Arsen Security Blog
The BlackForce MitM Phishing Kit & MFA Hijacking: When Your Credentials Are No Longer Enough
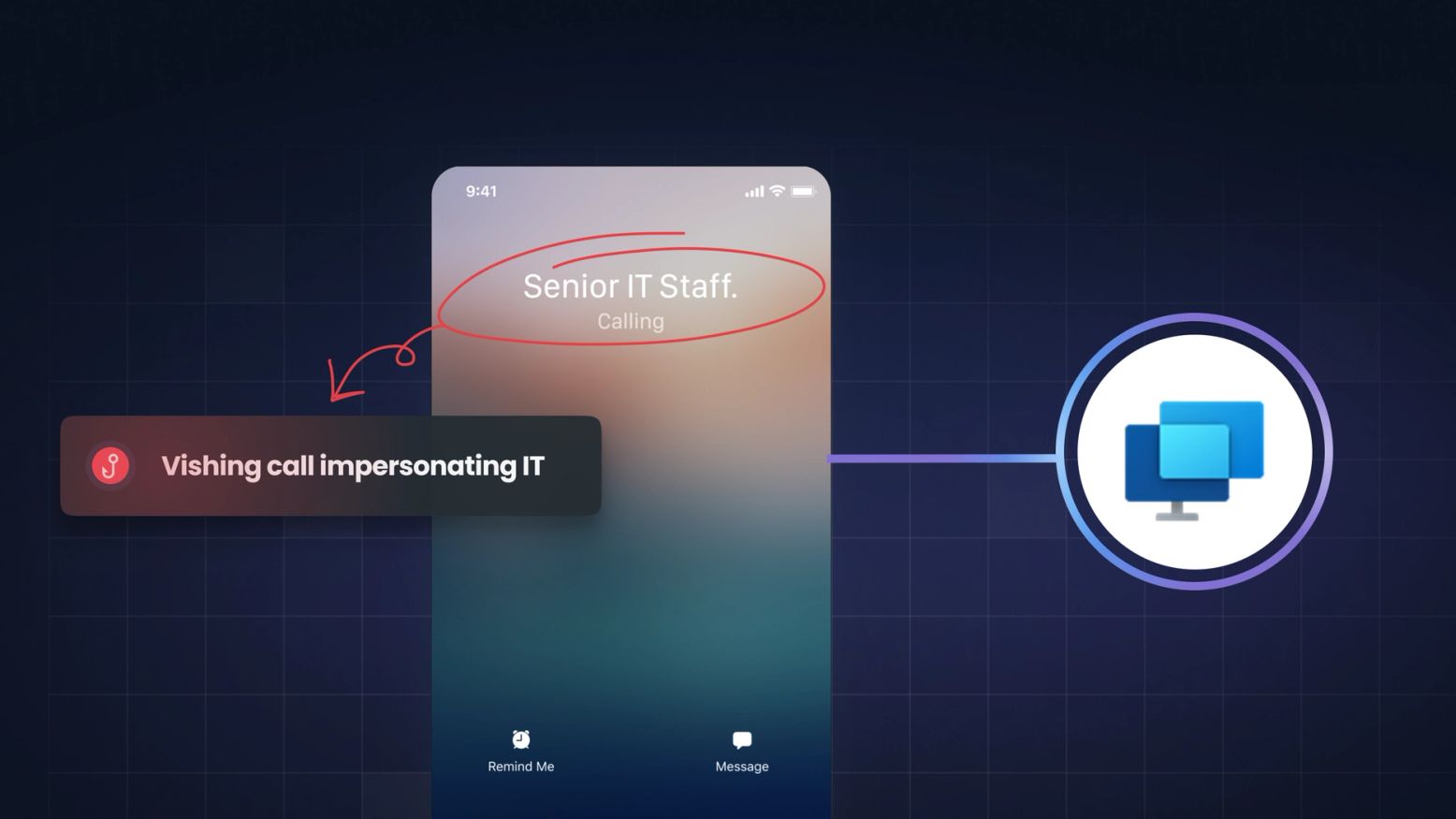
