
Effective generative AI for phishing engagements
If you’ve been reading our content, you’re probably itching to shoot some...

If you’ve been reading our content, you’re probably itching to shoot some...









"How would your team respond to a voice...
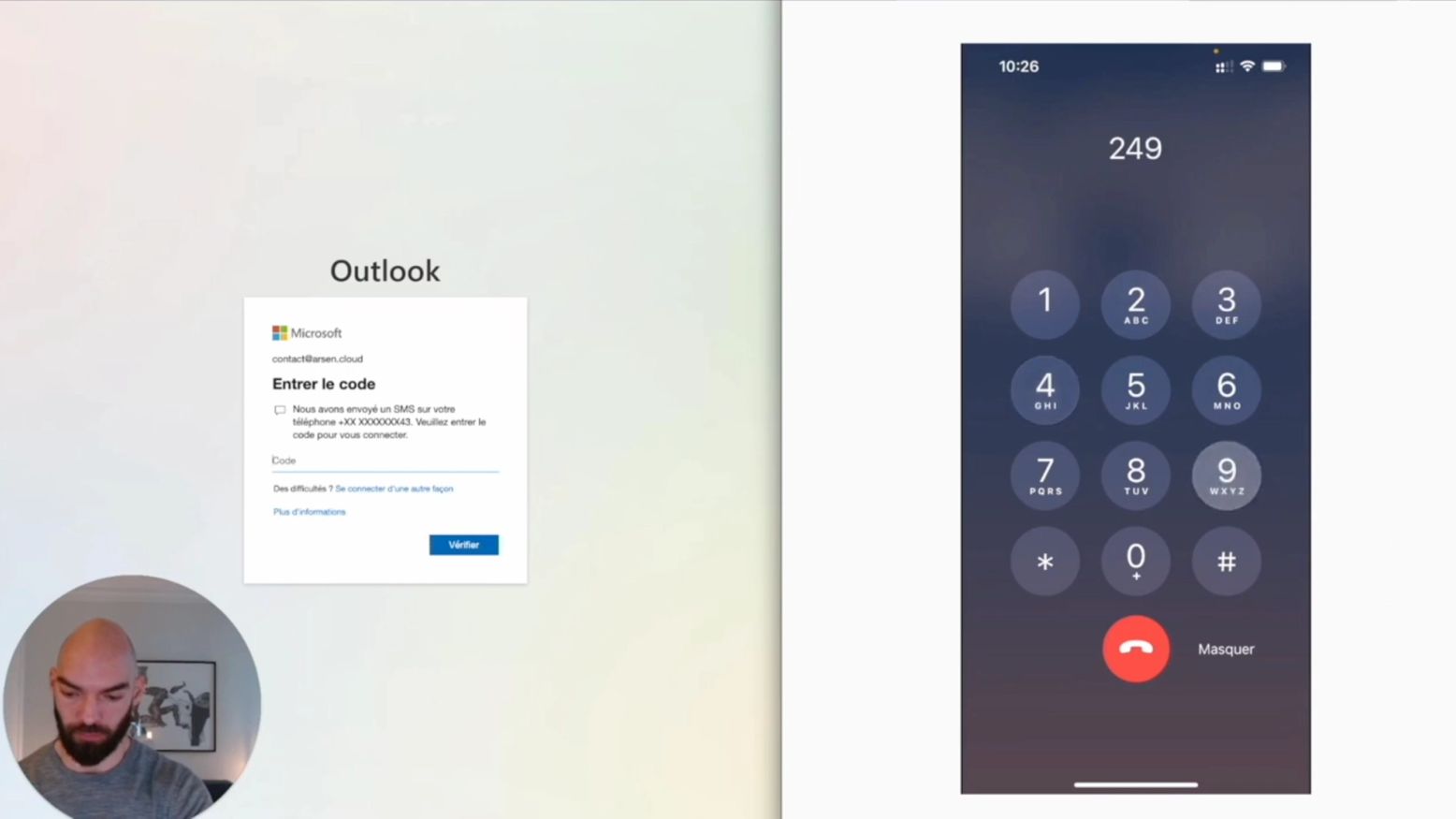
Call bots, a kind of vishing automation...

Cybersecurity threats continue to...







Ransomware is one of the most prominent...



HIPAA compliance is essential for any...




The California Consumer Privacy Act...








Pretexting is a social engineering...






Social engineering is a technique used...





In today’s digital age, Personal...


In this post, we'll explore the key...























Aymeric from Klaxoon explains why they...




Phishing simulation tools have become...








Whether it's clicking on a malicious...

During a phishing simulation, you will...


Click campaigns are now available on...


In this article, I will show you in a...

Ransomwares are becoming increasingly...

Cryptolocker is a notorious type of...


Originally, Emotet was a banking Trojan...






Did you know that SMS has an average...






The aim of your phishing campaigns is...

Discover how our phishing simulations can effectively reduce your human attack surface.
Request a DemoWe use cookies to ensure that we give you the best experience on our website. Read cookies policies