? Definition, mechanisms, identifcation and examples
Did you know that SMS has an average...





Why carry out phishing simulations with groups of employees?
The aim of your phishing campaigns is...