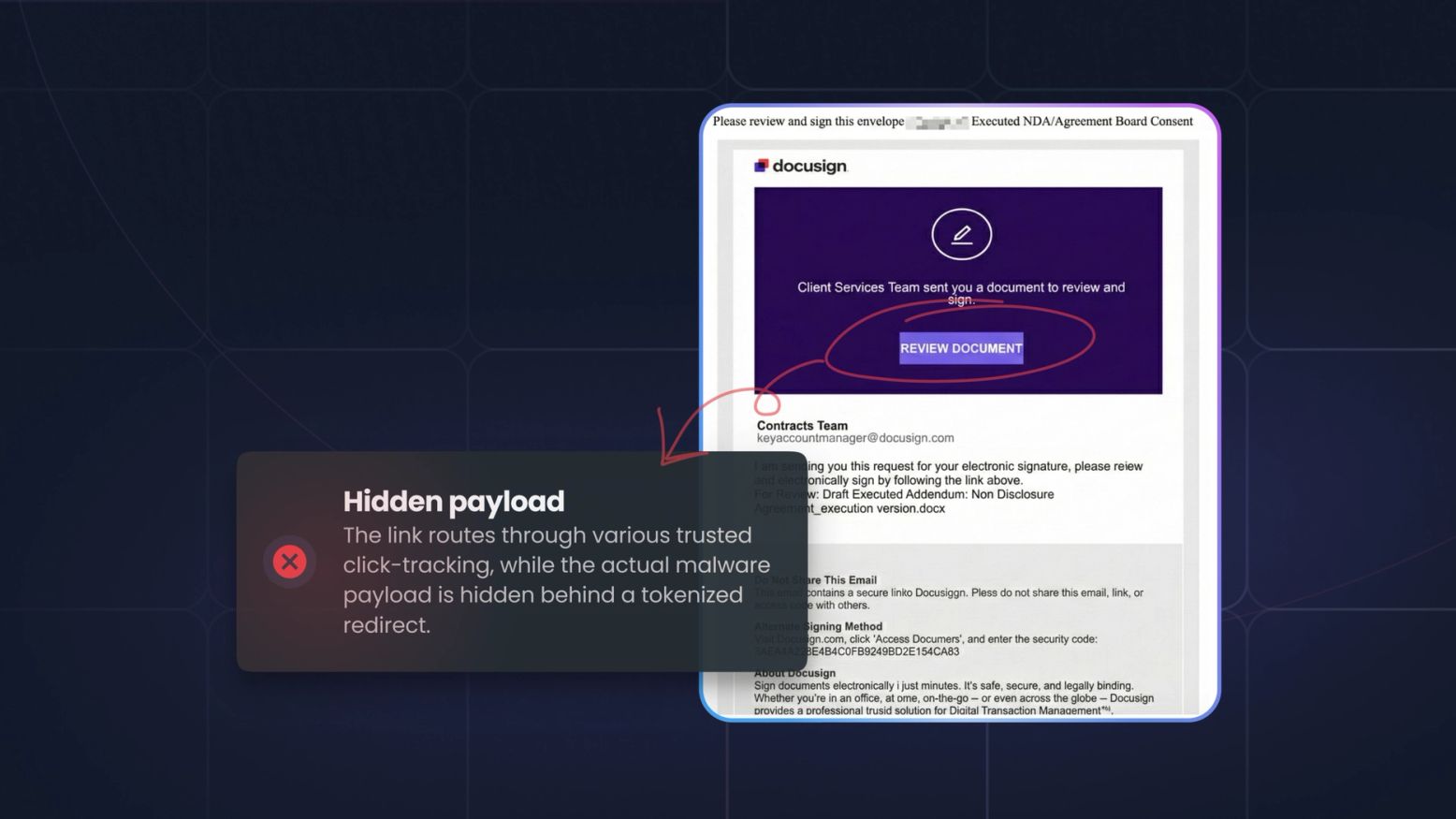
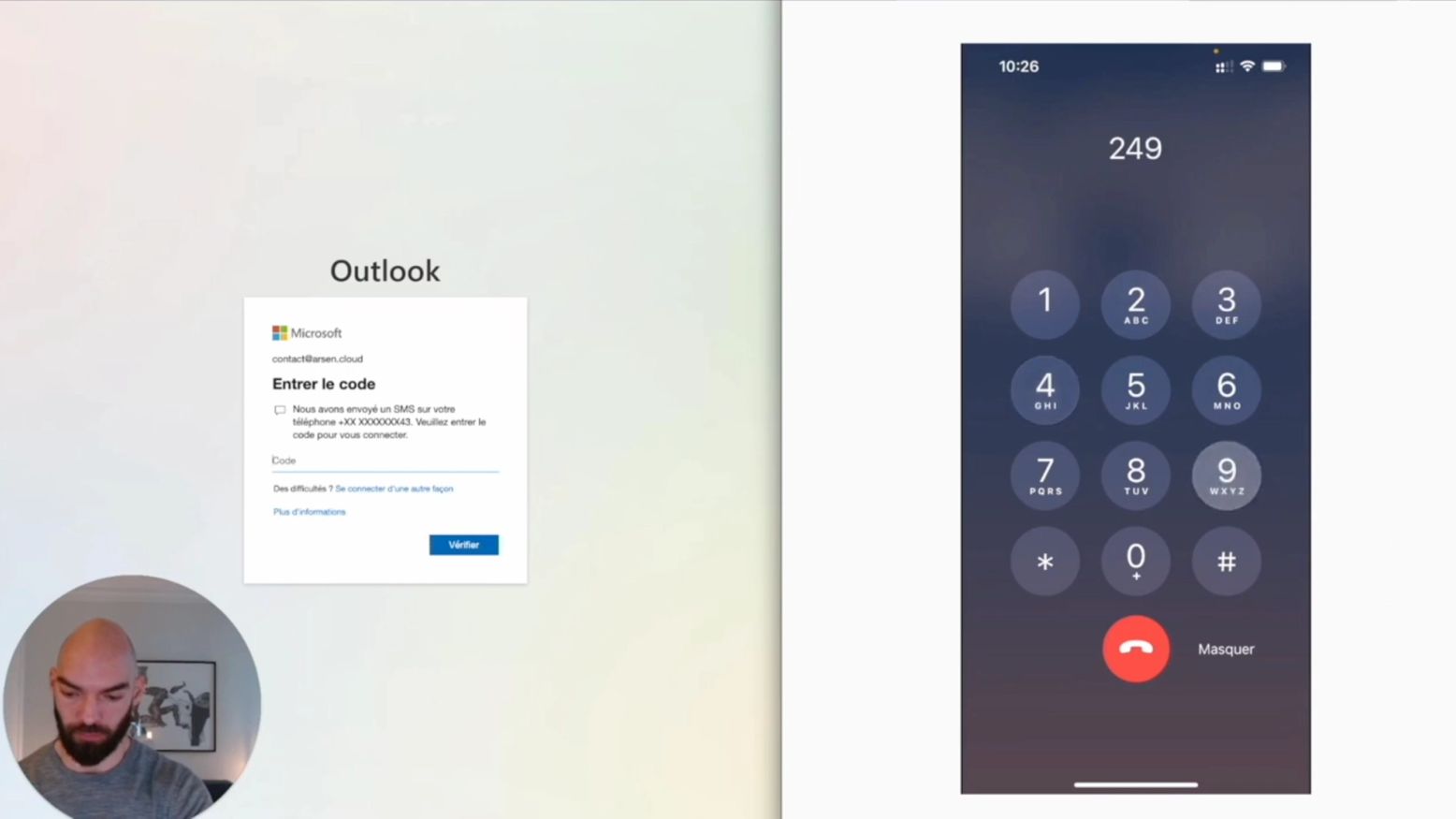
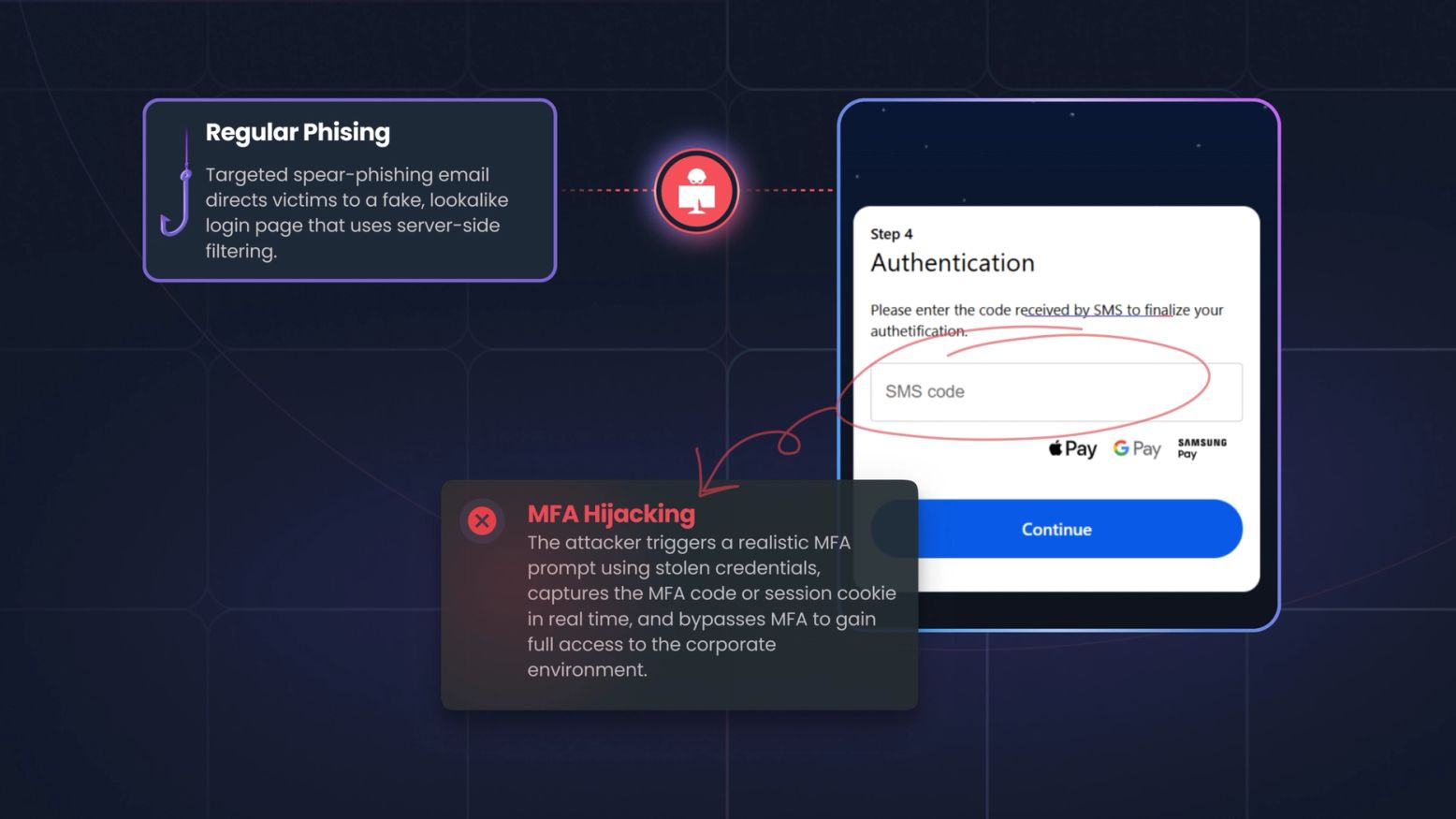
Phishing has evolved. Zscaler ThreatLabz recently revealed BlackForce, a toolkit hijacking active sessions and bypassing MFA, using the "Man-in-the-Middle" (MITM ) attack tactic. CISOs must update strategies, moving beyond simple awareness to defending against real-time,...